CVE-2024-10914: Critical Flaw in D-Link NAS Devices Actively Exploited, No Patch!
A critical command injection vulnerability (CVE-2024-10914) impacting numerous end-of-life D-Link network-attached storage (NAS) devices is currently under active exploitation. This vulnerability, assigned a CVSSv3 score of 9.2, poses a significant threat to organizations and individuals utilizing these devices, as successful exploitation can lead to complete system compromise.
Vulnerability Analysis
CVE-2024-10914 resides within the cgi_user_add command due to insufficient sanitization of the “name” parameter. This allows unauthenticated attackers to inject arbitrary shell commands via specifically crafted HTTP GET requests. Security researcher Netsecfish has published a detailed technical analysis of the vulnerability, including proof-of-concept exploit code utilizing the following command structure:
This exploit leverages the vulnerable parameter to inject and execute malicious commands within the targeted NAS device.
Scope of Impact
The vulnerability affects the following D-Link NAS models:
- DNS-320 Version 1.00
- DNS-320LW Version 1.01.0914.2012
- DNS-325 Version 1.01, Version 1.02
- DNS-340L Version 1.08
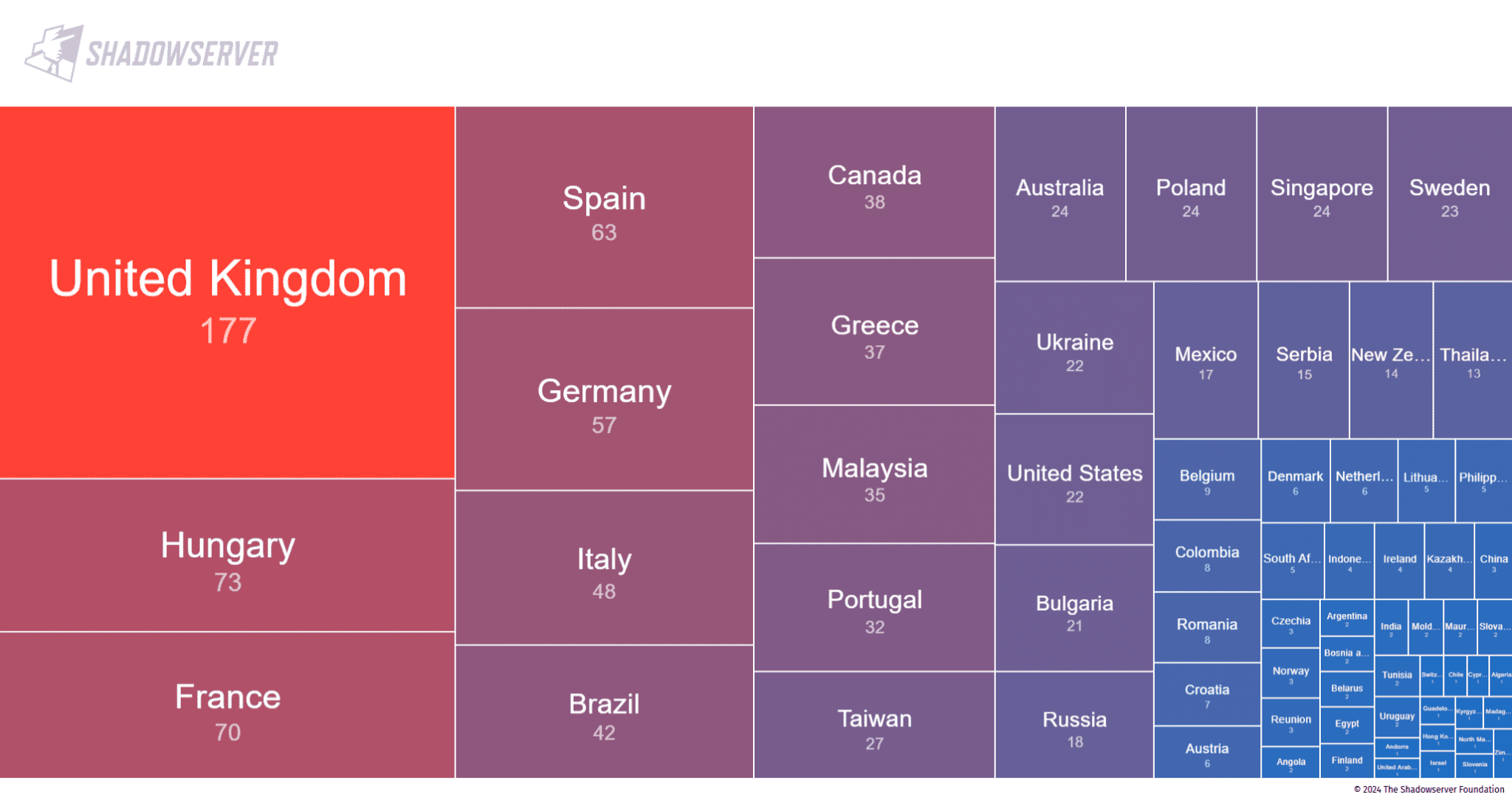
Netsecfish’s research identified over 60,000 potentially vulnerable devices exposed on the internet. Furthermore, the Shadowserver Foundation has reported observing active exploitation attempts targeting these devices since November 12th, with nearly 1,100 devices confirmed as exposed.
We have observed D-Link NAS CVE-2024-10914 /cgi-bin/account_mgr.cgi command injection exploitation attempts starting Nov 12th. This vuln affects EOL/EOS devices, which should be removed from the Internet: https://t.co/o2BsBwkIlI
We see ~1100 exposed.https://t.co/0ZhIHSXqVZ pic.twitter.com/YB6c11LKU5
— The Shadowserver Foundation (@Shadowserver) November 13, 2024
Mitigation Strategies
D-Link has officially confirmed that no patch will be released for CVE-2024-10914 due to the end-of-life status of the affected devices. In light of this, immediate mitigation is crucial. D-Link strongly recommends retiring vulnerable devices. If immediate retirement is not feasible, the following measures are critical:
- Network Isolation: Isolate the affected devices from the public internet to prevent external access.
- Access Control: Implement strict access control measures, limiting device access to authorized personnel only.
Related Posts:
- CVE-2024-10914 (CVSS 9.2): Command Injection Flaw Threatens 61,000+ D-Link NAS Devices
- APT organization steals D-Link company digital certificate to sign its malware
- D-Link router and modem vulnerabilities are being exploited by Satori IoT botnet
- CVE-2024-3273: D-Link NAS Vulnerability Threatens 92,000 Devices
- Hackers Actively Exploiting Critical D-Link NAS Vulnerability: 90,000+ Devices at Risk