CVE-2024-3273: D-Link NAS Vulnerability Threatens 92,000 Devices
Security researchers have uncovered a serious vulnerability in several D-Link Network Attached Storage (NAS) devices, including DNS-320L, DNS-327L, and others. This flaw leaves devices wide open to attack, giving hackers the ability to execute commands remotely and potentially steal sensitive data or disrupt operations.
The Double Whammy: Backdoor and Injection
The vulnerability (CVE-2024-3273, CVSS 7.3) is two-fold and particularly dangerous:
- Hidden Backdoor: Hardcoded credentials within the vulnerable code allow attackers to bypass authentication and gain access to the device.
- Command Injection: A flaw in how the NAS handles requests allows hackers to inject malicious commands through the ‘system’ parameter, granting them remote control.
The Impact
Attackers exploiting this vulnerability could:
- Steal Sensitive Data: Access stored files, potentially exposing confidential business information or personal data.
- Disrupt Systems: Run commands that could modify system settings or cripple services, causing downtime.
- Install Further Malware: Use the compromised device as a jumping-off point to infect other systems on the network.
Who’s At Risk?
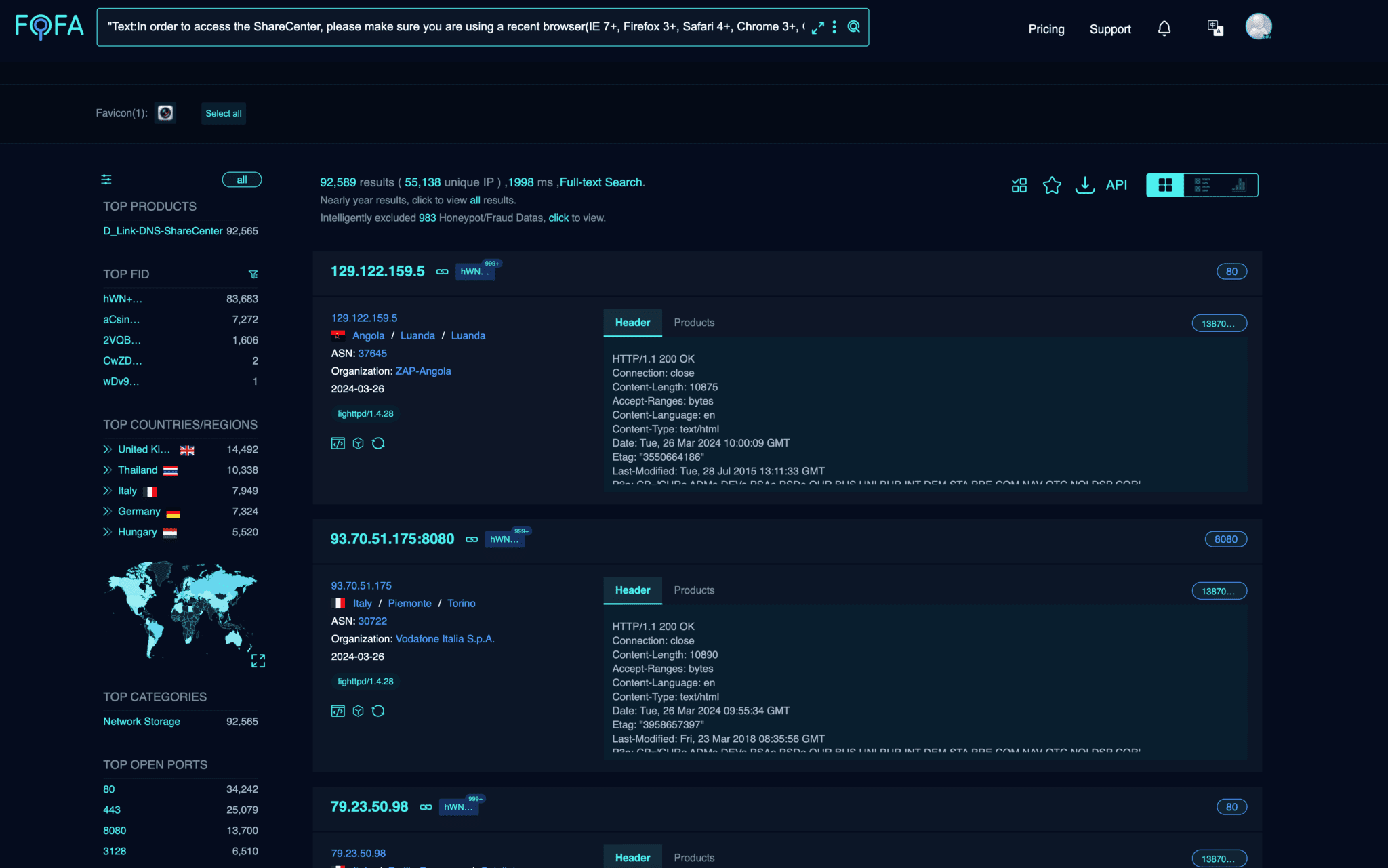
Image: netsecfish
An estimated 92,000 devices on the internet could be susceptible to attacks exploiting this vulnerability. The specific versions affected include:
- DNS-320L Versions 1.11, 1.03.0904.2013, and 1.01.0702.2013
- DNS-325 Version 1.01
- DNS-327L Versions 1.09 and 1.00.0409.2013
- DNS-340L Version 1.08
Exploitation and Consequences
Exploiting CVE-2024-3273 is alarmingly straightforward. An attacker can craft a malicious HTTP GET request targeting the vulnerable /cgi-bin/nas_sharing.cgi endpoint. This request, containing the hardcoded username and an empty password along with a base64 encoded command, can lead to unauthorized command execution.

Image: netsecfish
The implications of such an attack are far-reaching. Successful exploitation could result in unauthorized access to sensitive information, modification of system configurations, or even a total denial of service, rendering the device unusable and disrupting operations for businesses and individuals alike.
Call to Action
In response to the discovery of CVE-2024-3273, it is strongly recommended that all users of affected D-Link NAS devices promptly apply any available patches or updates provided by D-Link. Given the severity of the vulnerabilities and the potential for widespread impact, addressing this issue should be considered an immediate priority for all affected users.
Here’s what you need to do:
- Check Your Device: Visit D-Link’s website and determine if your NAS model is affected.
- Apply Updates Urgently: If your device is vulnerable, download and install the latest firmware update as soon as possible.
- Change Default Passwords: Even after patching, it’s good practice to change any default passwords on your NAS device.
Protect Your Data
This vulnerability underscores the need to remain vigilant about cybersecurity, even with trusted devices. Stay informed about security updates, use strong passwords, and consider additional security measures like network segmentation to reduce your risk.







