Category: Sniffing & Spoofing
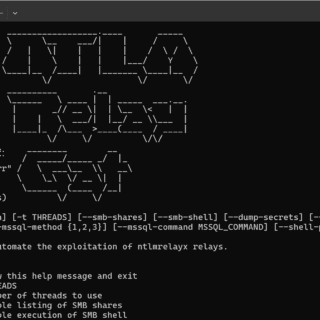
NTLM Relay Gat NTLM Relay Gat is a powerful tool designed to automate the exploitation of NTLM relays using ntlmrelayx.py from the Impacket tool suite. By leveraging the capabilities of ntlmrelayx.py, NTLM Relay Gat streamlines...
Above Invisible protocol sniffer for finding vulnerabilities in the network. Designed for pentesters and security professionals. Mechanics Above is an invisible network sniffer for finding vulnerabilities in network equipment. It is based entirely on...
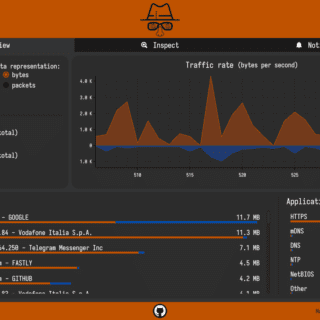
sniffnet Sniffnet is a network monitoring tool to help you easily keep track of your Internet traffic. Sniffnet is a technical tool, but at the same time it strongly focuses on the overall user experience: most of...
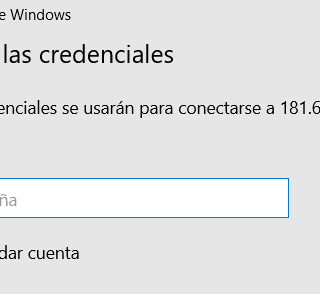
RDPCredentialStealer RDPCredentialStealer it’s malware that steals credentials provided by users in RDP using API Hooking with Detours in C++. Code RDPCredStealerDLL: This code is an implementation of a hooking technique in C++ using the...
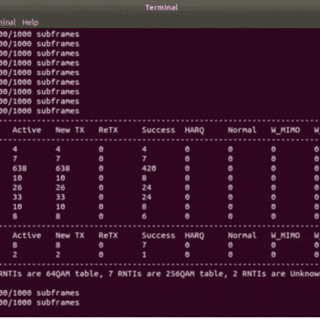
LTESniffer – An Open-source LTE Downlink/Uplink Eavesdropper LTESniffer is An Open-source LTE Downlink/Uplink Eavesdropper It first decodes the Physical Downlink Control Channel (PDCCH) to obtain the Downlink Control Informations (DCIs) and Radio Network Temporary Identifiers...
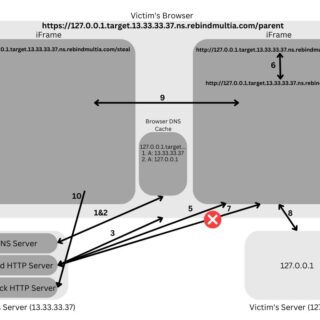
rebindMultiA rebindMultiA is a tool to perform a Multiple A Record rebind attack. rebindmultia.com is a domain that I’ve set up to assist with these attacks. It makes every IP its own authoritative nameserver for the...
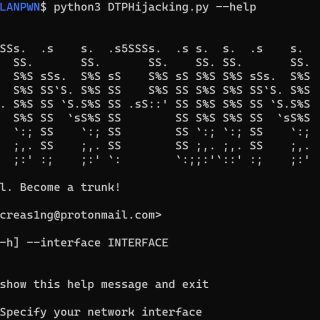
VLANPWN VLAN attacks toolkit DoubleTagging.py – This tool is designed to carry out a VLAN Hopping attack. VLAN hopping is a computer security exploit, a method of attacking networked resources on a virtual LAN...
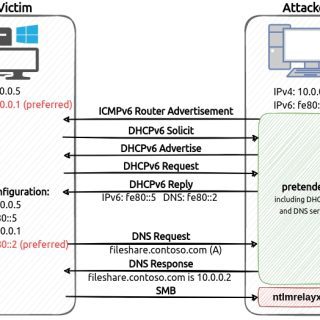
pretender pretender is a tool developed by RedTeam Pentesting to obtain machine-in-the-middle positions via spoofed local name resolution and DHCPv6 DNS takeover attacks. pretender primarily targets Windows hosts, as it is intended to be used...
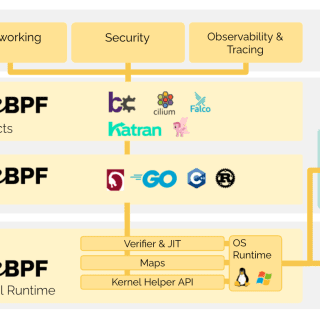
peetch peetch is a collection of tools aimed at experimenting with different aspects of eBPF to bypass TLS protocol protections. Currently, peetch includes two subcommands. The first called dump aims to sniff network traffic...
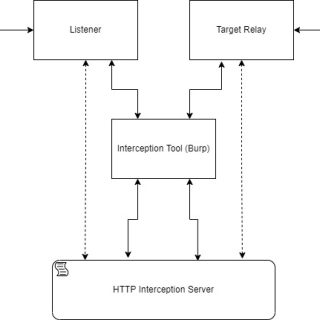
MITM Intercept A little bit less hackish way to intercept and modify non-HTTP protocols through Burp and others with SSL and TLS interception support. This tool is for researchers and applicative penetration testers that...
SMB Session Spoofing This is a utility that can be compiled with Visual Studio 2019 (or newer). The goal of this program is to create a fake SMB Session. The primary purpose of this...
Xepor Xepor (pronounced /ˈzɛfə/, zephyr), is a web routing framework for reverse engineers and security researchers. It provides a Flask-like API for hackers to intercept and modify HTTP request and/or HTTP response in a human-friendly coding...
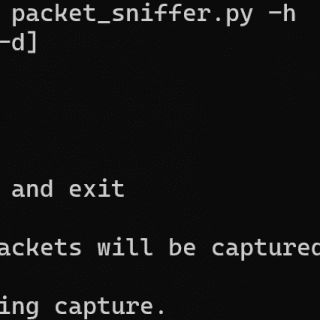
Python 3 Network Packet Sniffer A simple pure-Python network packet sniffer. Packets are disassembled as they arrive at a given network interface controller and their information is displayed on the screen. This application maintains...
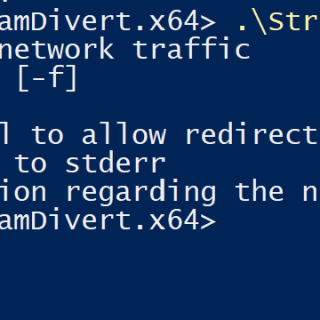
StreamDivert StreamDivert is a tool to man-in-the-middle or relay in and outgoing network connections on a system. It has the ability to, for example, relay all incoming SMB connections to port 445 to another...
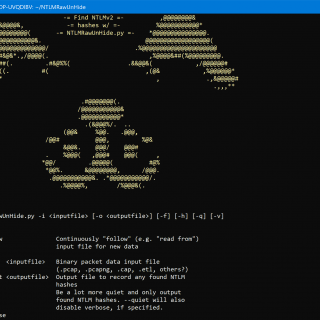
NTLMRawUnhide.py NTLMRawUnhide.py is a Python3 script designed to parse network packet capture files and extract NTLMv2 hashes in a crackable format. The tool was developed to extract NTLMv2 hashes from files generated by native...