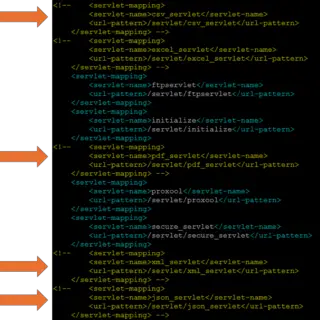
1Panel Users Urged to Patch After Critical SQLi Flaws (CVE-2024-39911, CVSS 10) Discovered
A critical SQL injection vulnerability, collectively endangering millions of Linux servers worldwide found in the popular open-source server management tool, 1Panel. Identified as CVE-2024-39911, this SQL injection flaw, carries a maximum CVSS score of...