Kali Linux 2024.2 Released: An Upgrade for the Penetration Tester’s Arsenal
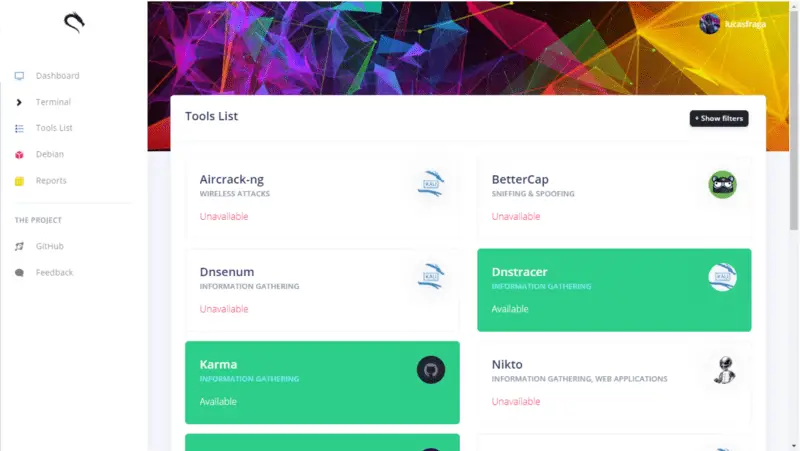
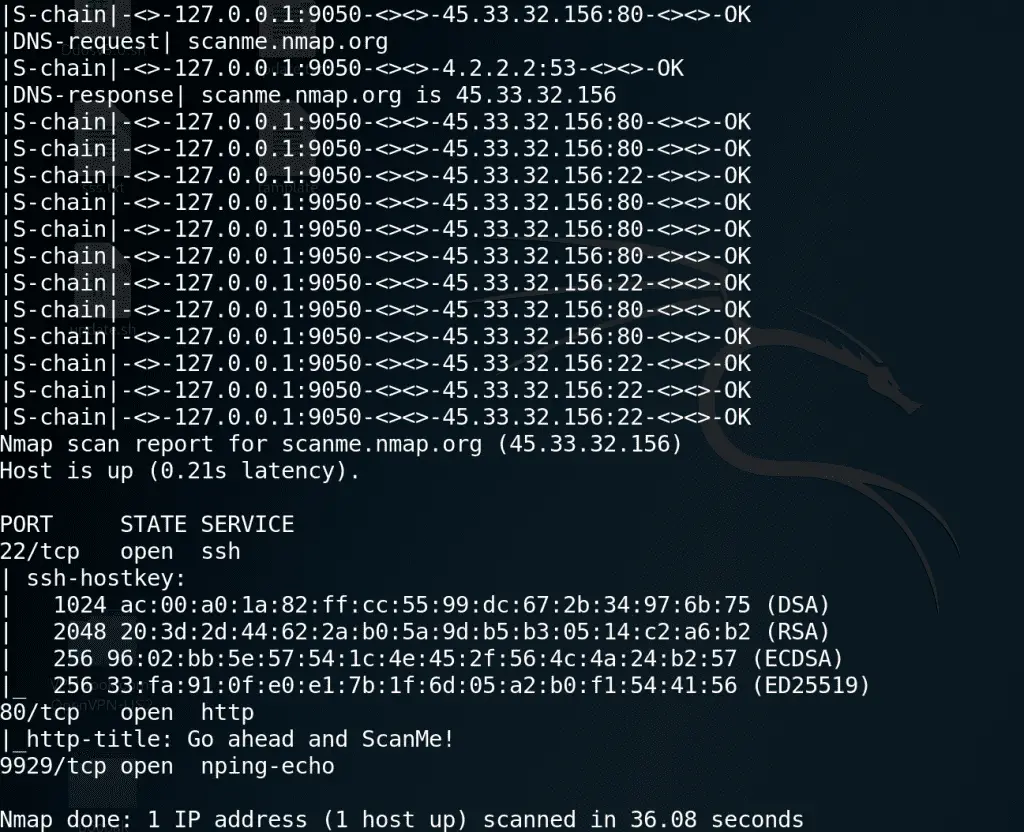
Kali Linux, the renowned open-source, Debian-based Linux distribution, has officially released its latest version, Kali Linux 2024.2 This highly anticipated update, though slightly delayed, packs a punch with a plethora...