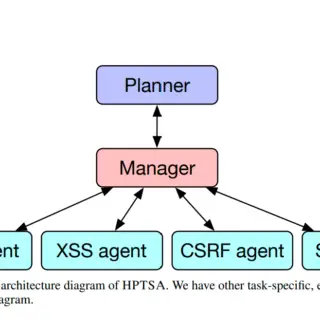
AI Agents Exploit Zero-Day Vulnerabilities with 53% Success
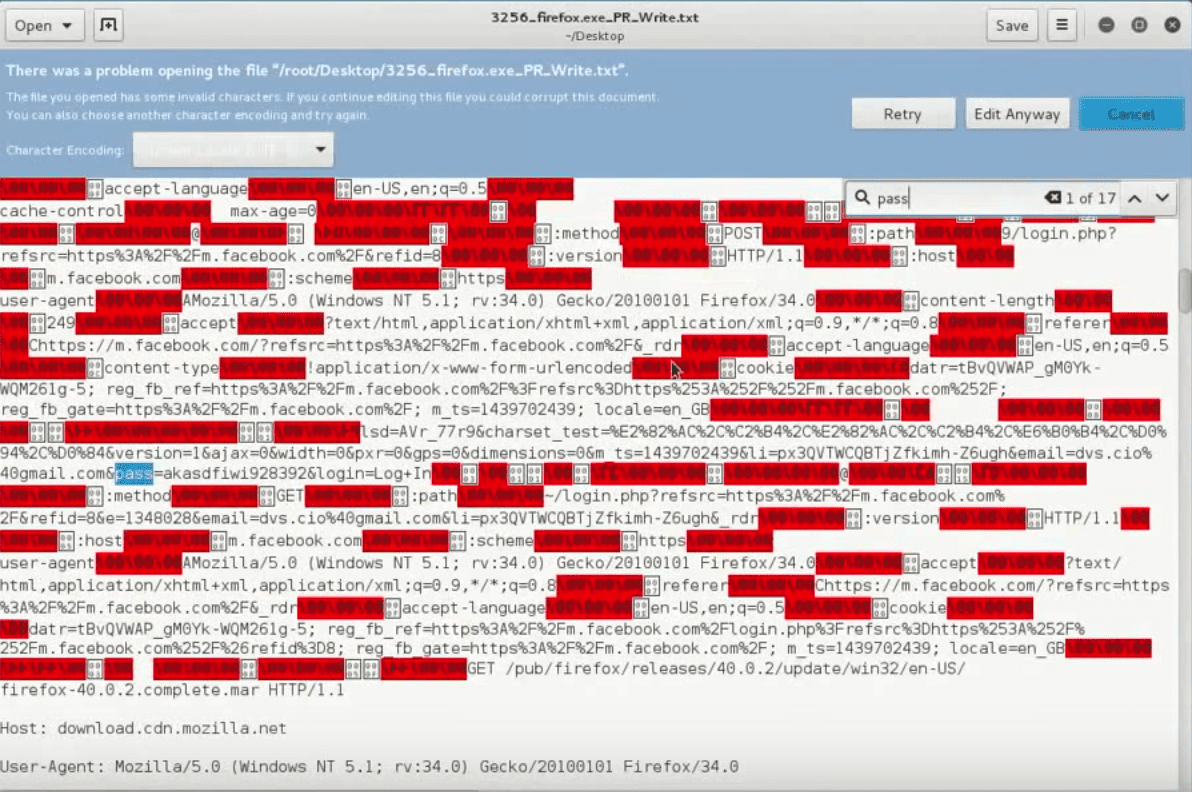
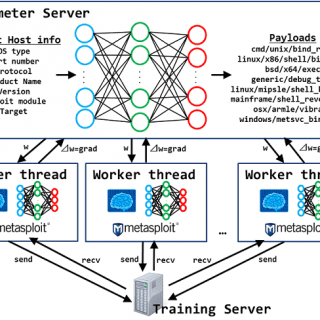
In a groundbreaking development, researchers at the University of Illinois Urbana-Champaign have demonstrated that teams of AI agents, powered by large language models (LLMs), can successfully exploit zero-day vulnerabilities. These are previously unknown and...