Deep Exploit: Fully automatic penetration test tool using Machine Learning
Deep Exploit
Fully automatic penetration test tool using Machine Learning.
Deep Exploit is fully automated penetration tool linked with Metasploit.
Deep Exploit has two exploitation modes.
- Intelligence mode
Deep Exploit identifies the status of all opened ports on the target server and executes the exploit at pinpoint based on past experience (trained result). - Brute force mode
Deep Exploit executes exploits using all combinations of “exploit module”, “target” and “payload” corresponding to a user’s indicated product name and port number.
Deep Exploit’s key features are following.
- Efficiently execute exploit.
If “intelligence mode”, Deep Exploit can execute exploits at pinpoint (minimum 1 attempt).
If “Brute force mode”, Deep Exploit can execute exploits thoroughly corresponding to user’s indicated product name and port number. - Deep penetration.
If Deep Exploit succeeds the exploit to the target server, it further executes the exploit to other internal servers. - Operation is very easy.
Your only operation is to input one command.
It is very easy!! - Self-learning.
Deep Exploit doesn’t need the “learning data”.
Deep Exploit can learn how to method of exploitation by itself (uses reinforcement learning). - Learning time is very fast.
Deep Exploit uses distributed learning by multi-agents.
So, we adopted an advanced machine learning model called A3C.
Current Deep Exploit’s version is a beta.
But, it can automatically execute following actions:
- Intelligence gathering.
- Threat Modeling.
- Vulnerability analysis.
- Exploitation.
- Post-Exploitation.
- Reporting.
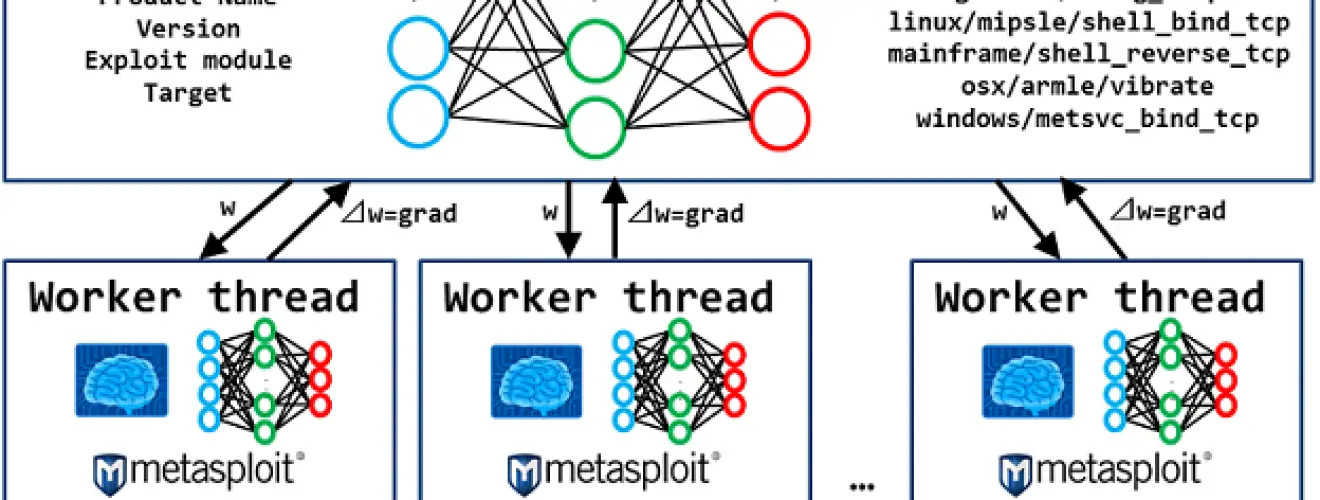
System component.
Processing flow
Intelligence mode
Step 1. Port scan the target server.
Deep Exploit executes the port scanning using Nmap for gathering target server’s information.
After, Deep Exploit executes two Metasploit’s command (hosts and services) via RPC API.
- ex) result of hosts command.
Deep Exploit gets OS type from a result of hosts command. In above example, Deep Exploit gets OS type as Linux.
- ex) result of services command.
Deep Exploit gets port numbers, protocol types, product name, product version from the result of port scanning.
In above example, Deep Exploit gets port number as 21, protocol as tcp, product as vsftpd, version as 2.3.4
Step 2. Exploit using Metasploit for training.
Deep Exploit learns how to method of exploitation using advanced machine learning model called A3C.
So, Deep Exploit uses vulnerable servers such as metasploitable2, owaspbwa for learning.
- vulnerable servers (one example)
metasploitable2
metasploitable3
others
Step 3. Exploit using Metasploit for testing.
Step 4. Post exploit.
Step 5. Generate report.
Deep Exploit generates a report that summarizes vulnerabilities.
Report’s style is html.
Brute force mode
Usage
Demo
Copyright 2018 Isao Takaesu
Source: https://github.com/13o-bbr-bbq/machine_learning_security/tree/master/
Suggest reading:
- Tired of Viruses in your Android Phone? Check out the best Android virus cleaner.
- A guide on how to choose webhosting in the UK










