pecoret: A Pentest Collaboration and Reporting Tool
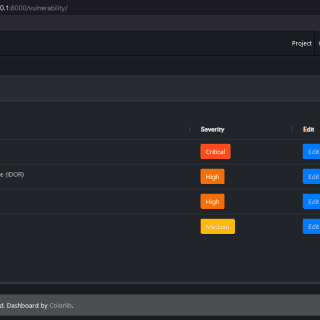
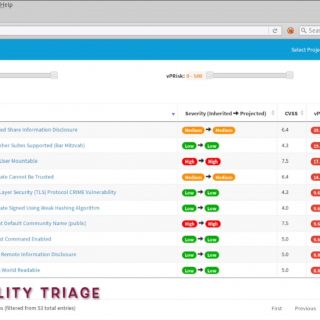
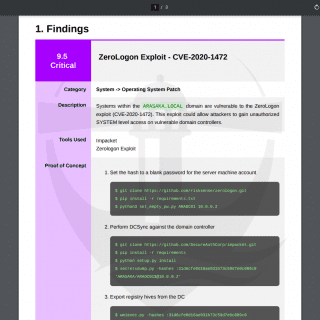
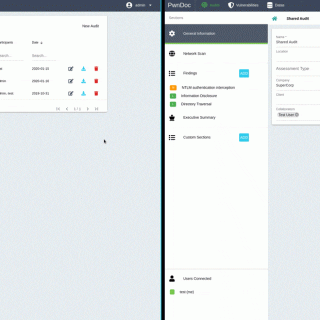
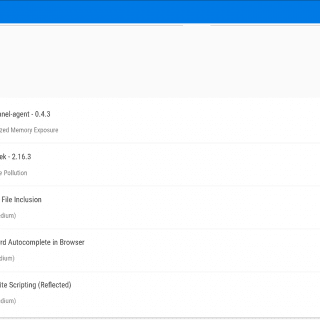
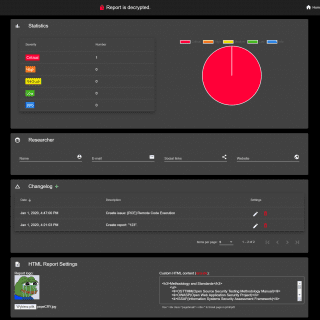
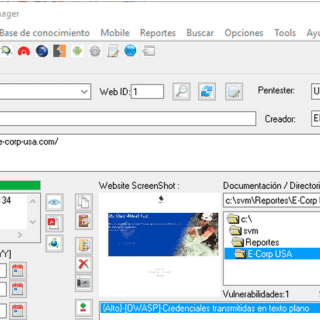
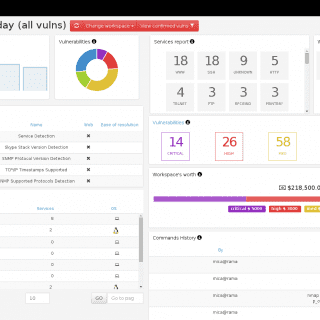
PeCoReT PeCoReT (Pentest Collaboration and Reporting Tool) is an open-source application to manage your pentest projects. PeCoReT allows pentesters to focus on testing instead of writing the report. It can be customized and once...