Faraday v5.3 released: Open Source Vulnerability Manager
Faraday – Open Source Vulnerability Manager
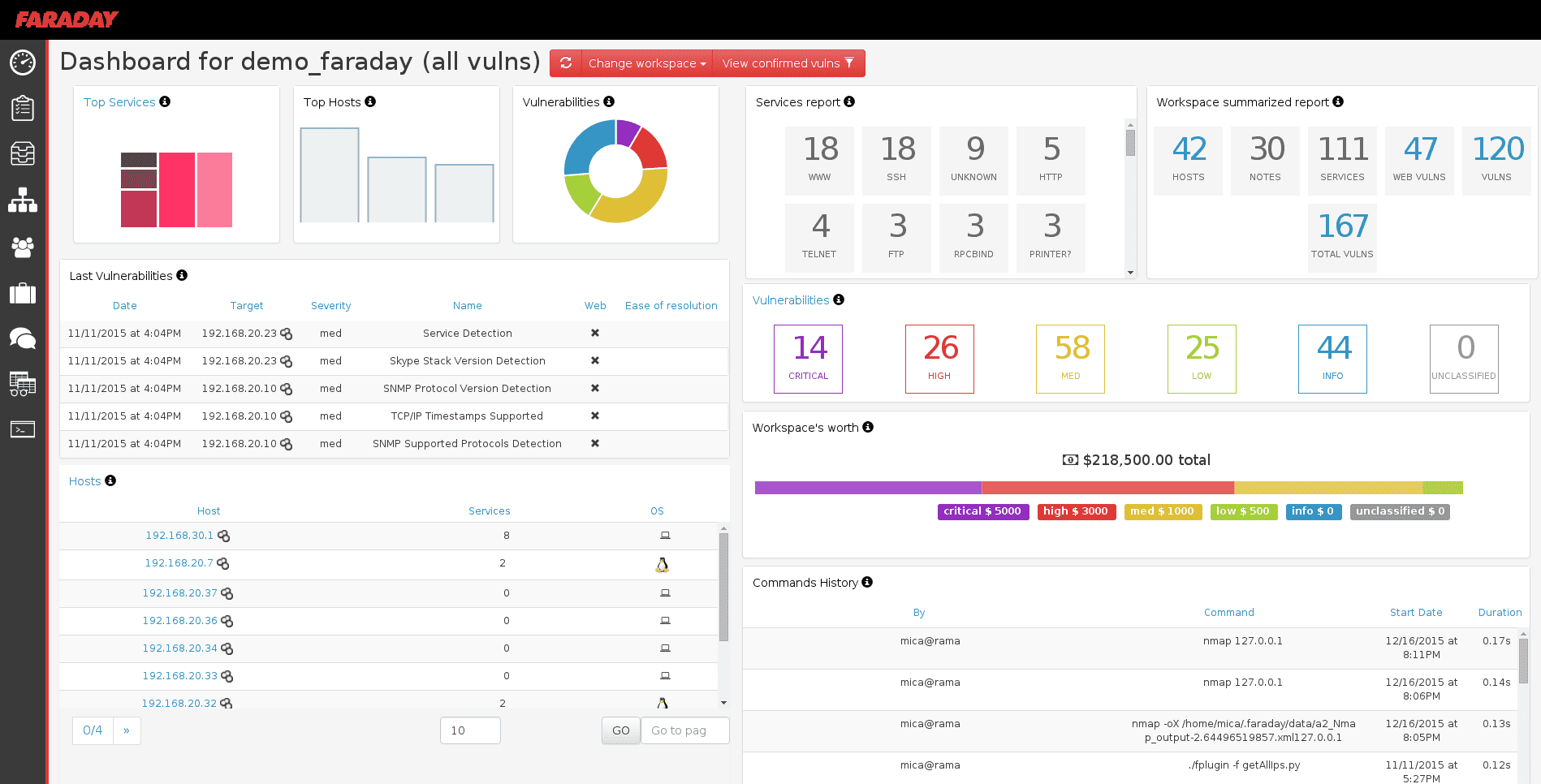
Faraday introduces a new concept – IPE (Integrated Penetration-Test Environment) a multiuser Penetration test IDE. Designed for distribution, indexation, and analysis of the data generated during a security audit.
Security has two difficult tasks: designing smart ways of getting new information and keeping track of findings to improve remediation efforts. With Faraday, you may focus on discovering vulnerabilities while we help you with the rest. Just use it in your terminal and get your work organized on the run. Faraday was made to let you take advantage of the available tools in the community in a truly multiuser way.
Faraday aggregates and normalizes the data you load, allowing exploring it into different visualizations that are useful to managers and analysts alike.

The main purpose of Faraday is to re-use the available tools in the community to take advantage of them in a multiuser way.
Designed for simplicity, users should notice no difference between their own terminal application and the one included in Faraday. Developed with a specialized set of functionalities that help users improve their own work. Do you remember programming without an IDE? Well, Faraday does the same as an IDE does for you when programming, but from the perspective of a penetration test.
Changelog v5.3
- [MOD] Modified parameters for interactive swagger. #7610
- [ADD] Add services and host endoints that retrives all the information that the users has access. #7503
- [FIX] Revised the references fetching strategy to enhance memory usage during CSV export. #7712
- [FIX] Fixed creation of vuln from template. #7711
- [MOD] Modify version of libraries accordingly to dependabot findings. #7691
- [ADD] Add vuln endoint that retrives all the objects that the users has access. #7521
Plugins
Don’t change the way you work today! Faraday plays well with others, right now it has more than 50 supported tools, among them you will find:
There is 3 kind of plugins:
- Plugins that intercept commands, fired directly when a command is detected in the console. These are transparent to you and no additional action on your part is needed.
- Plugins that import file reports. You have to copy the report to $HOME/.faraday/report/[workspacename] (replacing [workspacename] with the actual name of your Workspace) and Faraday will automatically detect, process and add it to the HostTree.
- Plugin connectors or online (BeEF, Metasploit, Burp), these connect to external APIs or databases or talk directly to Faraday’s RPC API.
Installation & Tutorial
Source: https://github.com/infobyte/







