A critical vulnerability tracked as CVE-2025-30095 has been discovered in VyOS, a popular open-source network operating system....
ssh
A new vulnerability in JumpServer (CVE-2025-27095) has been disclosed, exposing Kubernetes clusters to potential compromise through token...
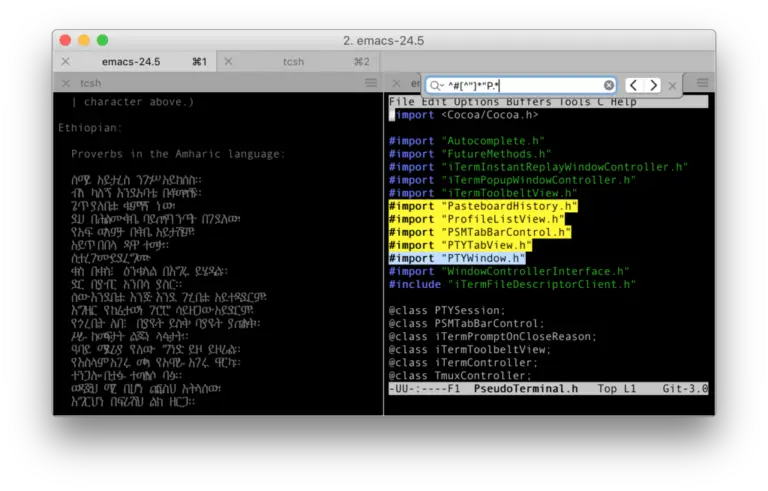
A critical security vulnerability, tracked as CVE-2025-22275 (CVSS 9.3) has been discovered and patched in iTerm2, a...
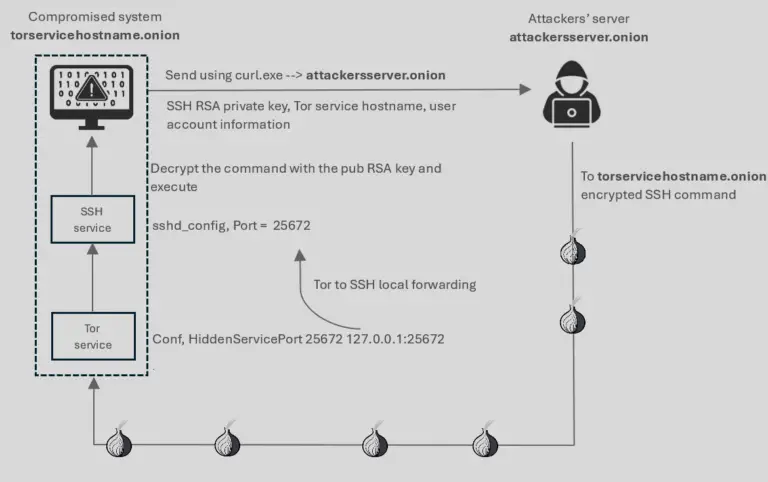
Security researcher Artem Baranov has detailed a sophisticated malware campaign targeting the Ukrainian military through a backdoor...
Wiz Threat Research revealed a new malware campaign orchestrated by the Romanian-speaking threat group Diicot, also known...
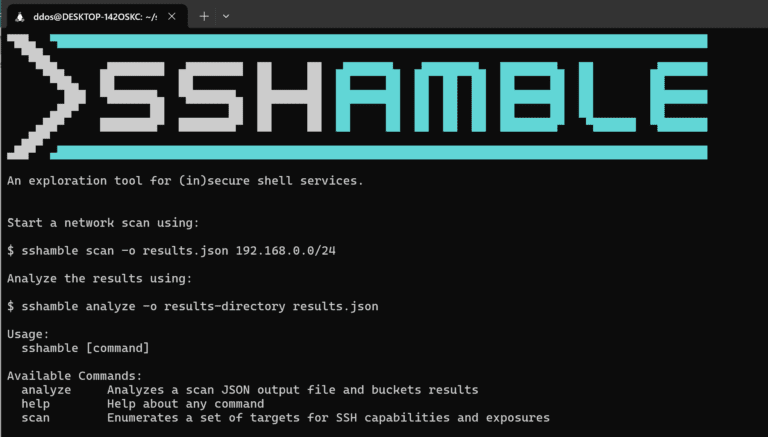
Experts at runZero have uncovered numerous vulnerabilities related to poorly secured or improperly implemented SSH services, an...
Security analysts at Sucuri have uncovered a novel attack technique targeting e-commerce websites, where cybercriminals abuse swap...
Zscaler’s ThreatLabz research team detected a formidable adversary: DreamBus. A Linux-based malware family, DreamBus has been quietly...
OpenSSH, a critical component in secure networking, has recently faced a formidable challenge. A now-patched security vulnerability,...
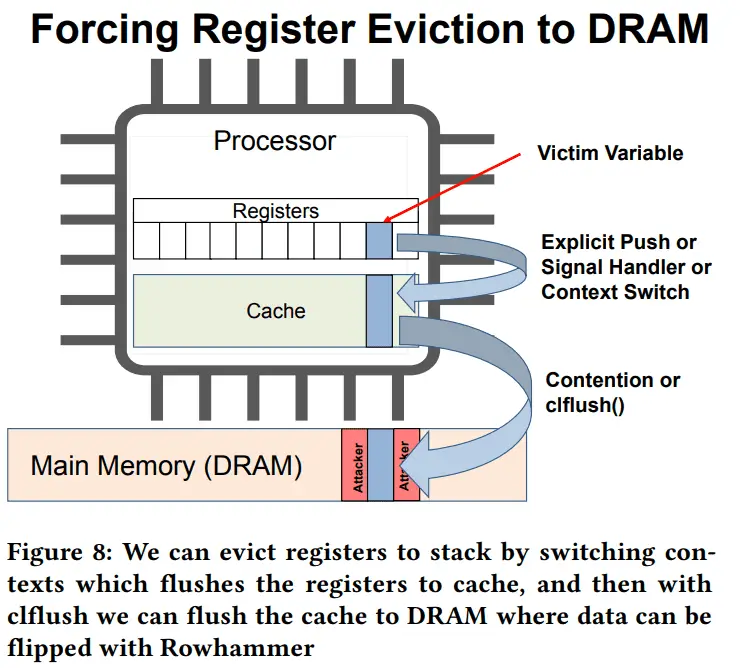
The digital realm is no stranger to ingenious exploits, and the latest breakthrough in cybersecurity research is...
SSH Short for Secure Shell, SSH (developed by SSH Communications Security Ltd.) is a secure protocol for...
Fail2Ban is an intrusion prevention software framework that protects computer servers from brute-force attacks. Written in the...