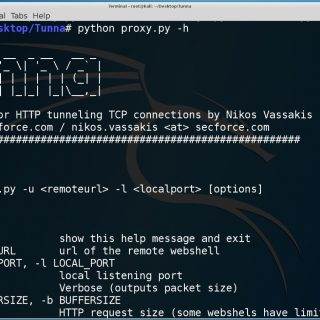
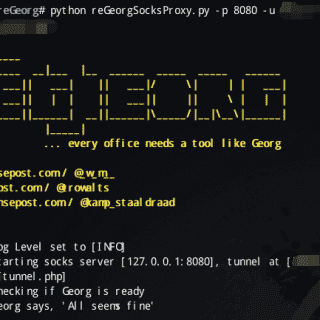
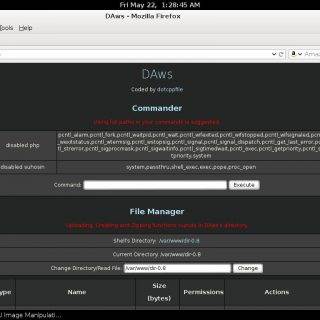
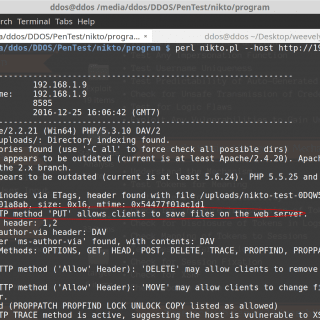
Kraken v1.2 releases: modular multi-language webshell
Kraken – a modular multi-language webshell coded by @secu_x11 Support On the one hand, Kraken is supported by different technologies and versions. The following is a list of where Kraken agents are supported: PHP...