Tagged: privilege escalation
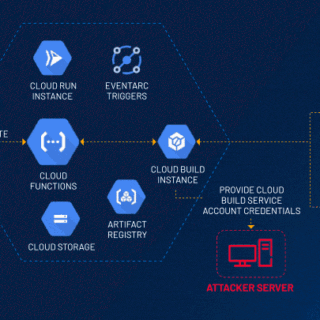
Cybersecurity researchers have uncovered a privilege escalation vulnerability in the Cloud Functions service on the Google Cloud Platform. This vulnerability, dubbed ConfusedFunction, could allow an attacker to gain unauthorized access to other services and...
OpenVPN, a leading provider of virtual private network (VPN) solutions, has refuted claims of zero-day vulnerabilities in its OpenVPN2 software, alleged to allow an attack named OVPNX. These claims, made in an announcement for...
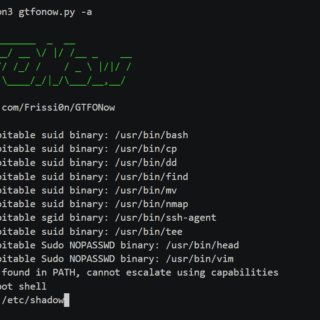
GTFONow Automatic privilege escalation on Unix systems by exploiting misconfigured setuid/setgid binaries, capabilities, and sudo permissions. Designed for CTFs but also applicable in real-world pentests. Features Automatically exploit misconfigured sudo permissions. Automatically exploit misconfigured...
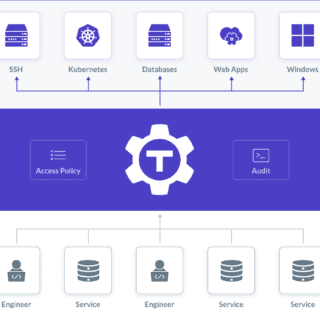
Teleport, a renowned platform offering centralized authentication and auditing for servers and cloud applications, has recently found itself in the cybersecurity spotlight. This platform, however, has multiple vulnerabilities, some of which are deemed ‘Critical‘....
On the 12th of December 2023, SAP Security Patch Day published 15 new Security Notes alongside updates to 2 previously released notes, fortifying SAP’s commitment to safeguarding its vast ecosystem against cyber threats. The...
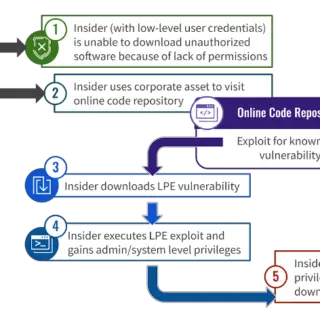
In the shadowy realm of cybersecurity, a new predator emerges from within, turning the very defenses meant to protect into weapons of betrayal. A recent report by CrowdStrike Counter Adversary Operations and the CrowdStrike...
In the interconnected world of software and cybersecurity, even the most seemingly innocuous applications can harbor dangerous vulnerabilities. This is the story of Papercut, a widely used printing management software, and how a security...
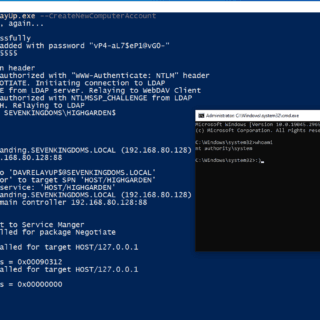
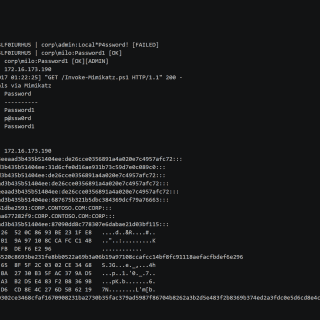
DavRelayUp A quick and dirty port of KrbRelayUp with modifications to allow for NTLM relay from webdav to LDAP in order to streamline the abuse of the following attack primitive: (Optional) New machine account creation (New-MachineAccount)...
PrivKit PrivKit is a simple beacon object file that detects privilege escalation vulnerabilities caused by misconfigurations on Windows OS. PrivKit detects the following misconfigurations Checks for Unquoted Service Paths Checks for Autologon Registry Keys...
PurplePanda This tool fetches resources from different cloud/saas applications focusing on permissions in order to identify privilege escalation paths and dangerous permissions in the cloud/saas configurations. Note that PurplePanda searches both privileges escalation paths within a platform...
Here you will find privilege escalation tools for Windows and Linux/Unix* (in some near future also for Mac). These tools search for possible local privilege escalation paths that you could exploit and print them to you with nice colors so...
uptux Privilege escalation checks for Linux systemd. This tool checks for issues on Linux systems that may lead to privilege escalation. The core focus in on systemd configuration. This tool is under active development...
portia Portia aims to automate a number of techniques commonly performed on internal network penetration tests after a low privileged account has been compromised Privilege escalation Lateral movement Convenience modules Portia is a genus...
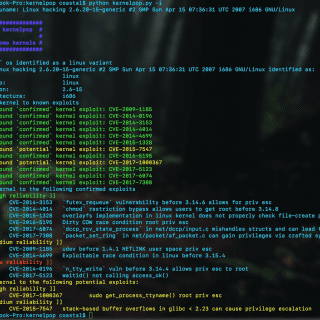
kernelpop kernelpop is a framework for performing automated kernel vulnerability enumeration and exploitation on the following operating systems: Linux Mac It is designed to be python version-agnostic, meaning that it should work with both python2 and python3 currently supported...
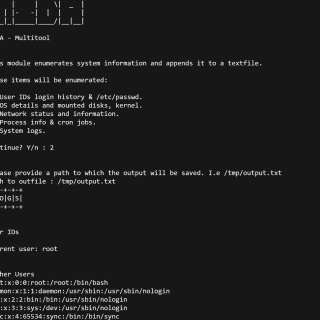
MIDA-Multitool – Bash script purposed for system enumeration, vulnerability identification, and privilege escalation.MIDA Multitool draws functionality from several of my previous scripts namely SysEnum and RootHelper and is in many regards RootHelpers successor. Besides functionality from these two previous...