A critical vulnerability in the open-source file-sharing web application ProjectSend, identified as CVE-2024-11680, is being actively exploited in the wild, according to a report by VulnCheck. Despite a patch being available since May 2023, an alarming 99% of ProjectSend instances remain unpatched, leaving them vulnerable to exploitation.
ProjectSend is a moderately popular platform, with over 4,000 instances indexed on Censys and close to 1,500 GitHub stars. The vulnerability, rated CVSS 9.8, allows attackers to alter server settings, enable unauthorized user registration, upload malicious web shells, and potentially inject harmful JavaScript. VulnCheck noted, “We are likely in the ‘attackers installing webshells’ territory,” highlighting the severe potential for abuse.
Exploitation began before the CVE assignment, with public tools such as Nuclei templates and a Metasploit module enabling attackers to test and exploit vulnerable instances. VulnCheck observed a unique hallmark of the attack: “Public-facing ProjectSend servers had started to change their landing page titles to long, random-ish strings,” a result of the tools’ testing methods.
The attack chain often progresses to enabling user registration—a non-default setting that provides attackers with post-authentication privileges. VulnCheck reported, “Given how widespread we are seeing this setting enabled, this is likely a bigger problem than ‘researchers intrusively checking for vulnerable versions.’”
Using data from Shodan, VulnCheck revealed that only 1% of ProjectSend instances are running the patched version (r1750). Most servers are still using older versions, such as r1605 from October 2022, which remains vulnerable to exploitation. The report warned, “Exploitation is likely widespread. And if not now, then in the near future considering the abysmal patching rates.”
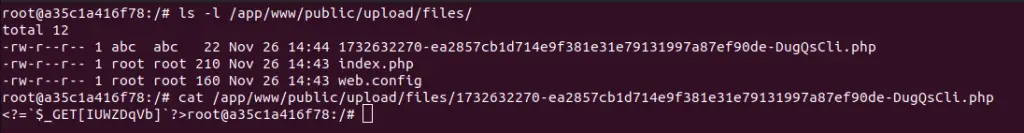
Attackers often leave traces, such as webshells uploaded to predictable locations within the upload/files/ directory, with filenames incorporating timestamps and SHA1 hashes. VulnCheck advised administrators to review server access logs for direct access to these directories to detect potential breaches.
Given the severity of CVE-2024-11680 and its ongoing exploitation, immediate action is essential. Organizations using ProjectSend should:
- Apply the Patch: Update to version r1750 or higher to mitigate the vulnerability.
- Audit Access Logs: Check for unauthorized changes or webshell uploads.
- Disable Unnecessary Features: Ensure user registration is disabled unless explicitly required.
- Monitor for Exploitation: Use tools to scan for anomalous activity on public-facing servers.
As VulnCheck concluded, “With the CVE now assigned and evidence of ongoing exploitation, it is crucial for security companies to assess their customers’ exposure, implement necessary remediations, and conduct incident response activities as needed.”
Related Posts:
- Researchers Disclose MikroTik RouterOS Security Flaw, Putting Hundreds of Thousands of Devices at Risk
- Facebook Launches Data Abuse Bounty Program