CVE-2024-1317: Critical WordPress Plugin Flaw Leaves Your Data Exposed
A serious vulnerability jeopardizes the security of WordPress websites using the popular RSS Aggregator by the Feedzy plugin. With over 50,000 active installations, WordPress users must understand the risks and take immediate action. Versions of the plugin up to 4.4.2 contain a critical SQL injection flaw that puts your sensitive information at the mercy of cybercriminals.
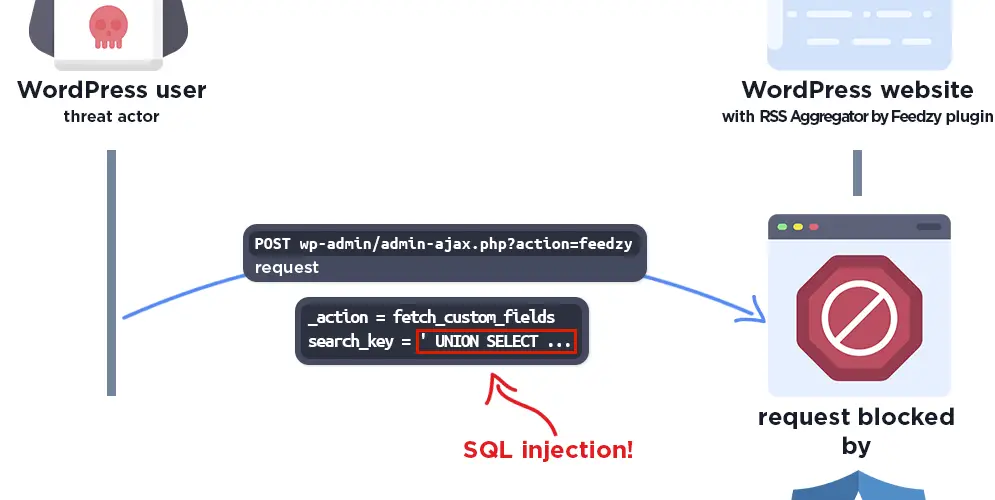
Tracked as CVE-2024-1317 (CVSS 8.8), this flaw was pinpointed within all versions up to and including 4.4.2 of the Feedzy plugin. The ‘search_key‘ parameter, a gateway through which SQL queries whisper secrets to the database, was left inadequately guarded. Insufficient escaping of user-supplied parameters and a lack of preparation in the SQL queries themselves opened the floodgates for authenticated attackers with contributor-level permissions or higher to inject malicious SQL, siphoning off data including password hashes.

Image: Wordfence
The allure of Feedzy lies in its versatility, offering features ranging from feed to post conversions, import capabilities, and RSS feed displays, making it a prized tool for content-rich sites. Yet, this allure turned perilous due to the misuse of the wpdb prepare() function, a safeguard against the SQL injection attack.
Diving deeper, it was discovered that the plugin’s fetch_custom_fields() function in the Feedzy_Rss_Feeds_Import class could be manipulated via the ‘search_key’ parameter, designed to trawl through postmeta keys. The removal of WordPress’s global default magic quotes protection by the filter_input() function with FILTER_UNSAFE_RAW further weakened its defenses.
In a typical scenario, the prepare() function would act as a diligent gatekeeper, parameterizing and escaping the SQL query to ward off injection attempts. However, in this case, the $like value was directly appended to the query, bypassing this critical defense mechanism.
The vulnerability was initially presented as a time-based blind SQL injection, a method requiring patience as attackers probe the database. However, a more alarming revelation was the possibility of UNION-based SQL injection, allowing attackers to swiftly glean information.
CVE-2024-1317 was reported to the Wordfence Bug Bounty Program on February 1, 2024, by the researcher Lucio Sá. Swift communication ensued with Themeisle, the developers behind Feedzy, culminating in the release of a patch on February 9, 2024. Version 4.4.3 fixes the vulnerability. Update now – this can’t wait!






