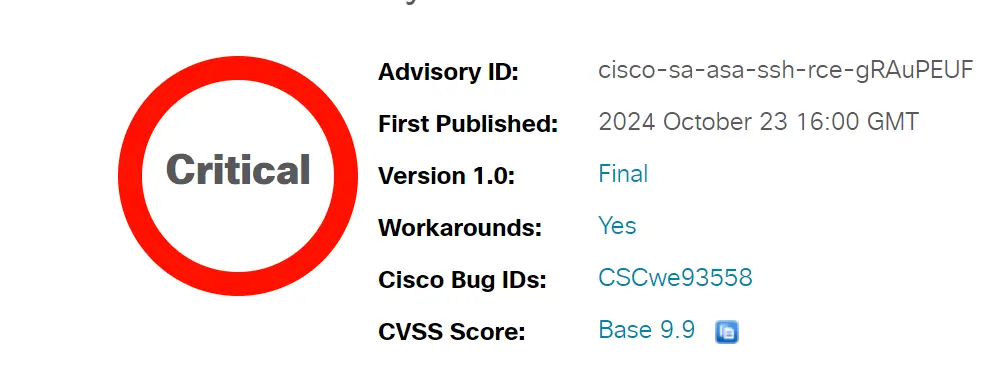
Cisco has issued a critical security advisory warning of a vulnerability in the SSH subsystem of its Adaptive Security Appliance (ASA) Software. This vulnerability, tracked as CVE-2024-20329 and assigned a CVSS score of 9.9, could allow an authenticated, remote attacker to execute commands with root privileges, effectively taking complete control of the affected system.
The vulnerability stems from “insufficient validation of user input,” according to the advisory. An attacker could exploit this flaw by “submitting crafted input when executing remote CLI commands over SSH.” This means that even users with limited privileges could potentially escalate their access and gain full control.
“A successful exploit could allow the attacker to execute commands on the underlying operating system with root-level privileges. An attacker with limited user privileges could use this vulnerability to gain complete control over the system.” Cisco’s advisory states.
Affected Products:
This vulnerability impacts Cisco ASA devices running vulnerable software versions with the CiscoSSH stack enabled and SSH access permitted on at least one interface. To determine if your device is at risk, Cisco recommends using the following command:
show running-config | include ssh
If the output includes the line “ssh stack ciscossh,” your device may be vulnerable.
Mitigation:
Cisco has released software updates to address this vulnerability and urges users to upgrade to a fixed release as soon as possible.
As a workaround, Cisco suggests enabling the native SSH stack by disabling the CiscoSSH stack using the following command:
no ssh stack ciscossh
At the time of the advisory, Cisco PSIRT was not aware of any public announcements or malicious use of this vulnerability. However, given the severity of the CVE-2024-20329 flaw, it’s crucial to take immediate action to mitigate the risk.