A newly discovered high-severity security flaw (CVE-2024-22262) in the widely-used Spring Framework software could leave countless applications vulnerable to redirect and server-side request forgery (SSRF) attacks, researchers warn.

The vulnerability lies in the way Spring Framework’s UriComponentsBuilder tool handles and validates externally provided URLs. Attackers can exploit this flaw to redirect unsuspecting users to malicious websites for phishing scams or to launch attacks against internal systems.
“Applications that use UriComponentsBuilder to parse an externally provided URL (e.g. through a query parameter) AND perform validation checks on the host of the parsed URL may be vulnerable to a open redirect attack or to a SSRF attack if the URL is used after passing validation checks,” reads the security advisory.
Echoes of Previous Vulnerabilities
This latest flaw bears worrying similarities to two previous critical Spring Framework vulnerabilities, CVE-2024-22259 and CVE-2024-22243. However, security researchers emphasize that CVE-2024-22262 involves a different attack route.
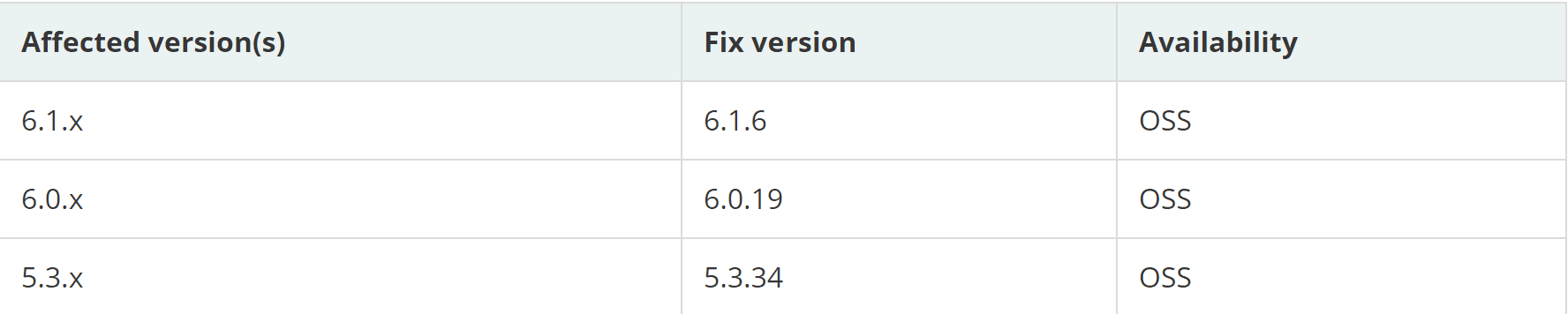
Affected Versions
The following Spring Framework versions are confirmed to be vulnerable:
- 6.1.0 – 6.1.5
- 6.0.0 – 6.0.18
- 5.3.0 – 5.3.33
- Older, unsupported versions
Take Action Immediately
The Spring development team has released patches to address CVE-2024-22262. Organizations using Spring Framework are strongly urged to upgrade to the fixed versions as soon as possible.