
The Go programming language, known for its simplicity and efficiency in software development, has recently issued a crucial security advisory addressing two severe vulnerabilities. These flaws, identified in the Go environment, could potentially allow arbitrary code execution (CVE-2024-24787) and cause infinite loops (CVE-2024-24788) in DNS operations.

CVE-2024-24787 (CVSS 9.8): Arbitrary Code Execution during Build on Darwin
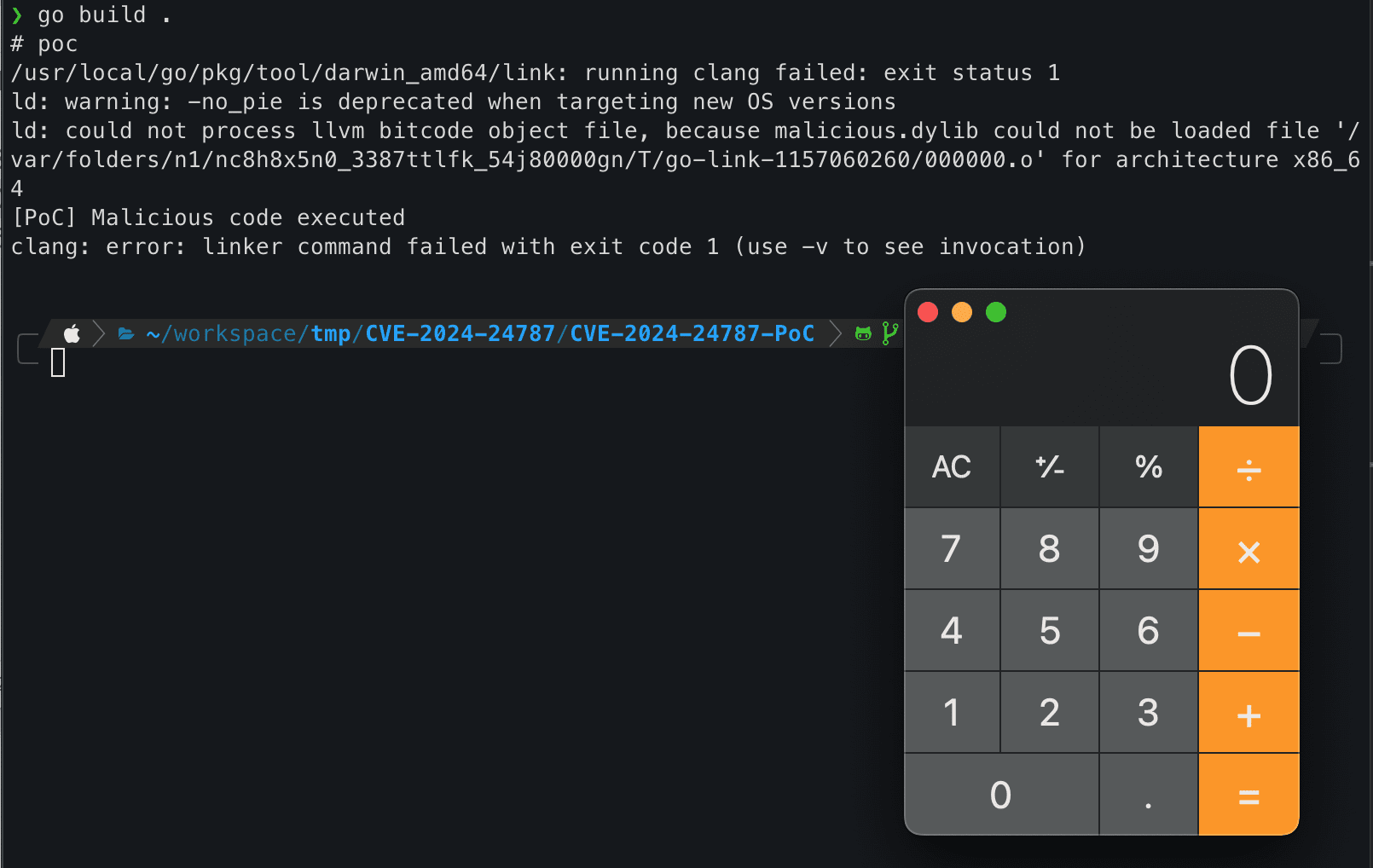
This vulnerability is specific to Darwin operating systems, where the build process of a Go module that includes CGO can inadvertently allow arbitrary code execution. The flaw stems from the misuse of the -lto_library flag in the #cgo LDFLAGS directive when using Apple’s version of the linker (ld). Traditionally, the darwin linker allows the setting of the LTO library with this flag, a method previously unchecked by Go’s “safe linker flags” verification due to its similarity to the benign -lx flag used for linking libraries. An attacker exploiting this vulnerability could load a malicious LTO library, leading to arbitrary code execution during the build process with the go build command.
Update on Friday, May 10: The proof-of-concept has been published.
CVE-2024-24788 (CVSS 7.5): Malformed DNS Message Causes Infinite Loop
This flaw lies within Go’s DNS lookup functions and centers around the potential for a malformed DNS response to crash applications or servers that rely on Go code. The crafted response can trigger an infinite loop, potentially leading to a Denial-of-Service (DoS) scenario.
Crashing services or freezing applications with the potential to deny access to resources is a significant threat, particularly for web-facing applications where uptime is crucial.
Update to Go 1.22.3 or 1.21.10 Now
All developers using Go on Darwin systems or projects utilizing Go’s DNS lookup functionality must prioritize the update to versions 1.22.3 or 1.21.10. These patched versions contain fixes that shut down the attack vectors described above.