Image: Check Point
In a recent advisory, Check Point has alerted its users to an active campaign targeting Remote Access VPN devices. Threat actors are exploiting this vulnerability to breach enterprise networks, prompting an immediate response from the cybersecurity firm.

Check Point’s Remote Access VPN is an integral feature of all Check Point network firewalls. It can be configured as a client-to-site VPN for accessing corporate networks through VPN clients or set up as an SSL VPN Portal for web-based access. However, the current wave of attacks focuses on security gateways using outdated local accounts with insecure password-only authentication methods. These attacks exploit vulnerabilities that could potentially allow unauthorized access to sensitive information on internet-connected gateways with remote access VPN or mobile access enabled.
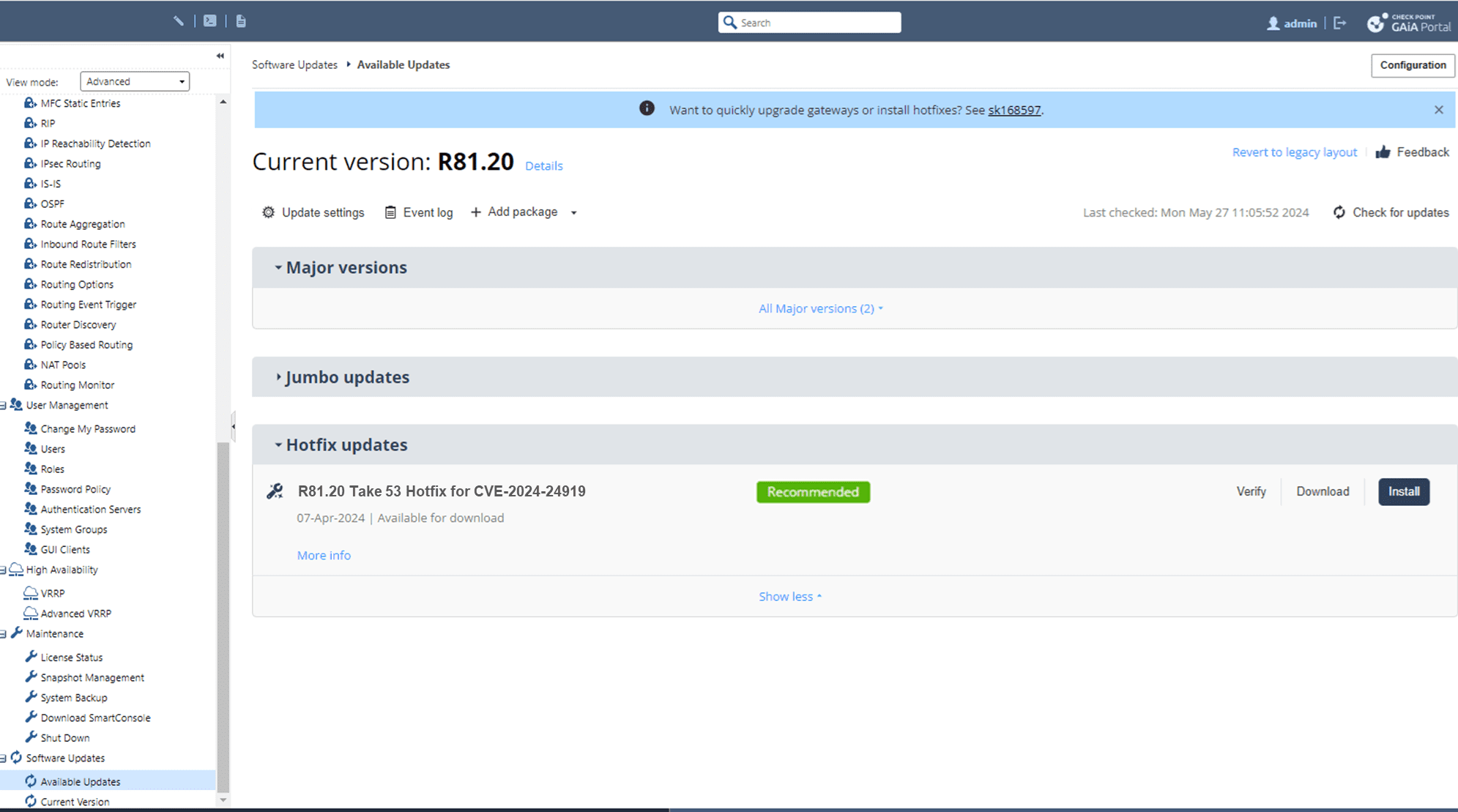
The vulnerability, tracked as CVE-2024-24919, has been assigned a CVSS score of 7.5, indicating high severity. This vulnerability could allow attackers to read certain information on compromised gateways. The primary targets have been old local accounts using password-only authentication, a method that Check Point strongly advises against.
On May 24, 2024, Check Point detected a series of login attempts exploiting this weakness. By May 27, Check Point had identified the root cause and promptly released a fix. In light of these events, the company has emphasized the critical need for customers to update their systems immediately to mitigate the risk.
“We have recently witnessed compromised VPN solutions, including those of various cybersecurity vendors. In response, we have been closely monitoring attempts to gain unauthorized access to the VPNs of Check Point’s customers. As of May 24, 2024, we identified a small number of login attempts using old VPN local accounts reliant on the insecure password-only authentication method,” Check Point said.
“Today, we found the root cause for these and are now releasing a fix. To remain protected, it is mandatory for customers to install this fix on Check Point Network Security gateways,” the company added.
To defend against these ongoing attacks, Check Point has issued several recommendations:
- Update Security Gateways: Install the latest hotfix on all Check Point Network Security gateways. This update blocks local accounts from authenticating with a password alone, effectively neutralizing the vulnerability.
- Secure Authentication Methods: Change user authentication methods to more secure options, such as certificate-based authentication. Detailed instructions are provided in the company’s support document.
- Audit and Remove Vulnerable Accounts: Identify and delete vulnerable local accounts from the Security Management Server database to prevent unauthorized access.
For further information on securing your VPN and responding to unauthorized access attempts, Check Point has provided a comprehensive support article. This resource includes detailed guidance on improving VPN security and implementing the necessary fixes to protect against these exploits.