Attention users of the popular go-zero web and RPC framework! A critical vulnerability (CVE-2024-27302) has been uncovered that could allow malicious actors to bypass your carefully crafted CORS (Cross-Origin Resource Sharing) policies.
go-zero is a web and rpc framework with lots of built-in engineering practices. It was born to ensure the stability of busy services with resilience design and has been serving sites with tens of millions of users for years.

A security researcher known as cokeBeer uncovered a critical vulnerability within the framework’s Cross-Origin Resource Sharing (CORS) Filter feature. With a Common Vulnerability Scoring System (CVSS) rating of 9.1, the flaw posed a severe security risk, capable of undermining the CORS policy protections integral to web application security.
The issue lies in how go-zero handles its CORS Filter. While the isOriginAllowed function is designed to limit access to specific domains, it relies on strings.HasSuffix for verification. This opens a bypass opportunity for attackers using specially crafted domains like “evil-victim.com”.
The proof of concept (PoC) for exploiting CVE-2024-27302 is alarmingly straightforward, underscoring the vulnerability’s severity. By crafting a request to a go-zero application from a non-allowed origin such as not-safe.com, attackers could bypass the CORS Filter. This bypass effectively breaks the CORS policy, enabling unauthorized pages to make requests and retrieve data as if they were legitimate users or services.
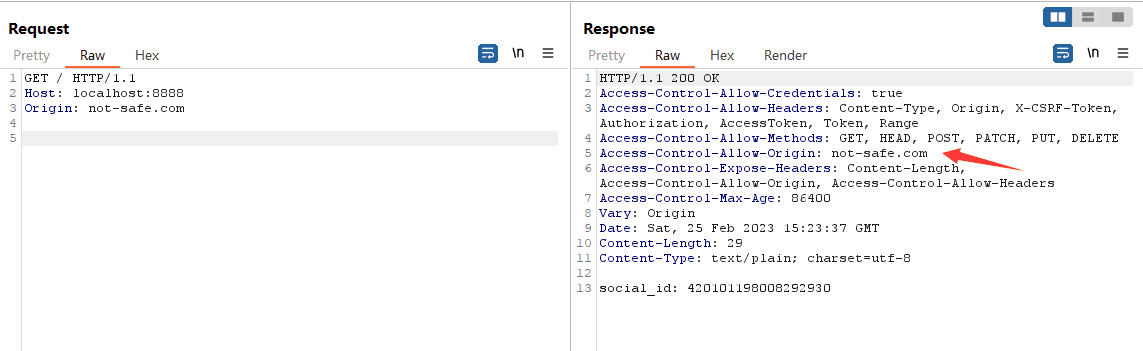
A successful exploit of this vulnerability breaks your CORS policy, potentially allowing:
- Cross-Site Attacks: Attackers could launch requests from unauthorized websites, masquerading as legitimate users.
- Data Theft: Sensitive information could be extracted from your application, impacting both you and your users.
If you’re using go-zero versions earlier than v1.4.4, you’re vulnerable. Recognizing the potential for widespread exploitation and the threat to tens of millions of users, a patch was swiftly developed and released. Version v1.4.4 of go-zero addressed this vulnerability by correcting the flawed origin validation logic, and closing the loophole that allowed unauthorized domain access. While updating, take the opportunity to reassess your CORS rules, ensuring they are as restrictive as necessary.