A security researcher has published a proof-of-concept (PoC) exploit code for a CVE-2024-27801 vulnerability affecting multiple Apple platforms, including macOS Sonoma, iOS/iPadOS, and visionOS. This vulnerability has the potential to elevate privileges, granting malicious apps unauthorized access to system services and sensitive user data.
The vulnerability was identified and reported by the CertiK SkyFall Team, a renowned group of security researchers dedicated to uncovering and addressing critical security flaws. CVE-2024-27801 exists in the low-level implementation of NSXPC, a crucial component affecting all Apple platforms. The vulnerability has been present in the ecosystem until the recent patch release in May, covering tvOS 17.5, visionOS 1.2, iOS 17.5, iPadOS 17.5, watchOS 10.5, and macOS Sonoma 14.5.
Apple’s advisory succinctly states, “An app may be able to elevate privileges,” attributing the resolution to improved checks in the system. However, the potential impact of this vulnerability extends far beyond this brief description. According to WangTielei, a prominent security researcher from the CertiK SkyFall Team, CVE-2024-27801 could have allowed malicious apps to gain unauthorized access to system services and user data.
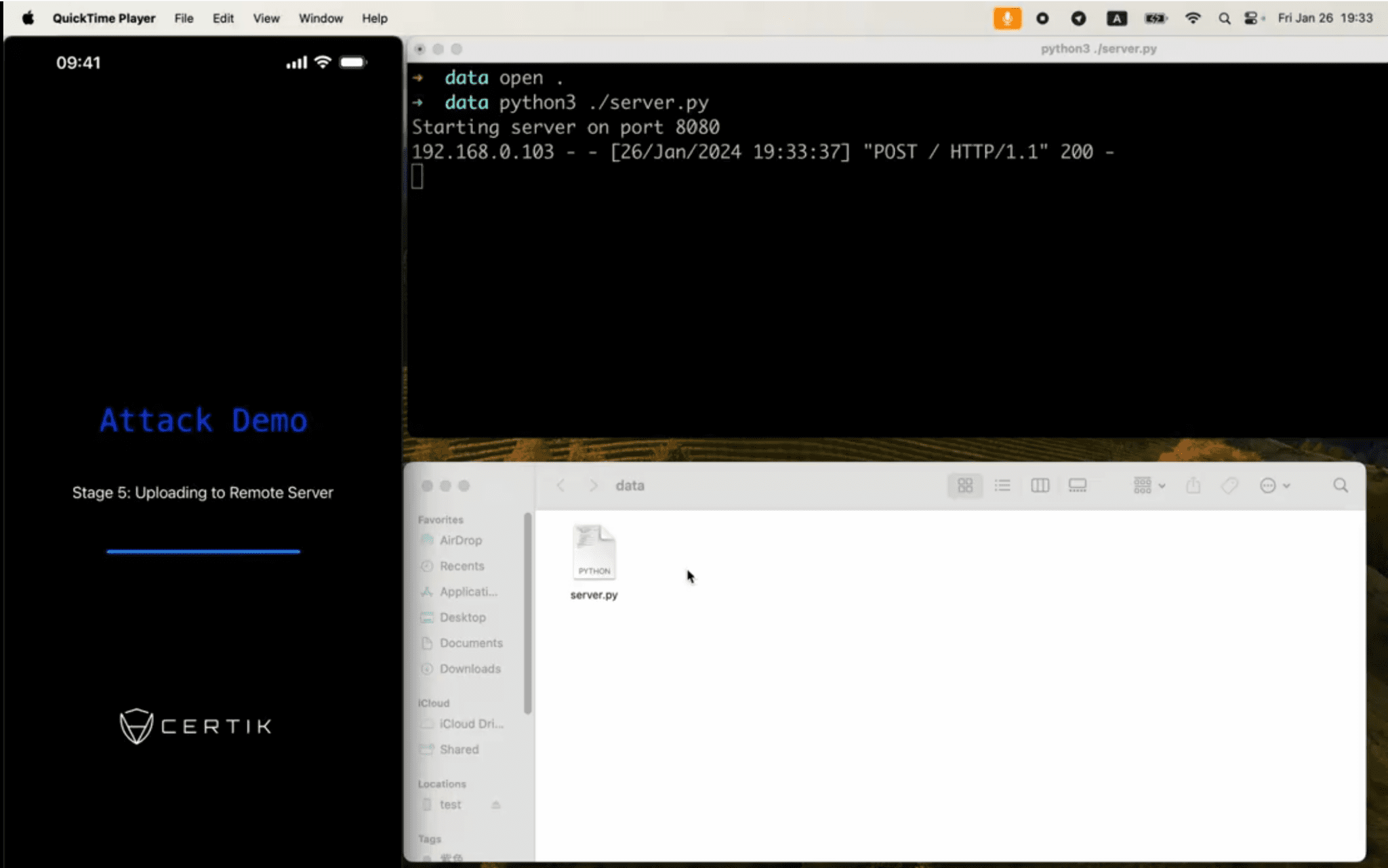
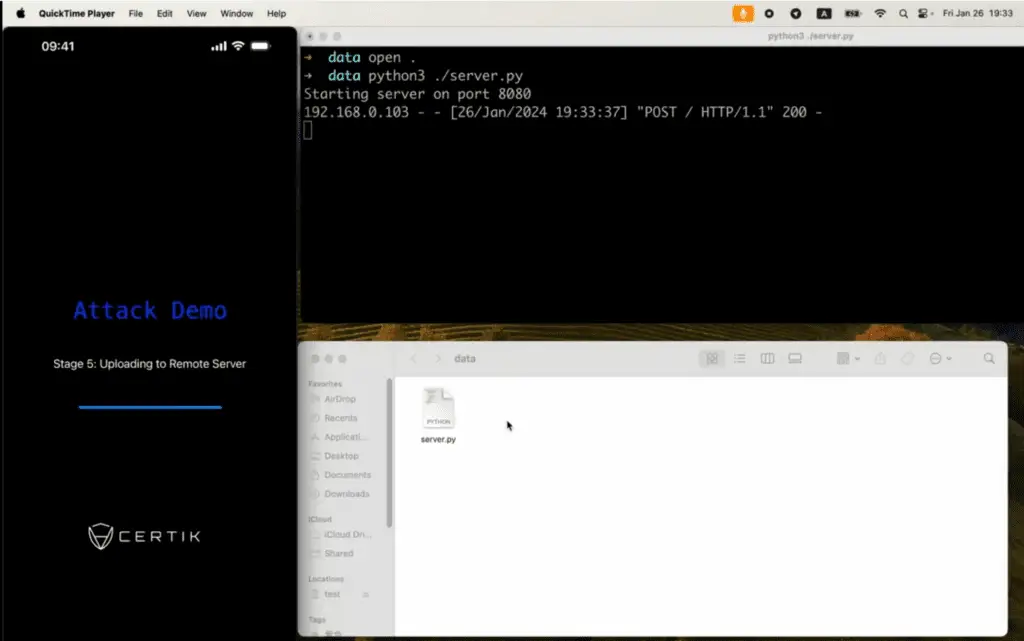
Particularly concerning is the potential for these apps to steal sensitive information from third-party applications with architectures similar to Telegram. In a striking demonstration, the CertiK SkyFall Team published a video showcasing how a malicious app could steal chat history, including pictures, from Telegram and transfer the data to a remote server.
To emphasize the severity of the CVE-2024-27801 vulnerability, WangTielei has published the proof-of-concept exploit code on GitHub.
While there is no evidence of active exploitation in the wild, the public disclosure of the PoC code increases the risk of malicious actors attempting to weaponize the vulnerability. The fact that popular messaging apps like Telegram could have been targeted underscores the potential impact on user privacy.
Fortunately, Apple has acted swiftly to address this critical security flaw. A comprehensive patch was released in May, covering all affected platforms. Users are strongly urged to update their devices to the latest versions—tvOS 17.5, visionOS 1.2, iOS 17.5, iPadOS 17.5, watchOS 10.5, and macOS Sonoma 14.5—to protect against potential exploitation.