
A critical security vulnerability (CVE-2024-28000, CVSS 9.8) in the widely-used Litespeed Cache plugin for WordPress has been disclosed, leaving over 5 million websites at risk of complete takeover. The vulnerability allows unauthenticated attackers to escalate their privileges and gain administrative access, effectively seizing control of affected sites.
The vulnerability in question stems from improper implementation of the “role simulation” feature within LiteSpeed Cache, up to and including version 6.3.0.1. The flaw allows unauthenticated users to spoof their user ID, setting it to that of an administrator. This is possible through the manipulation of a hashed value stored in the database, which can be found in debug logs or brute-forced due to its short length and limited permutations.
The CVE-2024-28000 vulnerability primarily exploits two key functions:
async_litespeed_handler(): This function, responsible for generating the critical$hashvalue, lacks proper capability or nonce checks, allowing unauthorized users to trigger it. Once triggered, the function simulates a crawl, generating a$hashvalue that is stored in the database.is_role_simulation(): This function, activated via an init hook, compares thelitespeed_hashcookie with the stored hash in the database. If they match, the function then uses thelitespeed_rolecookie value to set the current user role, potentially elevating it to an administrator level.
The combination of these flaws enables attackers to create a new administrative user account by sending requests to the /wp-json/wp/v2/users REST API endpoint, thus gaining full control over the WordPress site.
The severity of this vulnerability is compounded by the simplicity of the attack vector. The $hash value, generated by the Str::rrand() function, is only 6 characters long and limited to 1,000,000 possible combinations, making it feasible for an attacker to brute force. Furthermore, the hash never expires and utilizes a loose comparison, further easing exploitation.
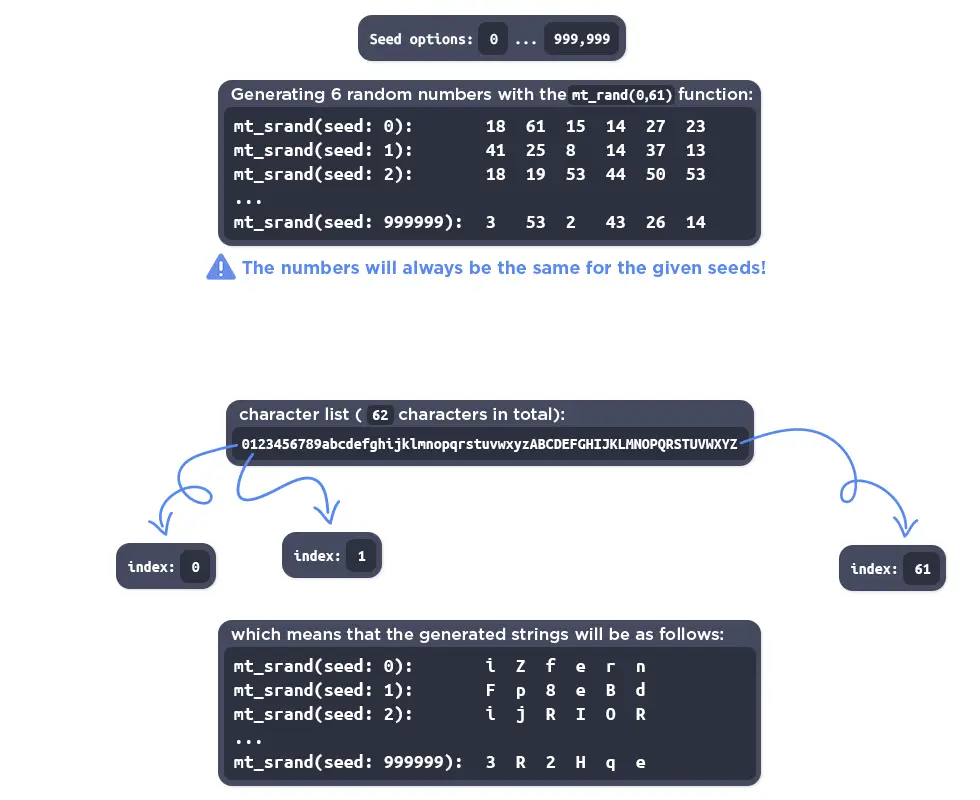
In environments where the LiteSpeed Cache’s crawler is disabled, this issue may not be exploitable. However, given the widespread use of this feature and the potential for the hash to be exposed through debugging logs, the threat remains significant.
Wordfence Threat Intelligence has already detected and blocked 990 attacks targeting this vulnerability within the past 24 hours, highlighting the urgency of the situation.
Website administrators using LiteSpeed Cache are urged to update to the latest version, 6.4.1, which patches this critical vulnerability. Immediate action is crucial as active exploitation of this flaw is likely to escalate.
Additionally, administrators should review their WordPress configurations to ensure that debugging is disabled on production sites, thereby minimizing the risk of sensitive data exposure. Regular audits of plugins and their settings are also recommended to prevent such vulnerabilities from being exploited.
Related Posts:
- WordPress Sites Under Widespread Attack – LiteSpeed Cache Plugin Exploit Puts Millions at Risk
- Wave of Attacks on WordPress: Urgent Update for WP Statistics, WP Meta SEO, LiteSpeed Cache
- LiteSpeed Cache Plugin Vulnerability Puts Millions of WordPress Sites at Risk
- WordPress LiteSpeed Cache Plugin Flaw Exposes 4M Sites to XSS Attacks
- XSS Alert: Patch LiteSpeed Cache Plugin Immediately
