Image: LeadroyaL
A security researcher has published details and proof-of-concept (PoC) exploit code for a critical vulnerability (CVE-2024-37051) that impacts users of its IntelliJ integrated development environment (IDE) apps and exposes GitHub access tokens. This vulnerability has a high CVSS score of 9.3. The flaw affects all IntelliJ-based IDEs from version 2023.1 onwards, where the JetBrains GitHub plugin is enabled and configured.
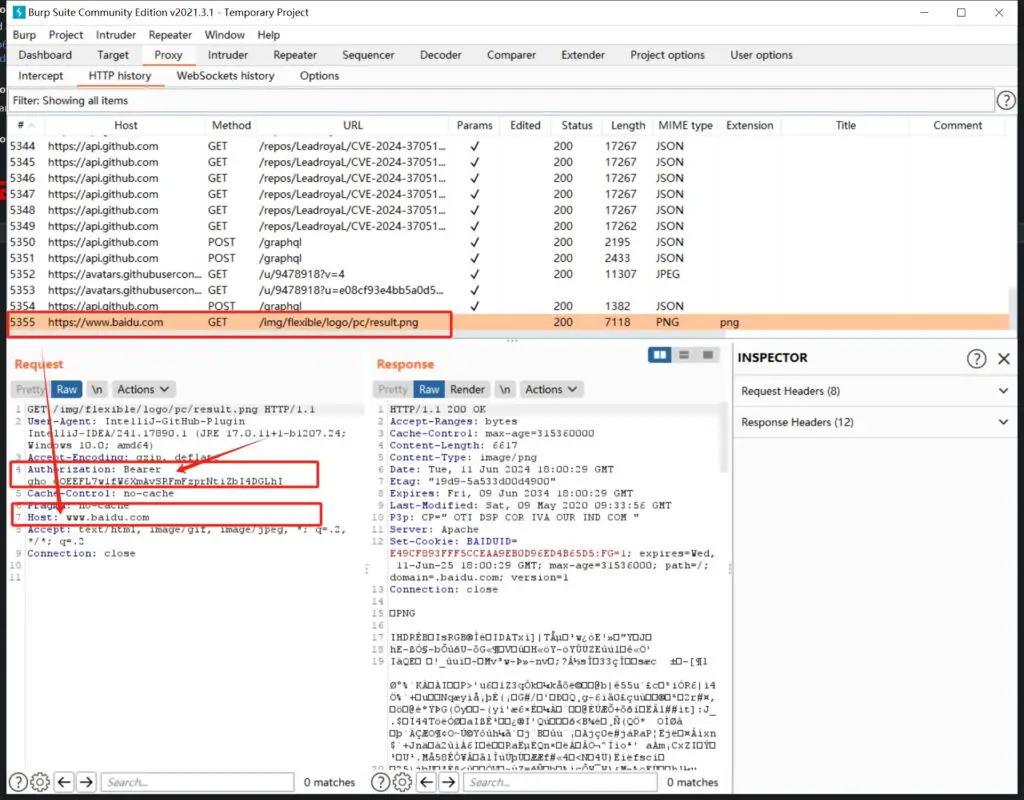
The vulnerability was reported on May 29, 2024, by an external security researcher. According to Ilya Pleskunin, Security Support Team Lead at JetBrains, the vulnerability allows malicious content in a GitHub pull request to expose access tokens to a third-party host when handled by IntelliJ-based IDEs. These tokens could grant attackers unauthorized access to GitHub accounts, posing severe risks of code tampering and data theft.
Recently, security researcher LeadroyaL published the technical details and a proof-of-concept exploit code for the CVE-2024-37051 flaw.
JetBrains has identified several of its products as vulnerable to this flaw. The affected IDEs include:
- Aqua: 2024.1.2
- CLion: 2023.1.7, 2023.2.4, 2023.3.5, 2024.1.3, 2024.2 EAP2
- DataGrip: 2024.1.4
- DataSpell: 2023.1.6, 2023.2.7, 2023.3.6, 2024.1.2
- GoLand: 2023.1.6, 2023.2.7, 2023.3.7, 2024.1.3, 2024.2 EAP3
- IntelliJ IDEA: 2023.1.7, 2023.2.7, 2023.3.7, 2024.1.3, 2024.2 EAP3
- MPS: 2023.2.1, 2023.3.1, 2024.1 EAP2
- PhpStorm: 2023.1.6, 2023.2.6, 2023.3.7, 2024.1.3, 2024.2 EAP3
- PyCharm: 2023.1.6, 2023.2.7, 2023.3.6, 2024.1.3, 2024.2 EAP2
- Rider: 2023.1.7, 2023.2.5, 2023.3.6, 2024.1.3
- RubyMine: 2023.1.7, 2023.2.7, 2023.3.7, 2024.1.3, 2024.2 EAP4
- RustRover: 2024.1.1
- WebStorm: 2023.1.6, 2023.2.7, 2023.3.7, 2024.1.4
JetBrains has promptly released security updates to address this vulnerability in the affected IDEs. The company has also patched the vulnerable JetBrains GitHub plugin and removed all previously impacted versions from its official plugin marketplace. Users are strongly urged to update to the latest versions immediately.
JetBrains has issued specific recommendations for users to mitigate potential risks:
- Patch Systems: Update to the latest version of the affected IDEs immediately.
- Revoke GitHub Tokens: Users who have actively used GitHub pull request functionality in IntelliJ IDEs should revoke any GitHub tokens used by the vulnerable plugin. This step is crucial even if two-factor authentication is enabled.
- OAuth Integration: If the plugin was used with OAuth integration or Personal Access Token (PAT), users should revoke access for the JetBrains IDE Integration app and delete the IntelliJ IDEA GitHub integration plugin token.
JetBrains has collaborated with GitHub to minimize the impact of this vulnerability. However, due to the mitigation measures, the JetBrains GitHub plugin may not function as expected in older IDE versions. Users need to set up the plugin again after revoking tokens, as all plugin features, including Git operations, will cease to function until reconfigured.