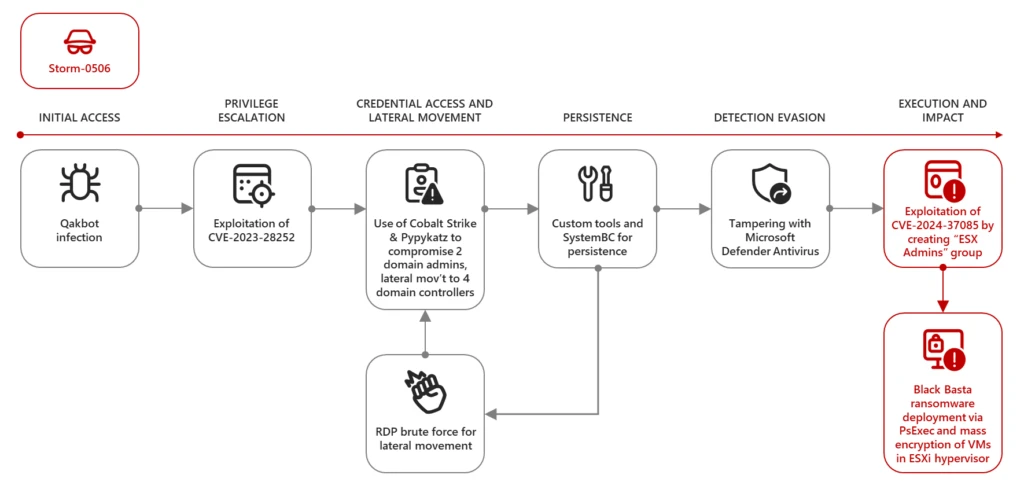
Storm-0506 ESXi attack chain | Image: Microsoft
Microsoft Threat Intelligence has disclosed a vulnerability (CVE-2024-37085) in VMware ESXi hypervisors, which is being actively exploited in the wild by multiple ransomware threat actors. The vulnerability allows unauthorized access and control of affected ESXi servers, putting entire virtualized infrastructures at severe risk.
The vulnerability resides in the way domain-joined ESXi hypervisors handle domain groups. By default, any member of a domain group named “ESX Admins” is automatically granted full administrative privileges on the ESXi server without adequate validation. Threat actors have been observed creating or manipulating this group to gain unauthorized access, circumventing standard security controls.
Microsoft researchers have outlined three primary methods for exploiting this vulnerability:
- Creating the “ESX Admins” Group: Any domain user with group creation permissions can create the “ESX Admins” group and add themselves or other users to it, instantly gaining administrative access to the ESXi hypervisor.
- Renaming an Existing Group: Threat actors can rename any arbitrary group to “ESX Admins” and use an existing or newly added member to escalate privileges.
- Privileges Refresh: Even if administrators change the management group for the ESXi hypervisor, administrative privileges for members of the “ESX Admins” group are not immediately revoked, allowing continued exploitation.
Successful exploitation can lead to the encryption of the ESXi file system, effectively disabling all hosted virtual machines (VMs). This can disrupt critical business operations and potentially result in significant financial losses. In addition to encryption, attackers may also exfiltrate sensitive data or pivot within the network, causing further damage.
Microsoft’s report highlights several ransomware operators, including Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest, utilizing this vulnerability. In one notable instance, Storm-0506 deployed Black Basta ransomware to target an engineering firm in North America. The attackers initially compromised the network via a Qakbot infection, followed by exploiting a Windows vulnerability (CVE-2023-28252) to elevate privileges. Using tools like Cobalt Strike and Pypykatz, they stole credentials, moved laterally, and ultimately created the “ESX Admins” group to gain control over the ESXi hypervisors, leading to mass encryption of the system.
VMware has released a security update addressing CVE-2024-37085, and administrators are urged to apply these updates promptly. For ESXi versions without a planned patch, VMware provides a workaround to enhance security settings. Additionally, researchers recommend keeping ESXi servers off the public internet and following best practices for mitigating risks of exploitation. Microsoft has additional recommendations on mitigating the risk of exploitation in their blog.
Related Posts:
- VmWare releases the patch to fix CPU vulnerabilities in VMware ESXi, Workstation and Fusion
- VmWare fix two high-risk arbitrary code execution vulnerabilities in several products
- VMware Issues Critical Patches for ESXi, Workstation, Fusion, & Cloud Foundation