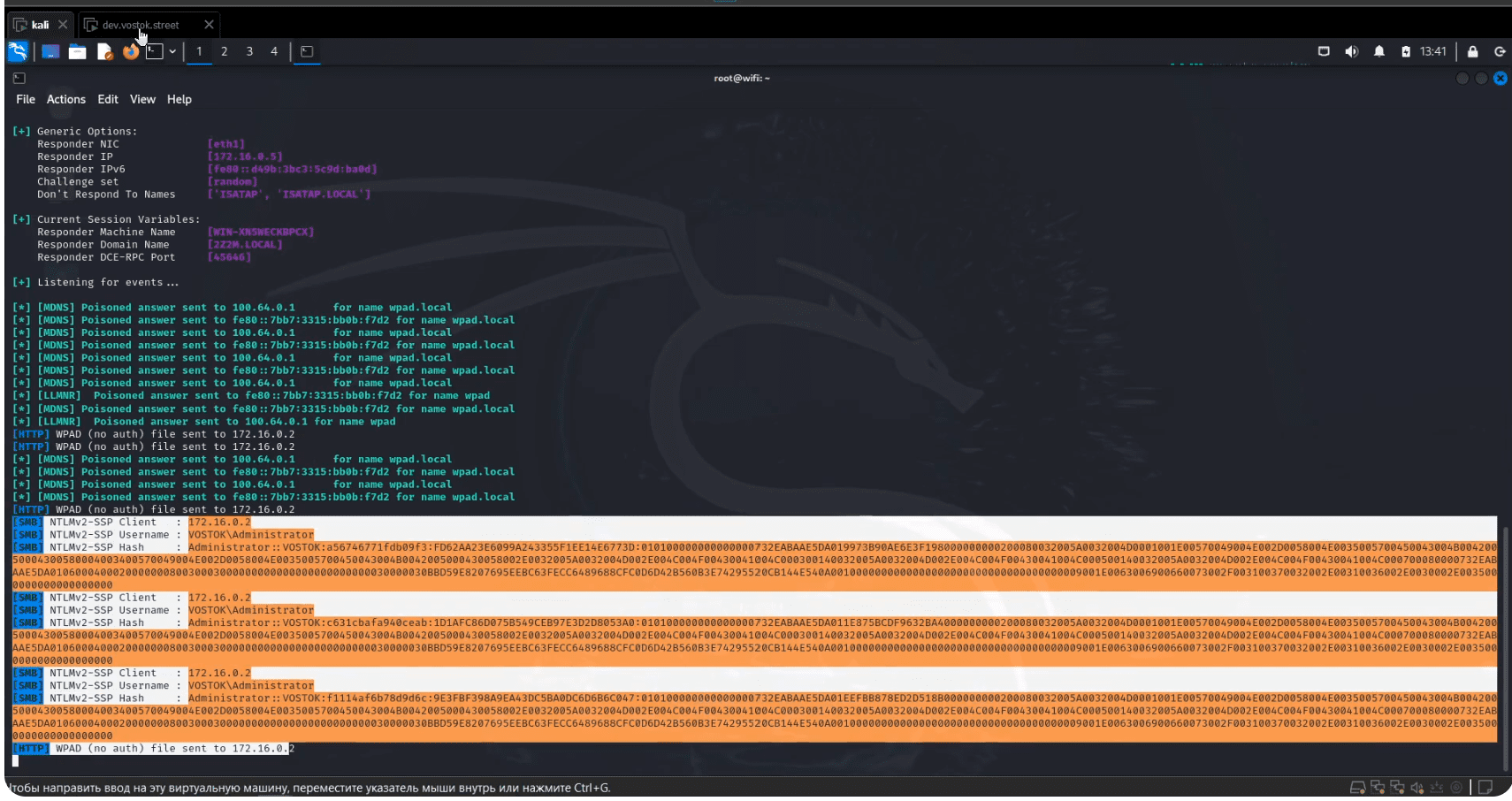
In a recent security bulletin, Microsoft disclosed a critical vulnerability in Windows File Explorer, identified as CVE-2024-38100, with a CVSS score of 7.8. This flaw, discovered by Andrea Pierini from Semperis, allows attackers to gain administrator privileges through a privilege escalation exploit. Dubbed “Leaked Wallpaper” by researcher Michael Zhmaylo, this vulnerability enables the leakage of a user’s NetNTLM hash from any session, even from low-privileged accounts.
CVE-2024-38100 affects Windows File Explorer and can be exploited to elevate privileges to an administrator level. The exploit, known as “Leaked Wallpaper,” works by leaking a user’s NetNTLM hash, which can then be used to gain further access to the system. This exploit is particularly concerning because it allows attackers to escalate privileges from any user session, significantly increasing the potential for damage.
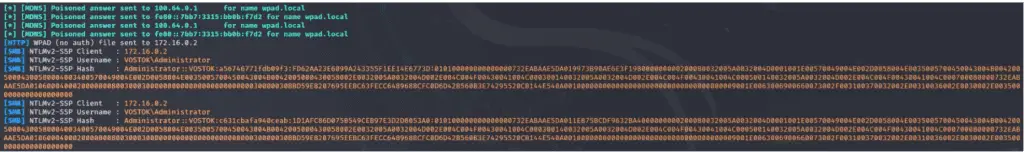
Michael Zhmaylo recently published a proof-of-concept (PoC) exploit for CVE-2024-38100, demonstrating the vulnerability’s impact. The PoC code and a video demonstration are available on GitHub, providing attackers with the tools needed to exploit the flaw.
Microsoft addressed this vulnerability in the July Patch Tuesday update, releasing the fix under KB5040434. Users and administrators are strongly advised to apply this update immediately to protect their systems from potential exploitation.
The Leaked Wallpaper vulnerability serves as a stark reminder of the importance of proactive security measures. Regularly applying security updates, maintaining strong password hygiene, and implementing robust security solutions are essential steps to safeguard systems against evolving threats.
In addition, organizations should educate their users about the risks of social engineering attacks, which can often be used to trick users into running malicious code or revealing sensitive information. By raising awareness and staying informed about emerging threats, users can play a vital role in protecting themselves and their organizations from cyberattacks.
Related Posts:
- Security Expert Announces PoC to Crashes All Recent Windows
- From Games to Ransom: Albabat’s Deceptive Distribution Method Exposed
- Fleckpe: A Subscription Trojan Infiltrating Google Play Store