A security vulnerability, identified as CVE-2024-39202, has been discovered in the D-Link DIR-823X AX3000 Dual-Band Gigabit Wireless Router, posing a significant risk to users. The vulnerability was reported to D-Link by third-party security researcher Adesh Kolte on July 7, 2024.
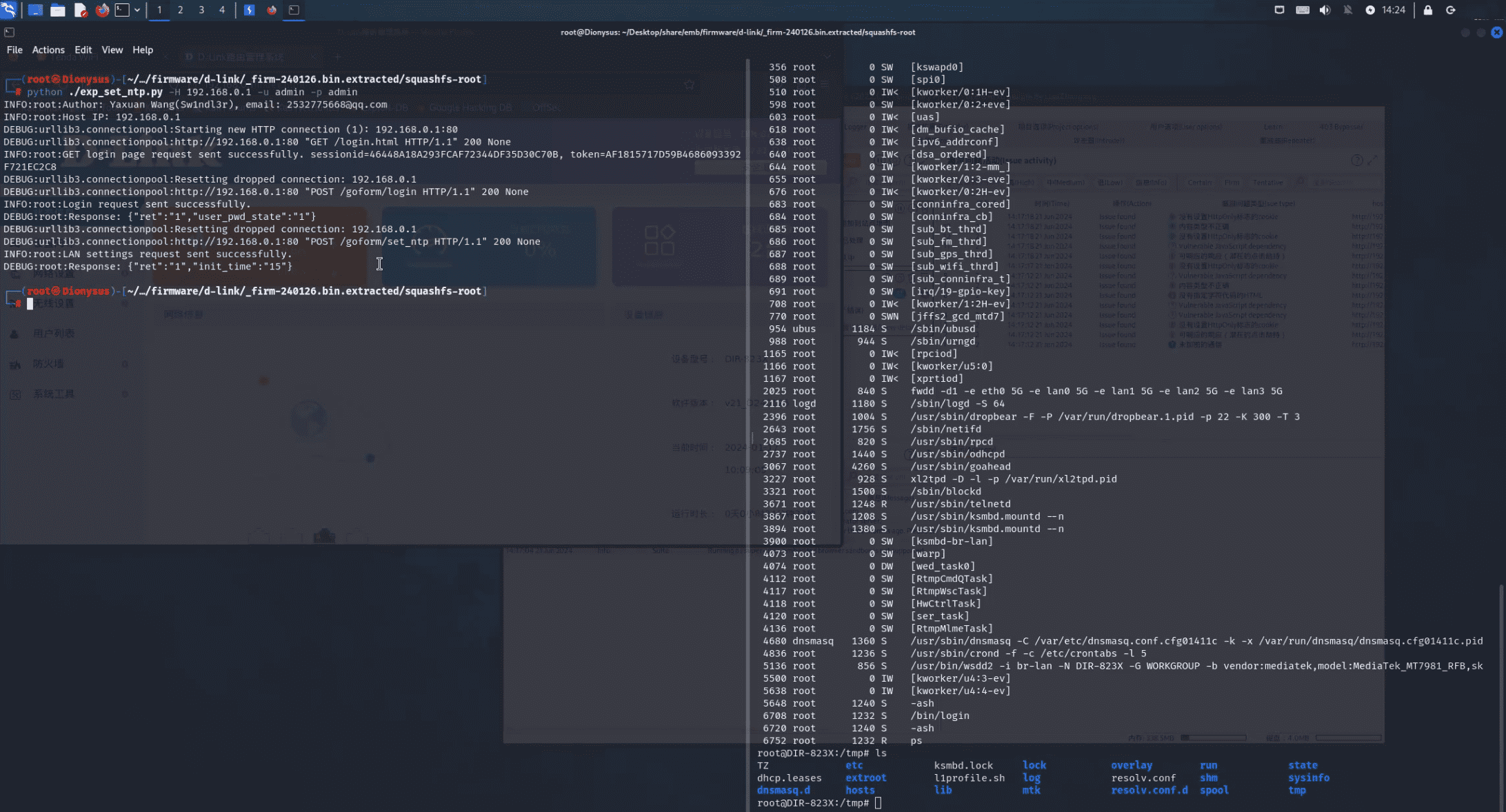
The vulnerability is present in the (Non-US) DIR-823X Hardware Revision Ax, specifically in Firmware version 240126. It allows for authenticated Remote Command Execution due to improper handling of the ntp_zone_val field in the CGI request for /goform/set_ntp. This flaw enables an attacker to craft a malicious ntp_zone_val field and send a malicious HTTP request to the /goform/set_ntp CGI, leading to command execution with administrator privileges on the firmware file system.
Kolte, who reported the CVE-2024-39202 flaw to D-Link, also published detailed technical information and a proof-of-concept (PoC) exploit code. In a demonstration video, Kolte showed how easily the vulnerability could be exploited, underlining the urgent need for a fix.
D-Link Corporation has acknowledged the severity of the issue and is currently working on developing patches to address it. In the meantime, users of the affected router model are strongly urged to take immediate action to protect their networks:
- Check Your Firmware: Verify the firmware version of your D-Link DIR-823X router. If it is 240126 or earlier, your device is vulnerable.
- Disable Remote Management: Immediately disable remote management access to your router through the web interface. This will help prevent external attackers from exploiting the flaw.
- Limit Access: Restrict access to your router’s administration panel to trusted devices on your network. Use strong, unique passwords and change them regularly.
- Stay Updated: Monitor D-Link’s official website for updates and apply patches as soon as they become available.