
A significant vulnerability has been identified in Laravel v11.x, the popular PHP web framework renowned for building modern, elegant web applications. This vulnerability, designated as CVE-2024-40075, is an XML External Entity (XXE) flaw that could potentially allow attackers to execute arbitrary commands and access sensitive data.
Security researcher Q16G has provided an in-depth analysis of the vulnerability, outlining the critical points of exploitation within Laravel’s codebase. The vulnerability traces back to the handling of the __destruct function in the Monolog\Handler\Handler class, a core component of Laravel’s logging mechanism. Here’s a detail of the exploit process:
- Tracing the __destruct Function: The researcher first identified that the __destruct function, found in the abstract class Monolog\Handler\Handler, is called if not overridden by a subclass. This function ultimately calls the close method.
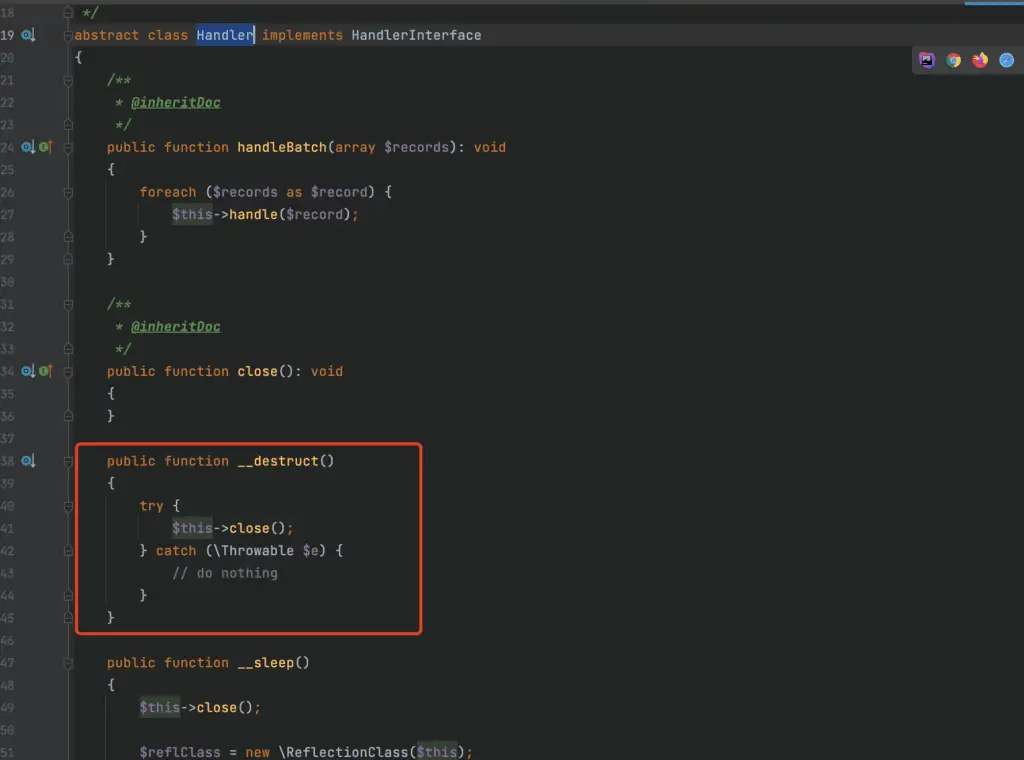
Monolog\Handler\Handler - Subclass Analysis: By locating a subclass that overrides the close method but not the __destruct method, such as groupHandler, it was possible to further trace the execution flow.
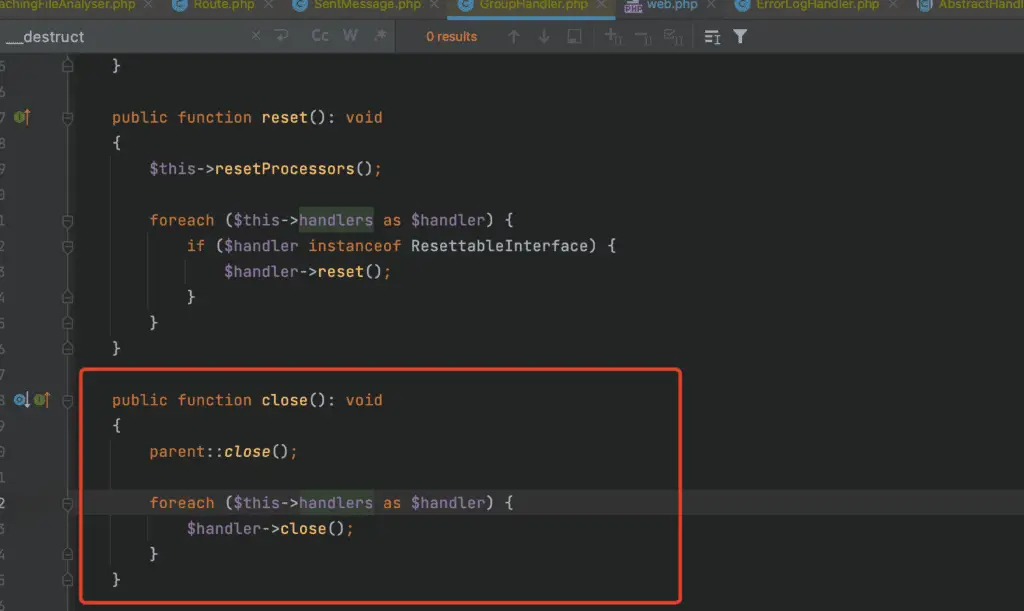
Monolog\Handler\GroupHandler - Handler Iteration: In the groupHandler close method, the code iterates through handlers and executes their close methods, leading to the discovery of the getStreamName method call.
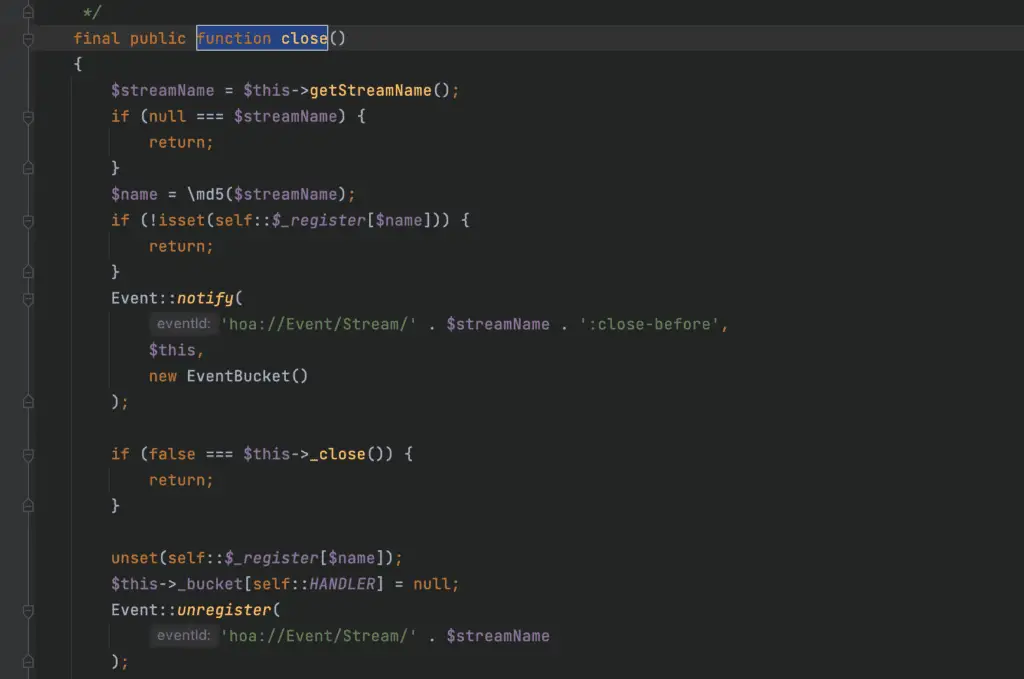
Psy\Readline\Hoa\Stream - Trigger Identification: The getStreamName method then invokes the md5 function, necessitating the search for a __tostring trigger. The researcher identified the implementation class Psy\Readline\Hoa\FileRead as a critical component.
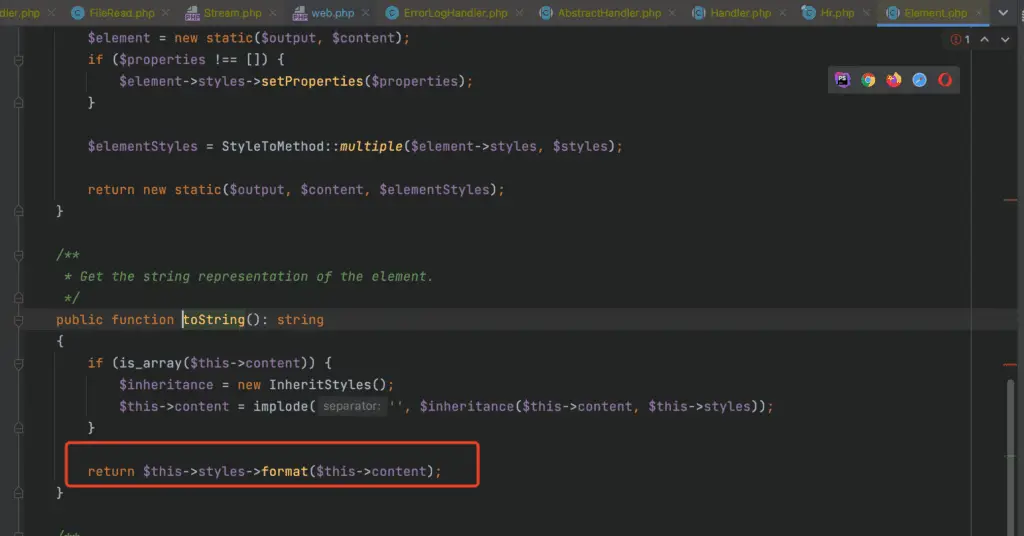
Termwind\Components\Element - Function Execution: Finally, because the __tostring function calls the tostring function, which in turn calls the $this->stypes->format function, the vulnerability could be exploited to execute arbitrary commands.
The CVE-2024-40075 vulnerability poses a serious risk as it allows malicious actors to manipulate XML input and perform unauthorized operations, potentially leading to data breaches and system compromises. Given the widespread use of Laravel for web development, the impact of this vulnerability could be extensive, affecting numerous web applications globally. Users are strongly urged to update to the latest version to protect their applications.
Related Posts:
- Popular Chinese Text Editors Compromised in Targeted Attack
- DanaBot Malware: The Hidden Threat in Job Application Emails
- Cybercriminals Exploit Swap Files: New E-commerce Skimming Tactic
- Fickle Stealer: A Rust-Based Stealer with Evolving Attack Chains and Flexible Targeting