
A severe security vulnerability has been discovered in the widely-used AI library llama_cpp_python, potentially allowing threat actors to execute malicious code on affected systems remotely. The vulnerability, tracked as CVE-2024-42479, carries a critical CVSS score of 10, signifying its significant impact on cybersecurity.
The vulnerability stems from a “Write-what-where” condition in the rpc_server::set_tensor function. This condition arises from the unsafe handling of data pointers within the rpc_tensor structure, potentially enabling attackers to write data to arbitrary memory locations. This type of vulnerability can serve as a foundation for a wide range of exploits, including those leading to remote code execution.
llama_cpp_python, a Python binding for the llama.cpp library, has over 3 million downloads, making it a highly popular tool among developers for integrating AI models with Python applications. This widespread adoption significantly amplifies the potential reach of this vulnerability, putting millions of users at risk.
The vulnerability was discovered by 7resp4ss, a security researcher at 360 Vulnerability Research Institute, who provided a detailed proof-of-concept exploit demonstrating the severity of this flaw. By combining CVE-2024-42479 with another vulnerability that allows arbitrary address reading, the researcher successfully achieved RCE, highlighting the critical impact of this flaw on affected systems.
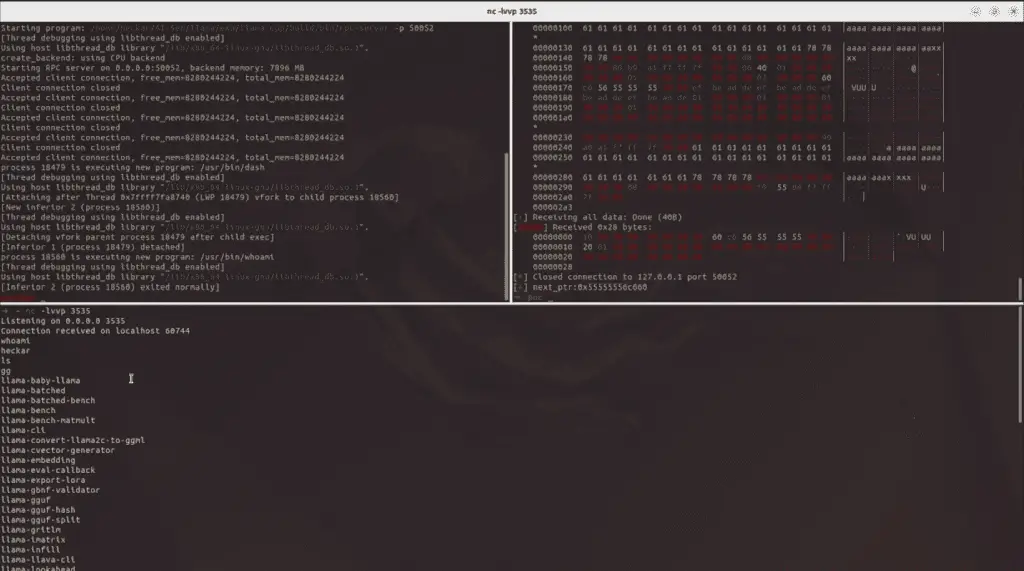
The proof-of-concept exploit has been published along with a technical breakdown, allowing security professionals to understand the mechanics of the attack. Additionally, a demonstration video has been released, showcasing the ease with which this vulnerability can be exploited.
The vulnerability has been patched in version b3561 of the llama_cpp_python package. Users are strongly advised to update their installations immediately to mitigate the risk of exploitation. Failing to do so could leave systems vulnerable to attacks that could result in unauthorized access, data breaches, and potentially, full system compromise.
Organizations leveraging llama_cpp_python in their AI and machine learning projects should prioritize this update, considering the widespread use of this package and the critical nature of the vulnerability.