
A critical vulnerability has been found in TP-Link RE365 V1_180213 series routers, leaving them susceptible to remote exploitation and potential takeover. Identified as CVE-2024-42815 and carrying a near-perfect CVSS score of 9.8, this flaw poses a serious risk to users of these popular networking devices.
The vulnerability stems from a buffer overflow issue in the router’s HTTP server. By sending a specially crafted HTTP request with an overly long “User-Agent” header, attackers can trigger a buffer overflow, potentially crashing the device or, more alarmingly, executing malicious code on it.
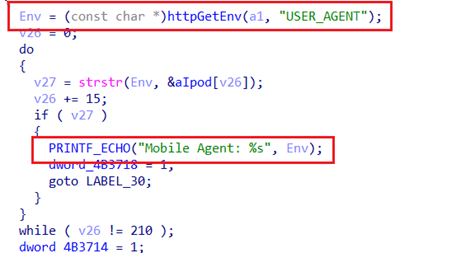
The vulnerability resides in the httpRpmWmbParse function within the /usr/bin/httpd binary, specifically linked to how the router handles the USER_AGENT field in HTTP GET requests. The issue arises due to the absence of length verification for the USER_AGENT field, which is passed unchecked to the PRINTF_ECHO function. This function, in turn, concatenates the USER_AGENT content into a format string using the vsprintf function, storing the result in a variable named v3.
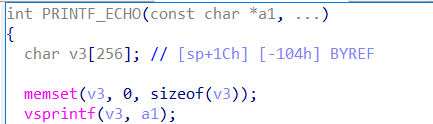
Because there is no safeguard on the length of data that can be entered into the USER_AGENT field, attackers can exploit this weakness by sending a specially crafted GET request with an excessively long USER_AGENT header. The result is a buffer overflow, which can cause the router to crash, leading to a denial of service (DoS) or even allowing the execution of arbitrary commands on the device.
The implications of CVE-2024-42815 are severe. By leveraging this vulnerability, a remote attacker could effectively disrupt the normal operation of the affected router, rendering it unusable through a targeted DoS attack. More concerning, however, is the possibility of executing arbitrary commands on the device, which could lead to a complete compromise of the router and the network it supports. Such an exploit could open the door to further attacks, including data exfiltration, network surveillance, and the propagation of malware.
TP-Link has released a patch for this vulnerability. Users are strongly advised to upgrade firmware immediately.
Related Posts:
- Congress Scrutinizes TP-Link Routers Over Cybersecurity Concerns
- Old Vulnerability, New Attacks: Botnets Swarm Exploited CVE-2023-1389 in TP-Link Routers
- Hackers use Cisco Router flaws to attack Iran, 3,500 routers hacked
- Mirai Botnet Exploits TP-Link Router’s CVE-2023-1389 Vulnerability