CVE-2024-44000 (CVSS 9.8): Litespeed Cache flaw exposes millions of WordPress sites to takeover attacks

A significant security vulnerability has been uncovered in the popular LiteSpeed Cache plugin for WordPress, which boasts over 5 million active installations. The vulnerability, discovered by Rafie Muhammad, a security researcher at Patchstack, poses a severe threat to WordPress users by allowing unauthenticated visitors to gain access to logged-in accounts, including those with administrator privileges. The vulnerability, identified as CVE-2024-44000, carries a CVSS score of 9.8, marking it as critical.
The LiteSpeed Cache plugin, widely used for its robust caching and site optimization features, suffers from an unauthenticated account takeover flaw. This vulnerability allows attackers to hijack user sessions, potentially escalating their access to an administrator-level role. Once an attacker gains such access, they can upload and install malicious plugins, taking complete control over the compromised site.
The vulnerability stems from an issue within the plugin’s debug log feature, which inadvertently leaks HTTP response headers, including sensitive “Set-Cookie” headers. This occurs when users log in to a WordPress site, and if the debug log feature is enabled or has been previously activated, attackers can exploit this leak to hijack user sessions.
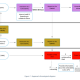
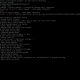
The root of the CVE-2024-44000 vulnerability lies in the ended function of the plugin, which calls the self::debug() function with headers_list() data as its parameter.
This function compiles all HTTP response headers, including the “Set-Cookie” header, and writes them into the debug log file. If the debug log feature has been enabled at any point, the log file may contain sensitive session cookies, exposing them to attackers if the file is not purged.
The exploitability of this vulnerability depends on two key conditions:
- The debug log feature must be active or have been activated in the past without the log file being purged.
- The attacker must be able to access the
/wp-content/debug.logfile, which retains the leaked cookies.
In response to this critical vulnerability, the LiteSpeed team released a patch in version 6.5.0.1 of the plugin. While the patch addresses the core issues, additional recommendations were made to enhance the security of affected sites:
- Implementing proper
.htaccessrules to deny direct access to the new log files, as the current rules are insufficient to fully block access. - Purging or removing content from the old
debug.logfile, especially if the debug feature had been enabled in the past, to prevent attackers from accessing previously leaked cookie data.
Related Posts:
- CVE-2024-28000 (CVSS 9.8): Active Exploitation of Litespeed Cache Vulnerability, 5 Million WordPress Sites at Risk of Complete Takeover
- CVE-2024-28000 in LiteSpeed Cache Plugin Actively Exploited: Over 30,000 Attacks Blocked in 24 Hours
- LiteSpeed Cache Plugin Vulnerability Puts Millions of WordPress Sites at Risk
- WordPress Sites Under Widespread Attack – LiteSpeed Cache Plugin Exploit Puts Millions at Risk
- Wave of Attacks on WordPress: Urgent Update for WP Statistics, WP Meta SEO, LiteSpeed Cache