CVE-2024-4978: Backdoor Discovered in Justice AV Solutions Courtroom Software
A critical vulnerability, designated CVE-2024-4978, has been discovered in Justice AV Solutions (JAVS) Viewer software, a widely used audio-visual recording solution for courtrooms and other legal settings. This backdoor, stealthily introduced in version 8.3.7 through a compromised installer, granted attackers unfettered control of affected systems, potentially exposing sensitive legal information and proceedings to unauthorized access.
Far-Reaching Impact
JAVS technologies are deployed in over 10,000 installations worldwide, making this a security incident of significant magnitude. The breadth of JAVS’s customer base, spanning courtrooms, correctional facilities, and legal offices, raises concerns about the potential compromise of confidential legal data and the integrity of judicial processes.
Unveiling the Attack
Rapid7’s investigation revealed that the installer for JAVS Viewer v8.3.7, downloaded from the official JAVS site on March 5, contained a backdoor that could allow attackers full control over affected systems. The investigation, which started on May 10, 2024, uncovered that the installer, named JAVS Viewer Setup 8.3.7.250-1.exe, was signed with an unexpected Authenticode signature and included a malicious binary, fffmpeg.exe.

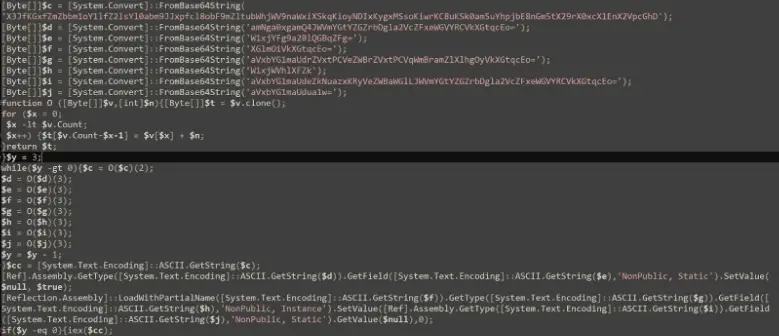
Encoded PowerShell Script Spawned by fffmpeg.exe | Image: Rapid7
The backdoored installer was traced back to the GateDoor/Rustdoor malware family, known for its ability to execute encoded PowerShell scripts, facilitating unauthorized remote access and data exfiltration. The malicious activity was identified through the execution of these scripts, which attempted to bypass security measures and establish a persistent connection with a command-and-control (C2) server.
Timeline of Compromise
The attack appears to have originated in February 2024, with the creation of a fraudulent certificate used to sign the malicious installer. The compromised software was distributed through JAVS’s official website, highlighting the insidious nature of supply chain attacks.
Remediation and Vendor Response
Rapid7 and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) promptly coordinated with JAVS to address the vulnerability. JAVS has taken swift action, removing the compromised version from its website, resetting passwords, and conducting a thorough internal audit.
Users are strongly advised to reimage any affected endpoints, reset all associated credentials, and upgrade to the latest version of JAVS Viewer (8.3.9 or higher). These steps are crucial to ensure the complete removal of any malicious remnants and the restoration of system security.





