Germany’s CERT@VDE has issued a high-severity security advisory concerning a critical vulnerability in the Moneo IIoT platform developed by ifm electronic GmbH. The platform, which is designed to facilitate industrial digitalization through a no-code approach, has been identified to contain a significant security flaw that could allow unauthenticated remote attackers to gain privileged access.
The identified vulnerability, cataloged as CVE-2024-5404 with a CVSS score of 9.8, affects the “Forgot Password” function of the Moneo IIoT platform. The flaw arises from a weak password recovery mechanism that allows an unauthorized remote attacker to change the admin password without authentication.
In Moneo appliances where no mail server is configured, this vulnerability becomes particularly critical. An attacker can exploit this weakness to reset the password to a new user default value, thereby gaining privileged access to the system.
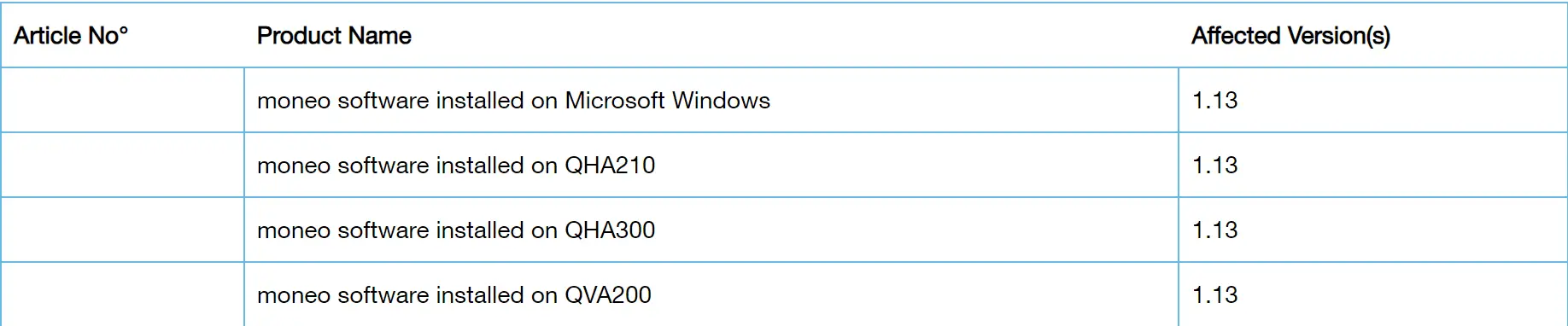
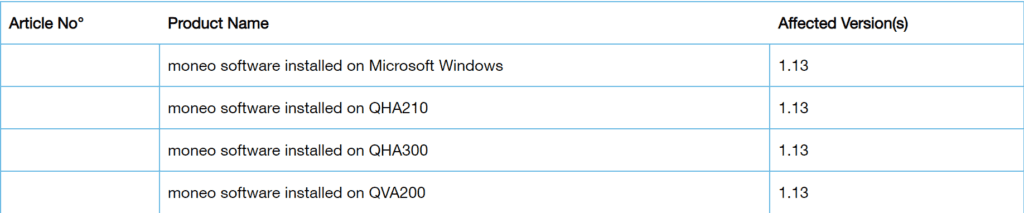
The CVE-2024-5404 vulnerability affects the following products
Given the widespread use of the Moneo IIoT platform in industrial settings for optimizing machine availability, ensuring process quality, and improving energy consumption, the potential impact of this vulnerability is considerable. Unauthorized access to the platform can lead to significant disruptions in industrial processes, data breaches, and potential manipulation of critical operational parameters.
To mitigate the risk of exploitation, ifm electronic GmbH recommends the correct configuration of a mail server within the Moneo appliance. This configuration is crucial as it prevents the unauthorized password reset mechanism from being exploited.
Furthermore, users are strongly advised to update their Moneo IIoT platform to version 1.13.5 or later. This update addresses the vulnerability and strengthens the security mechanisms within the platform to prevent similar issues in the future.