
The DataEase project has issued an urgent advisory regarding a critical vulnerability (CVE-2024-56511) affecting its popular open-source BI tool. This flaw, rated 9.3 on the CVSSv4 scale, allows unauthorized access to sensitive data by bypassing authentication mechanisms.
DataEase is a widely used business intelligence tool that enables users to analyze data and gain actionable insights with ease. Its drag-and-drop interface, support for diverse data sources, and seamless chart-sharing capabilities have made it a preferred choice for organizations seeking to optimize their operations.
The vulnerability lies in the io.dataease.auth.filter.TokenFilter class, where improper URL filtering in the authentication process allows attackers to bypass security measures. The advisory notes, “There is a flaw in the authentication in the io.dataease.auth.filter.TokenFilter class, which can be bypassed and cause the risk of unauthorized access.”
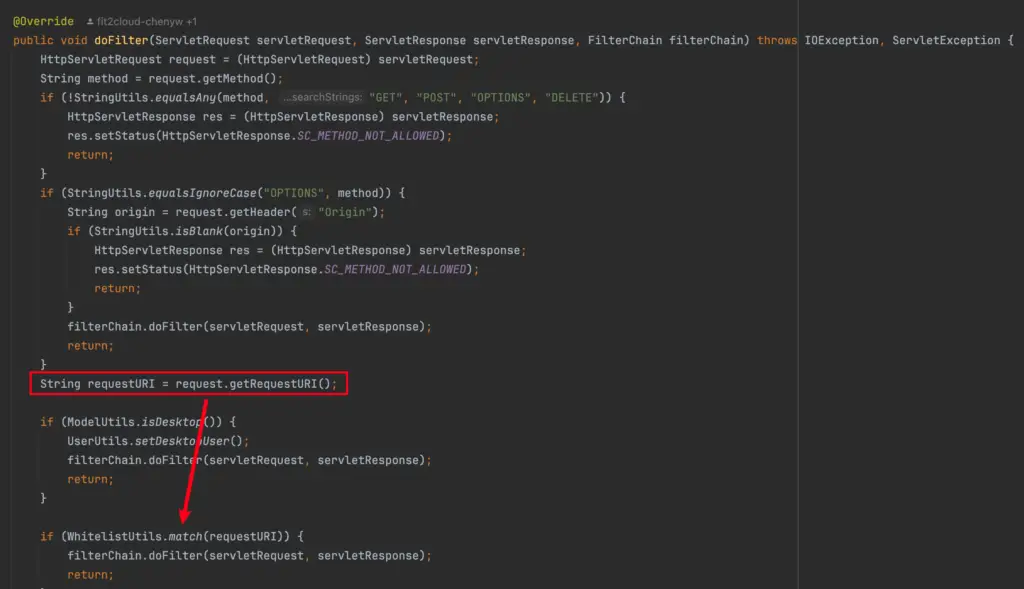
The vulnerability arises from how the TokenFilter class processes request URLs. Specifically, the WhitelistUtils.match method filters semicolons to determine whether a URL requires authentication. However, when users configure a custom server.servlet.context-path in the deployment, this mechanism can be circumvented. For example:
- Directly accessing http://127.0.0.1:8100/demo/de2api/user/info results in a 500 error, indicating token verification failure.
- By altering the URL to http://127.0.0.1:8100/geo/../demo/de2api/user/info, the request bypasses authentication, granting unauthorized access to sensitive information.
The CVE-2024-56511 vulnerability affects DataEase versions ≤ 2.10.3. If exploited, it could allow attackers to access protected resources, potentially leading to data breaches and compromised business operations.
The DataEase team has released version 2.10.4, which addresses this critical flaw. Users are strongly urged to upgrade to this version immediately to secure their systems.
Related Posts:
- Beyond HTML: The Hidden Danger of Phishing in HTTP Response Headers
- Google Patches Workspace Authentication Flaw, Thwarting Account Takeover Attempts