
A critical security vulnerability, identified as CVE-2024-7272, has been uncovered in FFmpeg, the world’s leading multimedia framework renowned for its ability to decode, encode, and stream nearly any format imaginable. This vulnerability, which affects FFmpeg versions up to 5.1.5, poses a significant threat to users and systems worldwide, with a CVSS score of 8.8.
The flaw lies within the fill_audiodata function in the /libswresample/swresample.c file of the FFmpeg library. This particular function, integral to the framework’s resampling capabilities, is susceptible to a heap-based buffer overflow. This type of overflow occurs when data is written beyond the allocated memory space, potentially leading to severe consequences such as arbitrary code execution or denial of service (DoS).
What makes this vulnerability particularly alarming is its potential for remote exploitation. Attackers can remotely trigger the heap-based overflow, and with the availability of an exploit, the risk is significantly elevated. The exploit code [1,2], published by the security researcher known as CookedMelon, is readily accessible on GitHub, demonstrating a proof-of-concept (PoC) that allows local attackers to take control of vulnerable systems. This PoC not only enables arbitrary code execution but can also be used to initiate a denial of service, rendering the affected system inoperable.
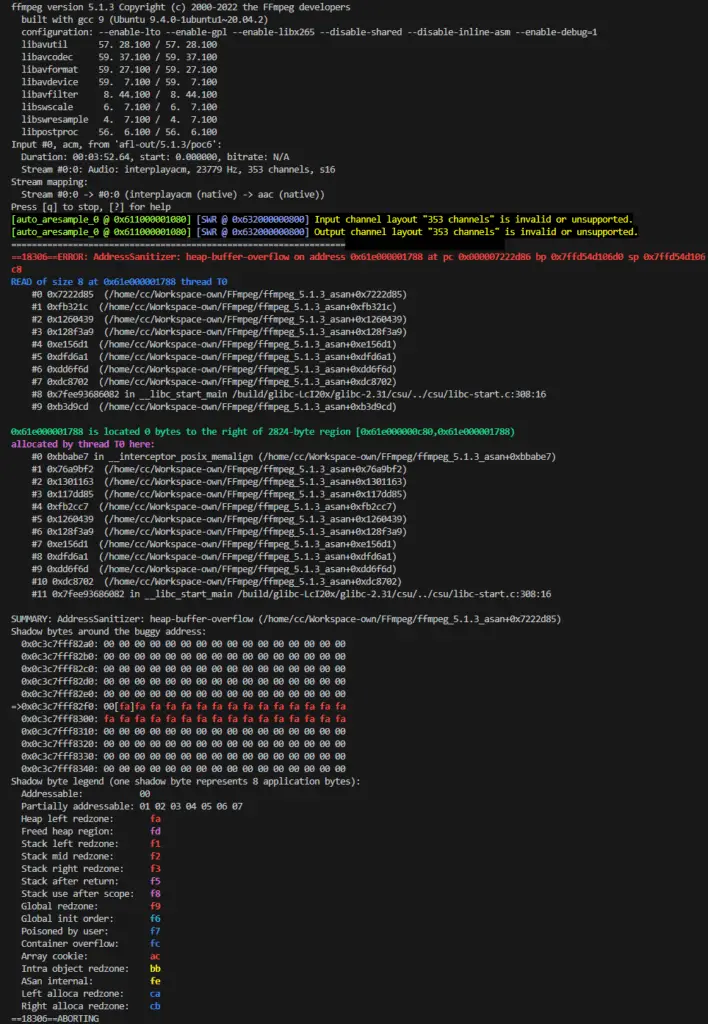
FFmpeg’s widespread adoption across various platforms, including Linux, macOS, Windows, BSDs, and Solaris, exacerbates the potential impact of CVE-2024-7272. Given FFmpeg’s extensive use in multimedia processing, from streaming services to media converters and more, the fallout from an unpatched system could be far-reaching.
The FFmpeg development team has responded to this critical vulnerability by urging all users to upgrade their installations immediately. Patching the affected component is essential to mitigating the risks associated with this vulnerability. Users running FFmpeg versions up to 5.1.5 are particularly at risk and should prioritize updating to a secure version to protect their systems from potential exploitation.
For developers and system administrators, it is recommended to review the security advisories and implement the necessary patches without delay. Additionally, verifying the security posture of FFmpeg deployments and ensuring that all components are up to date is crucial in safeguarding against such vulnerabilities.
Related Posts:
- Researcher details FFmpeg remote code execution flaw
- CVE-2024-22860 & CVE-2024-22862: Critical FFmpeg Remote Code Execution Flaws
- WordPress Issues Urgent Security Update to Patch Multiple Vulnerabilities