CVE-2024-7339: DVR Vulnerability Exposes Over 400,000 Devices to Hackers
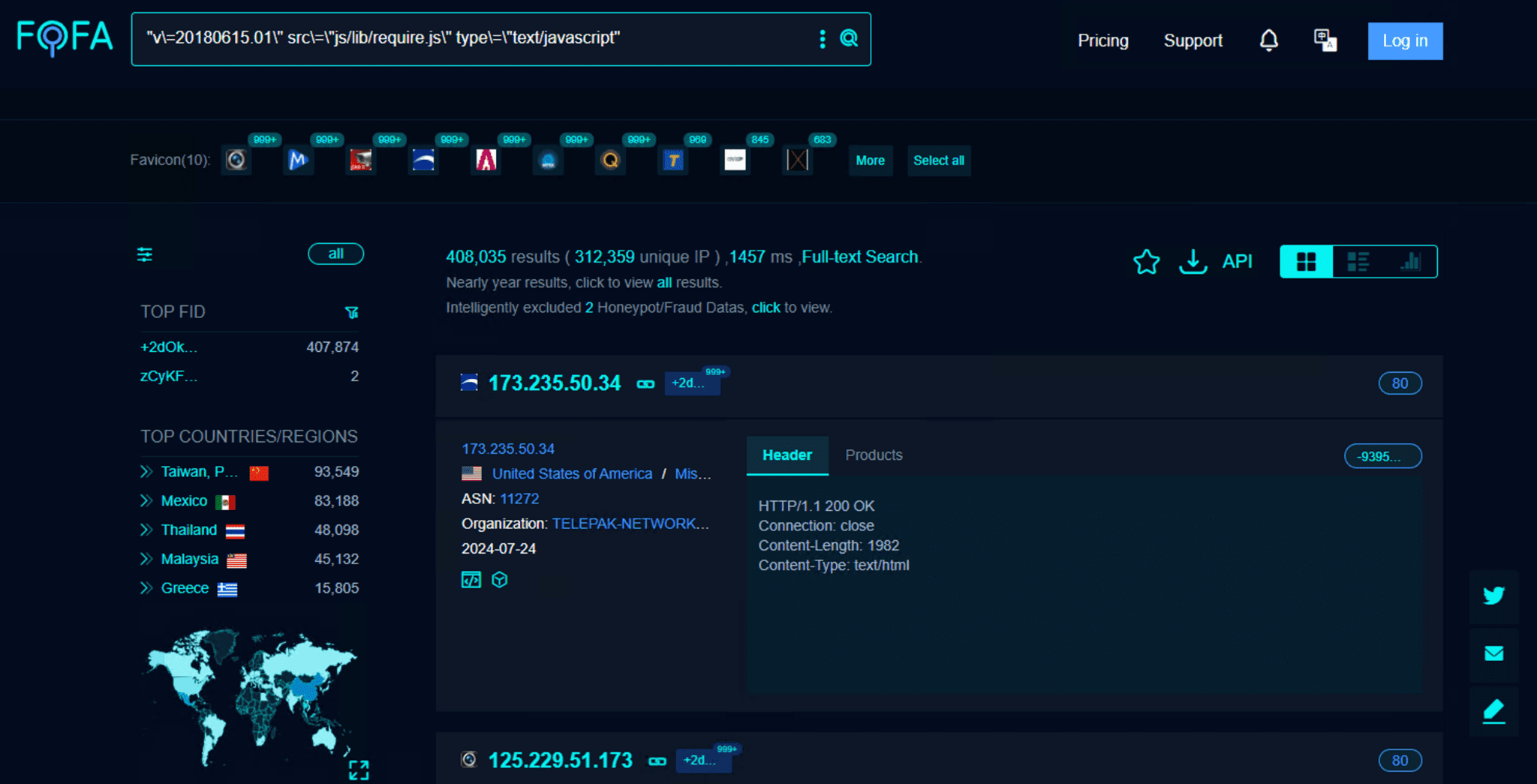
A security flaw tracked as CVE-2024-7339, has been discovered in a wide range of popular DVR (Digital Video Recorder) devices, including models from TVT, Provision-ISR, AVISION, and others. This vulnerability leaves a staggering 408,035 devices exposed to unauthorized access and potential exploitation.
The vulnerability resides in the device’s web server, which suffers from insufficient access controls. This allows attackers to remotely extract sensitive information, including hardware and software versions, serial numbers, and network configurations. Armed with this data, malicious actors could launch further attacks, such as:
- Targeted intrusions: Gaining intimate knowledge of a device’s configuration can help tailor attacks for maximum impact.
- Device takeover: Leveraging exposed vulnerabilities to seize control of the DVR for nefarious purposes.
- Data breaches: Potentially accessing recordings or other sensitive data stored on the DVR.
If you own or manage any of the following DVR models or use software versions listed below, your device is vulnerable:
- Hardware: TVT DVR (TD-2104TS-CL, TD-2108TS-HP), Provision-ISR DVR (SH-4050A5-5L(MM)), AVISION DVR (AV108T), etc.
- Software Versions: 1.3.4.22966B181219.D00.U1(4A21S), 1.3.4.22966B181219.D14.U1(8A41T), 1.3.4.22966B181219.D44.U1(16A82T), 1.3.4.24513B190218.D00.U1(8A21S), 1.3.3.20657B180918.D06.U2(4A41T), 1.3.4.24879B190222.D00.U2(8A21S)
The exploitation process is straightforward, involving a simple POST request to the vulnerable endpoint. An attacker can use the following cURL command to extract device information:
This command sends a crafted XML request to the target DVR, which then returns sensitive information about the device.
What Can You Do?
- Check for updates: Immediately contact your DVR manufacturer or vendor to determine if a patch or firmware update is available to address CVE-2024-7339. Apply any updates promptly.
- Restrict Access: Implement strict access controls and authentication mechanisms to manage access to the device interfaces.
- Secure your network: Implement robust network security practices, such as firewalls and strong passwords, to limit unauthorized access to your devices.
- Monitor for suspicious activity: Keep a close eye on your DVR logs for any unusual behavior, and report any concerns to your security team or the manufacturer.





