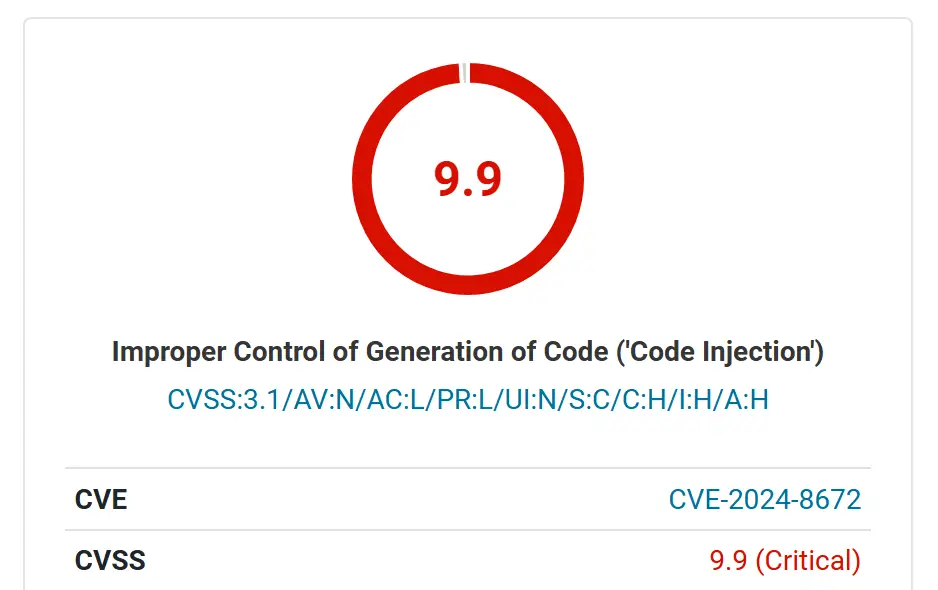
A critical security vulnerability (CVE-2024-8672) in the popular “Widget Options” plugin, which boasts over 100,000 active installations, has been patched in the latest release (version 4.0.8). This vulnerability, assigned a CVSSv3 score of 9.9, posed a significant threat to websites utilizing the plugin, potentially allowing malicious actors with contributor-level access or above to execute arbitrary code on the server.
The Flaw:
The vulnerability stemmed from the plugin’s “display logic” functionality, which extends several page builders. This feature allowed users to input data that was then passed through the eval() function without proper filtering or capability checks. This oversight opened the door for authenticated attackers to inject and execute arbitrary code.
Researcher Recommendation Ignored:
Security researcher Webbernaut, who discovered and reported CVE-2024-8672, recommended that the plugin developers implement an allowlist of permitted functions and restrict command execution to administrators only. Unfortunately, these recommendations were not fully adopted in the patch.
Patch and Residual Risk:
While the latest update (version 4.0.8) addresses the immediate vulnerability, security experts warn that the current patch might not be completely foolproof. The way the issue was resolved could still leave websites with residual risk.
Call to Action:
All users of the “Widget Options” plugin are strongly urged to update to version 4.0.8 immediately. Website administrators should also remain vigilant and monitor their sites for any suspicious activity.
Related Posts:
- PHP Everywhere WordPress Plugin Remote Code Execution Alert
- ServiceNow’s ‘Simple List’: The Vulnerability Jeopardizing Thousands of Companies