Image: GreyNoise
In a recent discovery, GreyNoise Labs identified two critical vulnerabilities in popular pan-tilt-zoom (PTZ) cameras, which could allow unauthorized access and remote code execution (RCE) on devices used globally. These vulnerabilities, CVE-2024-8956 and CVE-2024-8957, were first flagged through GreyNoise’s threat-hunting tool, Sift. Leveraging advanced large language model capabilities, Sift processes millions of daily HTTP events to uncover targeted attack patterns, making it possible to identify these threats amidst background traffic.
GreyNoise described the first vulnerability, CVE-2024-8956 (CVSS 9.1), as a high-severity issue caused by “insufficient authentication” in the firmware of VHD PTZ cameras, impacting multiple white-label brands like PTZOptics and SMTAV. The embedded web server on these cameras allowed access to sensitive device configurations without authentication. GreyNoise noted, “Upon accessing the device with omitted Authorization header, CGI API does not return 401 Unauthorized, and exposes the sensitive information about the camera,” including device model, serial numbers, and MD5 hashes of account passwords like ‘admin’ and ‘guest’.
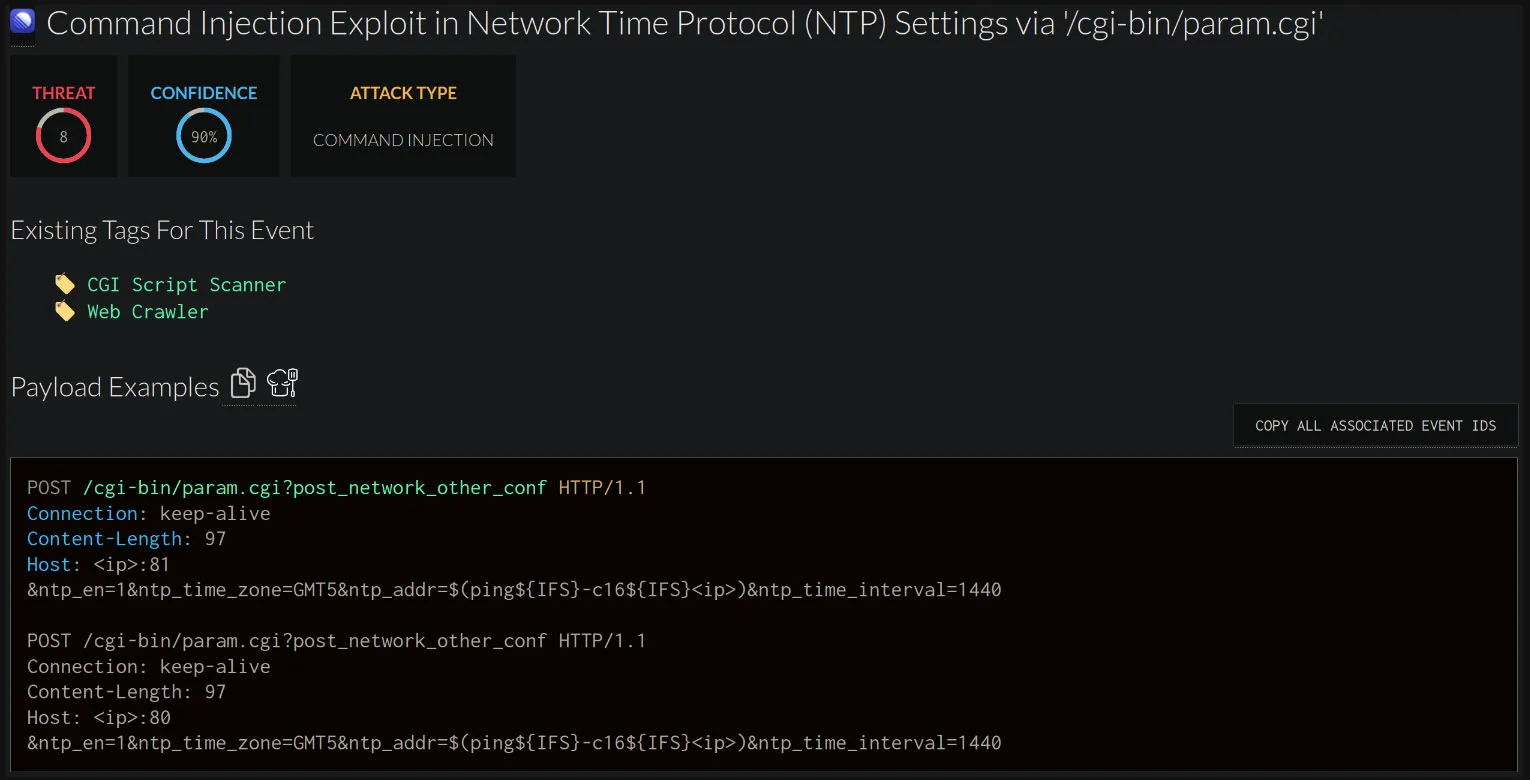
The second vulnerability, CVE-2024-8957 (CVSS 7.2), involves command injection. GreyNoise Labs found that the PTZ camera’s network configuration command could be manipulated to run arbitrary system commands, allowing attackers to gain deeper control over the device. This flaw stems from the camera’s reliance on a ntp_client binary with unsanitized arguments, which could be exploited by a crafted command. GreyNoise simulated the exploit, demonstrating that “passing a system command instead of the NTP server address” allowed the successful execution of unauthorized commands on the camera’s firmware.
The vulnerabilities were initially exploited in April 2024 by threat actors using an IP address flagged by GreyNoise’s sensors. An early attack attempt involved sending payloads that would trigger RCE on exposed cameras. One specific payload example included a “variation attempted using wget to download and run a shell script located at http://209.141.35.56/a,” allowing threat actors to install a reverse shell for continuous access. This IP stayed active for months, even after law enforcement efforts to disrupt the command-and-control (C2) infrastructure linked to the attacks.
In response to these vulnerabilities, GreyNoise Labs collaborated with VulnCheck and researcher Jacob Baines to alert affected vendors and develop disclosure protocols. Camera owners are strongly advised to update their firmware to the latest versions, as the impacted software versions remain exploitable by attackers skilled in leveraging unauthenticated web requests and command injections.
Related Posts:
- GreyNoise Intelligence Uncovers New Internet Noise Storm with Potential China Link and Cryptic “LOVE” Message
- GreyNoise Warns of Active Exploitation Attempts Targeting SolarWinds Serv-U Vulnerability (CVE-2024-28995)
- Hackers are exploiting ownCloud critical vulnerability in the wild
- CVE-2024-8956 (CVSS 9.1): PTZOptics Cameras Vulnerable to Remote Attacks