CVE-2024-9511 (CVSS 9.8): Critical Flaw in FluentSMTP Plugin Exposes Over 300,000 WordPress Sites to Potential Takeover
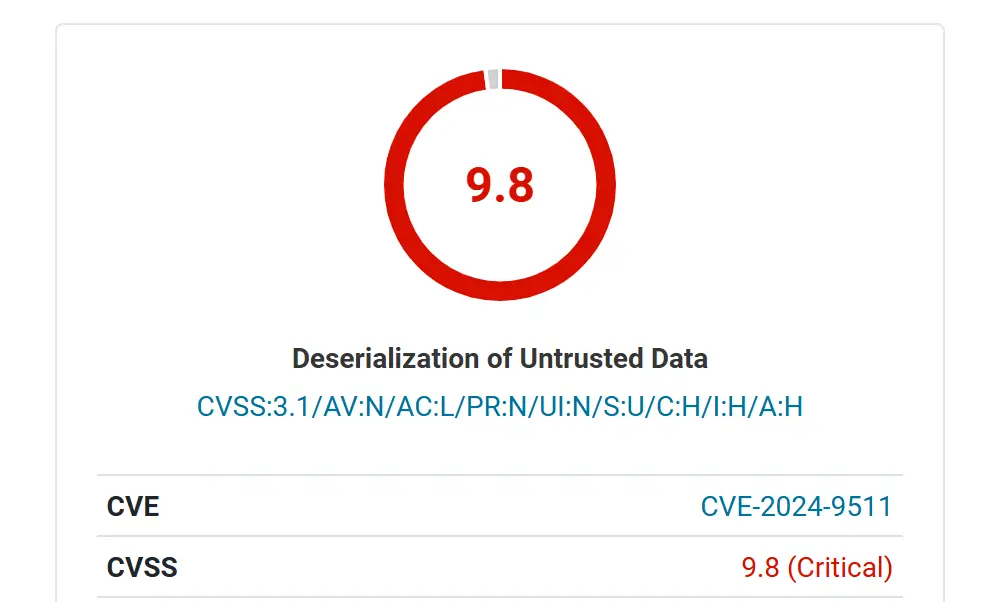
A critical-severity vulnerability has been discovered in FluentSMTP, a widely used WordPress plugin designed to optimize email deliverability. Tracked as CVE-2024-9511 and assigned a CVSS v3.1 score of 9.8, the flaw could allow unauthenticated attackers to execute arbitrary code on vulnerable websites.
FluentSMTP, which boasts over 300,000 active installations, provides seamless integration with popular email service providers such as Amazon SES, SendGrid, Mailgun, and Google. However, a vulnerability in the plugin’s formatResult function enables attackers to exploit PHP Object Injection by manipulating user-supplied data.
This vulnerability arises from the deserialization of untrusted data. While a specific exploit chain has not yet been identified within FluentSMTP itself, the potential for attackers to leverage this flaw in conjunction with vulnerabilities in other plugins or themes poses a significant risk to website integrity and data security.
Successful exploitation could grant attackers the ability to:
- Delete arbitrary files: Compromising critical system files or user data.
- Retrieve sensitive information: Accessing confidential data such as user credentials, financial records, or proprietary information.
- Execute arbitrary code: Taking complete control of the website and underlying server.
Although a partial remediation was implemented in version 2.2.82, website administrators are strongly urged to update to FluentSMTP version 2.2.83 or higher immediately to fully address the vulnerability.
Recommended Mitigation Strategies:
- Prioritize updating FluentSMTP to the latest version.
- Maintain regular updates for all WordPress plugins and themes.
- Enforce strong passwords and enable two-factor authentication for all WordPress user accounts.
- Implement robust website monitoring and logging practices to detect suspicious activities.
- Consider deploying a web application firewall (WAF) to provide an additional layer of protection.
Website owners and administrators are advised to take immediate action to mitigate the risk posed by CVE-2024-9511.





