A critical vulnerability in the popular WordPress plugin, formerly known as Post Grid and now ComboBlocks, has left over 40,000 websites vulnerable to complete takeover.
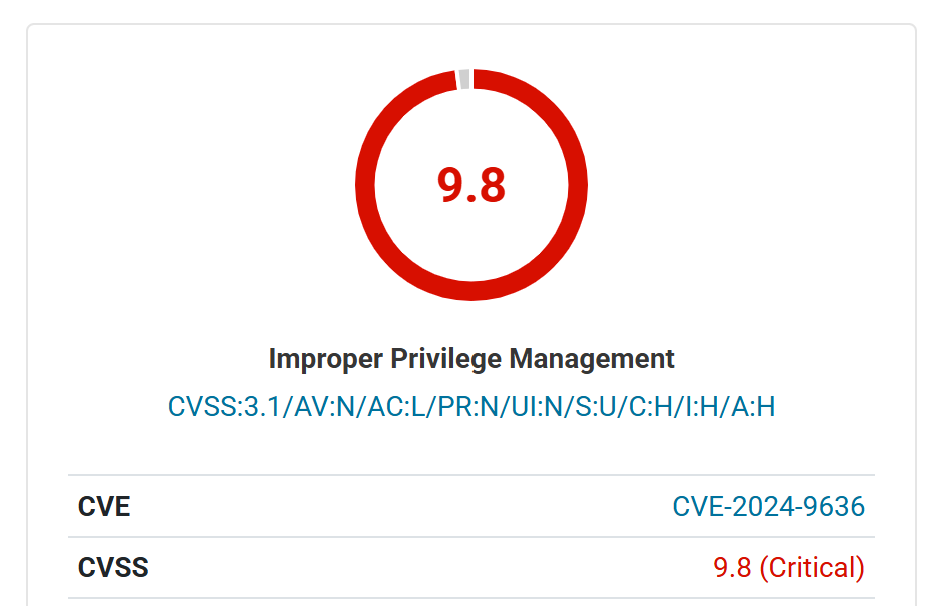
ComboBlocks, a plugin designed to enhance website design and functionality, was found to have a critical security flaw (CVE-2024-9636) that could allow unauthenticated attackers to register as administrators, granting them full control over the affected websites.
The vulnerability, with a CVSS score of 9.8, stems from improper user meta handling during the registration process. This oversight enables attackers to manipulate user data and elevate their privileges to the highest level.
What are the potential consequences?
- Complete website takeover: Attackers can gain full administrative access, allowing them to modify content, steal sensitive data, install malware, and deface the website.
- Data breach: User information, including personal details and login credentials, could be compromised.
- SEO spam: Attackers can inject malicious code to manipulate search engine rankings or redirect visitors to phishing sites.
Who is at risk?
Any website using ComboBlocks (formerly Post Grid and Gutenberg Blocks) versions 2.2.85 to 2.3.3 is vulnerable. With over 40,000 active installations, this represents a significant number of WordPress websites.
What should you do?
Website owners using ComboBlocks are strongly urged to update to the latest patched version (2.3.4) immediately. This update addresses the CVE-2024-9636 vulnerability and mitigates the associated risks.
Related Posts:
- Exploiting Misconfigurations in Argo Workflows for Kubernetes Cluster Takeover
- CVE-2024-43222 (CVSS 9.8): Critical Flaw in Sweet Date WordPress Theme Exposes Thousands of Sites to Potential Takeovers
- Over 15,000 Sites at Risk: Woffice WordPress Theme Vulnerabilities Could Lead to Full Site Takeovers
- CVE-2024-53552 (CVSS 9.8): CrushFTP Flaw Exposes Users to Account Takeover