A high-severity vulnerability has been discovered in Tenda AC7 routers, potentially granting attackers root access to the device. The vulnerability, tracked as CVE-2025-1851, carries a CVSS score of 8.7 and affects firmware versions up to 15.03.06.44.
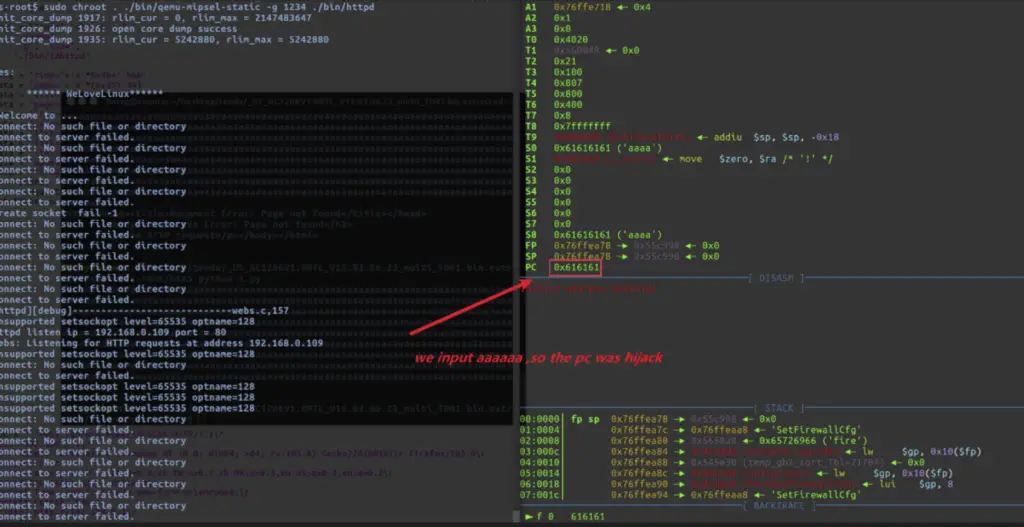
The vulnerability is a stack-based buffer overflow within the formSetFirewallCfg function. A remote attacker can exploit this flaw by sending a specially crafted payload to the router’s web interface. While successful exploitation could lead to a root shell on the device, it appears to require authentication, mitigating the overall impact.
A proof of concept (PoC) exploit is publicly available on GitHub, demonstrating how an attacker can trigger a denial of service by overflowing the firewallEn parameter. The PoC author also suggests that a modified payload could enable an attacker to gain a persistent root shell.
While there is no evidence of active exploitation at the time of writing, Censys has identified over 14,000 exposed Tenda router web login interfaces online. It is important to note that these may not all be Tenda AC7 routers, but the number highlights the potential scale of the issue.
Users of Tenda AC7 routers are strongly advised to update their firmware to the latest version as soon as possible. If an update is not available, consider disabling remote access to the router’s web interface if it is not required.